Both static and dynamic security testing are essential components of the mobile app software development life cycle (SDLC).
Static Application Security Testing (SAST) tests snippets of source code developers check-in during mobile binary compilation. SAST offers broad coverage, scanning vast amounts of code, then surfacing anything and everything that could be an issue. SAST enables early detection of code quality issues, but it cannot validate whether the issues are real, or whether they are false positives.
Dynamic Application Security Testing (DAST) fully exercises the compiled mobile binary, validating issues by interacting with the app on a real device, like an end user will. As such, DAST is effective at weeding out false positives and surfacing only exploitable vulnerabilities. DAST occurs during quality assurance phase, alongside other essential mobile app SDLC testing components, like UX and feature functionality testing. This enables Security and Development teams to prioritize time more efficiently and deploy fixes before publishing to an app store. Below are a few examples of issues mobile DAST locates, that are not discoverable during code compilation.
- Sensitive unencrypted data in transit
- Sensitive unencrypted data storage
- Man-in-the-Middle (MitM) attack vulnerabilities
- Vulnerabilities introduced by third-party libraries
Sophisticated mobile app programs integrate both SAST and DAST tools within the software development lifecycle to maximize coverage and efficiency. However, it’s not uncommon to find some organizations attempting to use legacy web SAST tools for mobile app security testing, even though mobile app architecture and functionality is fundamentally different than that of web apps. This approach is often taken by organizations newer to mobile app development and who may not yet understand the mobile attack surface.
Long-held misconceptions about DAST, including that it is slow or requires a human to execute, also continue to cause confusion for those new to securing mobile apps. For mobile, slow testing is not an option given mobile app developers are early adopters of Agile and/or DevOps release frameworks and move very quickly. DAST for mobile must be fully automated and integrated within a mobile app SDLC in order to keep pace. Technological advancements and ingenuity have changed the reality of what is possible today with modern mobile DAST tools.
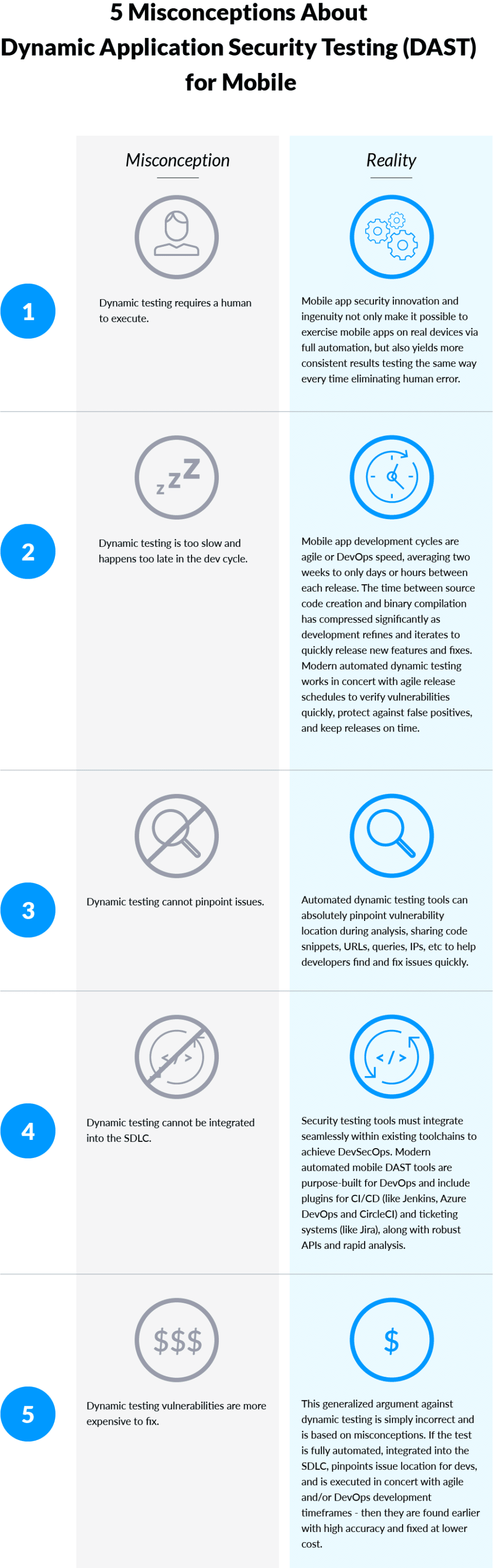
DAST purpose-built for mobile is a vital component of any mobile app security and privacy program. DAST technology continues to advance quickly in order to keep pace with mobile app development. Curious to learn more about leading-edge DAST? Request a demo from a NowSecure mobile app security and privacy expert today.





