That’s the question recently posed by founder, podcaster, threat modeling expert and security industry luminary Chris Romeo that sparked online debate and spawned a NowSecure DevSecOps Bunch webinar, “The Great Debate: Does DAST Work for DevSecOps?”
Misconceptions about DAST abound. In reality, organizations need a range of security tools and techniques to safeguard their apps. While many use Static Application Security Testing and pen testing to secure their web and mobile apps, they leave themselves at significant risk without automated continuous dynamic test coverage of their mobile apps that can be fast, efficient and economical. This blog post will cover application security testing types, DAST from a web and mobile perspective and delve into pipeline automation.
Given the high frequency rate of vulnerabilities in mobile apps, it becomes clear that every organization should be using DAST.
AppSec Testing Techniques
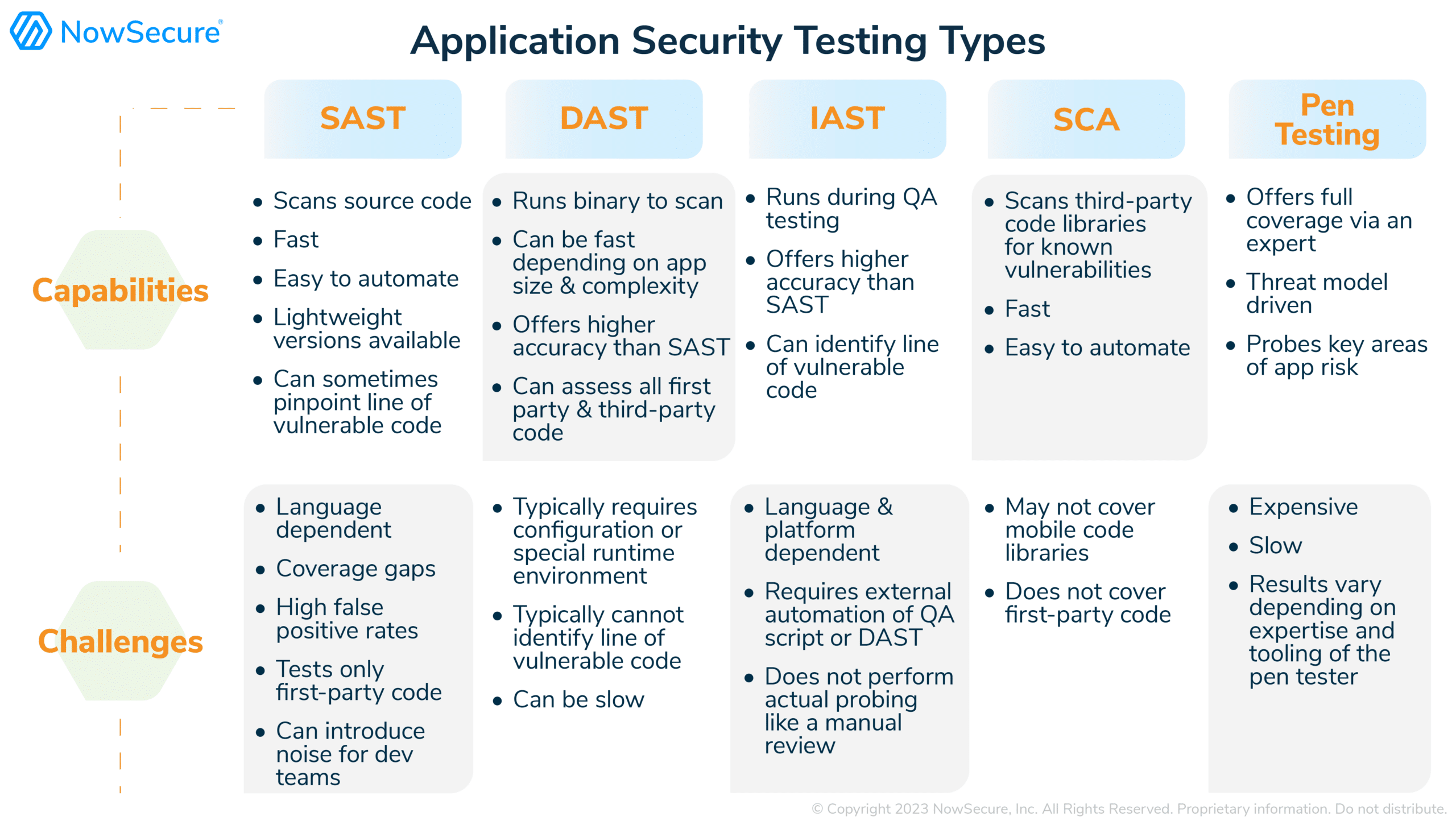
AppSec teams have learned it takes a village of multiple tools and techniques to ensure full security coverage of the apps their devs build. Traditionally teams use a mix of static, dynamic, interactive, and pen testing along with software composition analysis, each optimized for a different part of the problem set. Let’s run through the common suite of security tools, often purchased from multiple vendors.
- Static Application Security Testing (SAST): Static analyzes the source code to identify vulnerable code such as SQL injection attacks, buffer overflows, improper input validation, etc
- Dynamic Application Security Testing (DAST): Dynamic analysis of the running app binary in execution uses various attack scenarios to identify issues such as bad authentication, unencrypted network transmission, insecure storage, SQL injection, etc
- Interactive Application Security Testing (IAST): Interactive analysis injects instrumentation code inside the application to collect security telemetry and identify vulnerabilities
- Software Composition Analysis (SCA): SCA examines third-party libraries and open-source code for known vulnerabilities
- Pen Testing or Pen Testing as a Service (PTaaS): Expert pen testers perform threat modeling and manual dynamic testing using attack scenarios on an application to identify vulnerabilities.
When we look at app security testing for web vs. mobile platforms, the underlying technology and tools differ. Whereas web AppDev and AppSec teams may deploy multiple disparate tools from different vendors to run in different phases of the pipeline process, current state-of-the-art mobile application security testing tools like NowSecure Platform combine SAST, DAST, and IAST in a single tool that runs on the mobile app binary. We will dig into these advantages later.
Speed & Results of AppSec Testing Techniques
DevSecOps enables iterative application development in smaller chunks and accelerated release cycles. The goal is to automate as much security testing as possible and empower devs to do their own security testing as they write code. Like automating QA, the objective is to provide fast feedback loops to speed remediation and release cycles.
So let’s go back and look at the mixed bag of speed, efficiency and accuracy of SAST, DAST, IAST, SCA and pen testing techniques as we try to incorporate security test automation into the mobile dev pipeline.
Accelerating Security Testing in DevSecOps Pipelines
To meet speed and scale requirements, today’s pipelines often use SAST scans on repos and SCA scans on pull requests, such as with security embedded in GitHub Advanced Security or GitHub Actions or security tools integrated with CI/CD pipelines such as Azure DevOps, GitLab, Jenkins or Jira. These are configured to run fast in minutes in order to meet the rapid development and release cycles that businesses often demand. Sometimes periodic pen testing is also performed prior to release but not within the pipeline automation.
So where does this leave DAST for mobile DevSecOps? For many organizations, dynamic application security testing is only performed manually and periodically. A few traditional web-based DAST tools exist, but organizations find them difficult to configure and run. From a performance perspective, web DAST usually requires hours or days to complete. But that’s way too slow for modern fast-moving pipelines that seek security test completion and feedback in minutes. As a result, dev teams often go without frequent dynamic testing, leaving each release at risk with voids in testing coverage. To make up for it, they might manually pen test once or twice a year, but that leaves significant gaps and security risks. Vulnerabilities found in production can lead to data breaches that damage the business.
Mobile AST is different. Automating SAST/DAST/IAST/SCA via an all-in-one approach delivers fast testing results in minutes to keep pace with modern mobile DevSecOps pipelines. How can mobile DAST run fast? It starts with the binary testing approach used by NowSecure Platform. An automation engine drives mobile app security testing on real devices in minutes.
First, NowSecure performs binary SAST analysis, collecting key vulnerability data. Then NowSecure injects IAST test code into the binary, loads the binary onto a real device, and runs DAST analysis. DAST provides “outside in” analysis, while IAST provides “inside out” analysis simultaneously. Depending on the size and complexity of the binary, the combined testing runs in less than 20 minutes in the pipeline, enabling continuous testing of every build every day.
Uniquely combining SAST/DAST/IAST in a single stack overcomes traditional web DAST challenges. For example, NowSecure findings pinpoint code locations, provide detailed evidence for each finding and boast very high accuracy rates with less than 1% false positives.
To help developers speed security bug fixes, NowSecure includes embedded remediation guides with description, business impact, evidence, remediation instructions, links to iOS and Android developer docs and OWASP resources, code samples and regulatory mappings.
For screaming fast pipelines, NowSecure Platform integrates with all major DevOps tools to run fully autonomously including GitHub, GitLab, Jenkins. Jira, Azure DevOps, and more. Organizations can automatically test every build every day and route prioritized, effective tickets to devs for efficient remediation. NowSecure Platform also supports policy-driven development to optimize pipeline performance and efficiency.
And for further dynamic coverage in mobile DevSecOps pipelines, NowSecure Platform Guided Testing offers daily automated testing complemented by a periodic manual review by a NowSecure mobile security expert who will drive the mobile app with specific multi-factor authentication and navigation based on threat modeling and testing needs. This unifies the speed of DevOps and the depth of dynamic analysis.
SAST vs DAST Coverage
You might think that since SAST is easier, just stick with that — get the speed you need and attempt to tune for the noisy false positives. You can try to run without automated DAST in your mobile pipelines — it can’t be that bad to leave some code uncovered by continuous testing in the pipeline, right?
Our live benchmark analysis of thousands of mobile apps in the public app stores shows that 85% or more of mobile apps are vulnerable and over 70% leak private data. When we dig into the vulnerability patterns, we find that the majority of vulnerabilities in these public apps are found via DAST, not SAST. DAST uncovers issues like insecure storage, insecure network data transmission, data leakage into log files, improper use of crypto, lack of anti tampering, to name a few that SAST typically does not find. What’s more, nearly all the vulnerabilities that are CVSS-scored critical and high can only be found accurately via DAST — SAST misses them.
Given the high frequency rate of vulnerabilities in mobile apps — and high CVSS risk scores of these vulnerabilities -— it becomes clear that every organization should be using DAST. And with modern mobile AppSec tools like NowSecure, you can include automated DAST in your mobile DevSecOps pipelines at the speed and scale you need with low cost and high efficiency.