Many organizations have embraced mobile DevSecOps by integrating automated mobile application security throughout the software development lifecycle. Baking security into the development process reduces risk, cuts costs and accelerates delivery of secure, high-quality mobile apps. A policy-based approach enables stakeholders to define and operationalize policy rules to meet internal, industry, app store and other requirements while balancing business, performance and budgetary needs.
The Role of Policies in DevSecOps
The business, security and privacy requirements for mobile apps are complex and ever evolving. Organizations must comply with an array of security standards and guidelines:
- App Store or Google Play requirements such as the latest Apple iOS app privacy details and Google Play safety section requirements.
- OWASP Mobile Application Security Verification Standard (MASVS)
- App Defense Alliance (ADA) Mobile Application Security Assessment (MASA)
- California Consumer Privacy Act (CCPA)
- Global Data Protection Regulation (GDPR)
- Industry-specific regulations like Payment Card Industry (PCI) or the Health Insurance Portability and Accountability Act (HIPAA).
To optimize for pipeline performance and efficiency, many industry leaders have adopted a policy-driven approach to DevSecOps with a release policy in which security and development teams identify and agree up front on a standard set of business, security and privacy compliance requirements that must be met before pushing a mobile app to production. The release policy provides a minimum bar for dev to get an app into production. Automating the release policy gives the security team more time to go deeper and investigate the other findings that require more review. Once operationalized through software automation, this approach speeds up development, testing and release processes, while removing friction, debate and uncertainty.
We often hear from developers: “Just tell us the rules and we will follow them.” Another thing that we hear from developers is: “Don’t waste our time with false positives and things that aren’t critical.” Security and development teams can build a standard set of rules (policies) for which findings in their mobile app must be remediated before the app is pushed to production. Doing so drives consistency and uniformity in security and privacy practices across teams, projects, apps or risk profiles. What’s more, it enables development teams to move faster by knowing where the boundaries are for what issues must be fixed immediately and what issues are acceptable risks. The automated release policy with auditable test data also provides the evidence necessary to attest that proper controls are in place.
Operationalizing Through Policy Automation
Building a standard policy for teams to follow is the first key component of policy-based DevSecOps. The second is operationalizing it. Once teams have the set of requirements relevant to their mobile app, they need training on the security and privacy policy and practices. Then they need a way to integrate that policy check into their mobile AppSec testing process.
Ideally, businesses have fully automated mobile AppSec testing integrated into the CI/CD pipeline. In this seamless process, devs build the mobile app in their CI tool which kicks off a security assessment. Once the tests complete, only the issues that violate the set policy are automatically routed to the development team in the form of tickets on their board. Developers know that these are prioritized, valid “must fix” tickets based on the previously agreed policy in place. In the end, both the development and security teams know that when the policy-driven test results are all green, that is a good thing and they can automatically promote to production.
Developers and security teams can use NowSecure Platform Policy Engine to create custom policies that include relevant risk profiles, customize risk scores, categorize issues into groups and prioritize issues for remediation.
Policy-Based DevSecOps Best Practices
Organizations looking to move into policy-based DevSecOps should consider these best practices:
- Foster Collaboration: DevSecOps is all about breaking down the silos between development and security teams. Encourage collaboration between these teams to jointly define and refine policies. Create regular communication, knowledge sharing and mutual understanding of mobile security requirements. Agree in advance on what is a Release Blocker vs Backlog vs Acceptable Risk.
- Create Comprehensive, Tiered Policies: Create policies that cover the relevant requirements for your mobile app that include business, security and privacy requirements as well as industry standards and compliance requirements. For organizations with many mobile apps where some apps may require more security scrutiny than others, it may be appropriate to create multiple tiered policies based on risk profiles.
- Review and Update Policy Regularly: Review policies periodically to align them with new tests/findings from NowSecure, emerging threats, compliance regulations and lessons learned from security incidents. Update policies accordingly and communicate changes internally to the relevant teams.
- Integrate Security Testing: Embed policy-driven security testing tools into the CI/CD pipeline to help identify security and privacy issues earlier in the development process, where they are easiest and most cost effective to remediate.
Using NowSecure Policy Engine for Policy-Based DevSecOps
NowSecure introduced the NowSecure Platform Policy Engine to enable organizations to seamlessly deploy, automate and enforce standard and custom policies and controls. The use of industry-standard testing, such as OWASP MASVS, demonstrates that NowSecure has the highest quality testing capabilities and makes it easy to provide proof of controls for regulatory and cyber risk compliance.
Security and development teams can use NowSecure Platform Policy Engine to create custom policies that include relevant risk profiles, customize risk scores, categorize issues into groups and prioritize issues for remediation. With a release policy in place, NowSecure automatically tests every mobile app build and then creates and routes tickets to developers to remediate based on the previously agreed-upon release criteria. This capability enables NowSecure to provide the most efficient path to scale policy-driven mobile DevSecOps in a few simple steps.
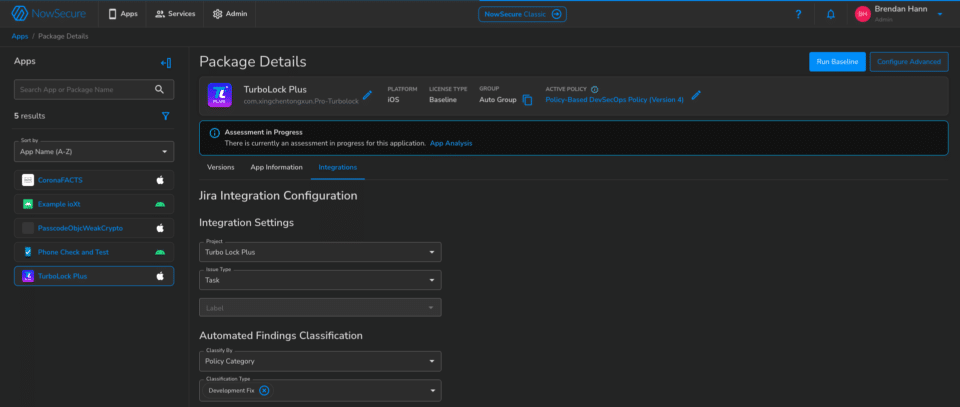
NowSecure automation integrates with many popular dev tools such Azure DevOps, GitHub, GitLab, Jenkins and Jira. For this example, I’ve integrated NowSecure Platform with Jira boards to perform automated mobile AppSec testing after every build and automated ticket routing. Follow along to learn how to use the NowSecure Platform Policy Engine.
1. Create a new integration between NowSecure and Jira. You must be an administrator of both the NowSecure Platform and Jira instance to create a new App Link in your Jira instance. You can find a full guide to creating this integration in the NowSecure Help Center.
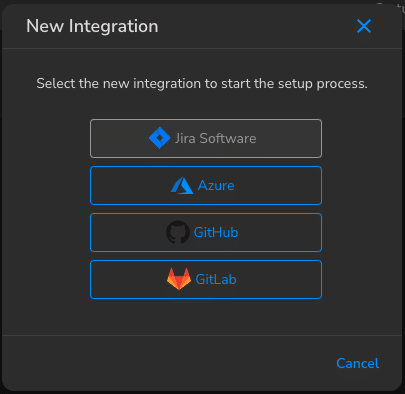
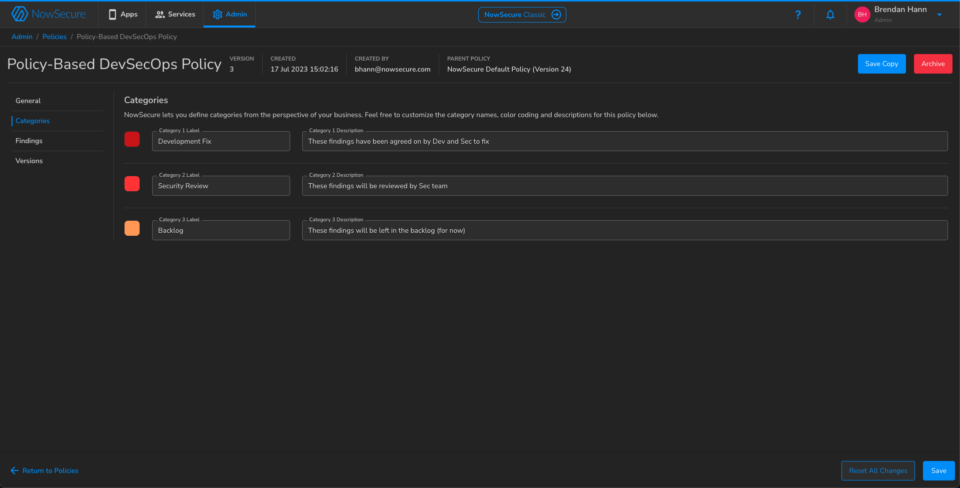
2. The second thing the administrator needs to do is create a custom policy. As described, development and security teams collaborate on this mobile app release policy. The policy will be made up of three categories and you can fully customize which findings are included and excluded from your reports. For this example, I have created the following categories: Development Fix, Security Review and Backlog.
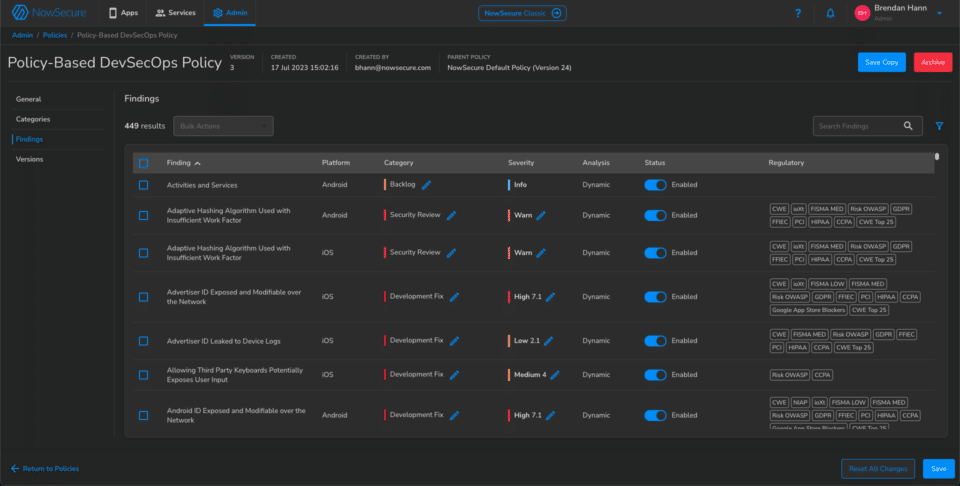
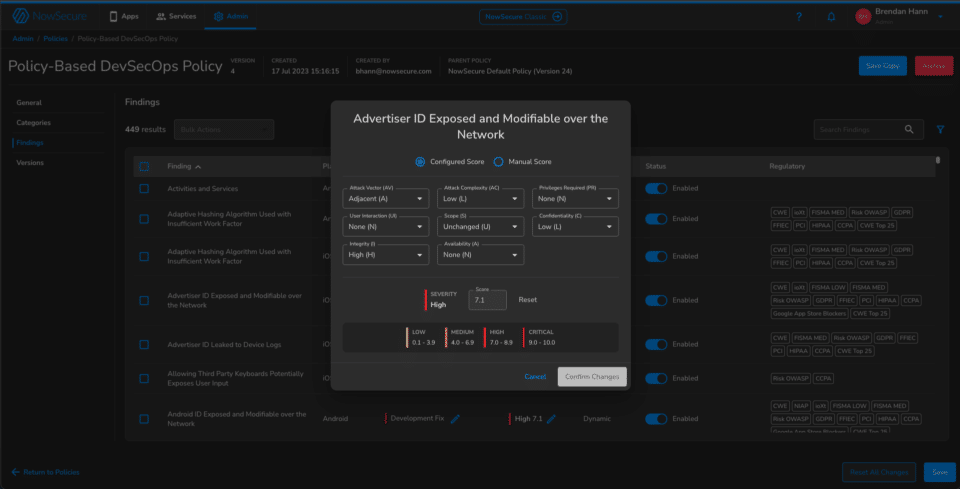
3. Once the policy categories have been created, your teams will have to decide which findings to include in each category. This is where development and security alignment is critical because it should include all relevant industry standards and compliance requirements. The NowSecure Platform Policy Engine makes this easy — all findings are tied to regulatory requirements and filterable. Here, you can also customize the severity of each finding individually, including setting the CVSS score.
4. Finally, you can link the app to the correct board and decide which policy categories create tickets. Notice in this example, the “Development Fix” category is the only category that generates tickets. The intention here is to improve developer productivity by sending them only the items that absolutely require their attention (release blockers), while the security team can review the other findings from mobile application security tests in the NowSecure Platform interface.
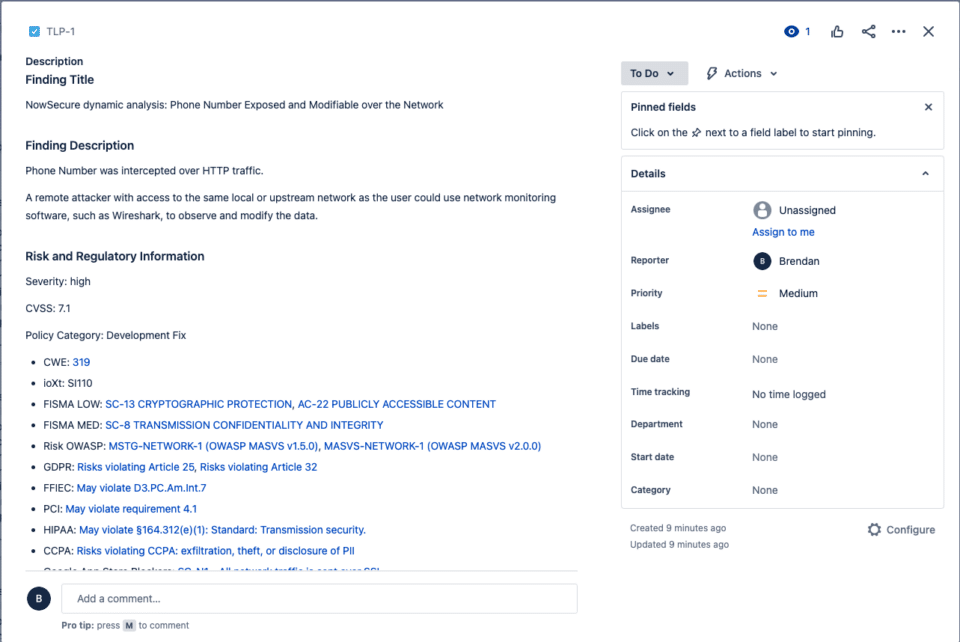
For developers using the board, issue tickets will automatically be created through the integration with the information that you decide is most relevant from the issue found in security testing. You can choose to include the Finding title, description, steps to reproduce, remediation resources, and business impact. Here’s an example of a ticket generated by NowSecure Platform:
You can still view the results of the assessment in the App Analysis section of NowSecure Platform.
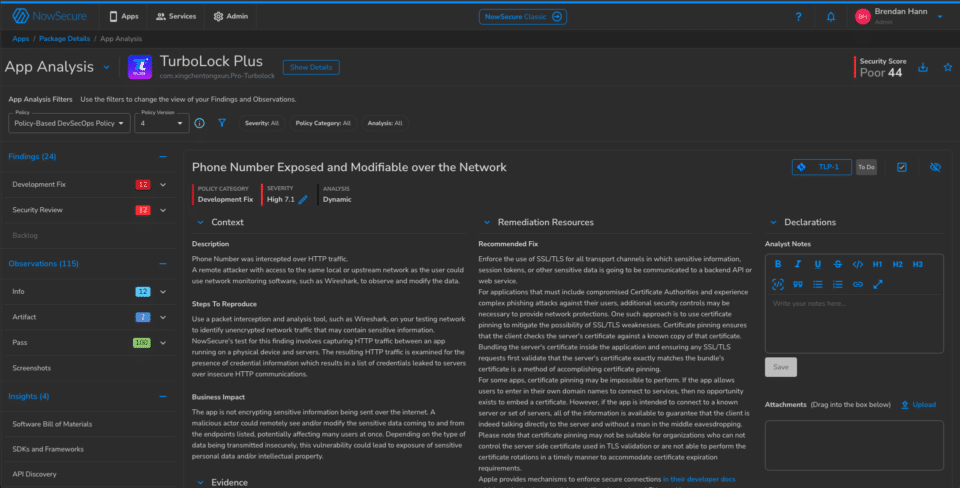
Here, the 12 “Development Fix” findings automatically created tickets which are linked (with the status shown) in the top right of each finding. You can see that this assessment also surfaced 12 “Security Review” findings, which the security team can review along with the informational findings, artifacts, and insights like the generated Software Bill of Materials (SBOM).
How NowSecure Customers Use Policy Engine Today
Many NowSecure customers successfully use NowSecure Platform Policy Engine to customize their results from NowSecure Platform. On average, users create more than two policies, but we’ve seen some customers create as many as nine. Some policy examples include targeted policies like:
- New Default Policy
- [App/Org Name] Release Policy
- App Store Blockers
- HIPAA Tests
- NIAP Tests
- Financial Apps Policy
- Android OWASP MASVS
- iOS OWASP MASVS
- CVSS Critical or High
- Static Tests
- Dynamic Tests
- PCI Policy
NowSecure customers have also set up multiple policies by tier to capture the more strict security testing required for mobile apps depending on the data it collects or the environment it operates in. One customer set up three policies:
- Baseline Policy
- Moderate Security Environment Policy
- High-Risk Security Environment Policy
As reflected in this case study, the Department of Justice uses NowSecure Policy Engine to enforce four different policies throughout the agency.
Conclusion
Policy-based mobile DevSecOps provides a structured approach to integrating business, security and privacy requirements into the mobile SDLC. By creating a standard release policy for mobile app security testing and utilizing NowSecure Platform with Policy Engine, automation and integrations, organizations can accelerate the delivery of mobile apps with confidence. Get a NowSecure Platform demo to see the power of automated mobile application security testing integrated into the dev pipeline.





