Radare
Reverse Engineering Toolkit
Radare is a free, open-source portable reverse engineering toolkit for developers, reverse engineers, and security researchers created and supported by NowSecure researchers.
Portable Reverse Engineering Toolkit for Mobile Apps
Radare is a reverse engineering toolkit used to disassemble, analyze, emulate and debug applications and perform forensics on file systems on any modern operating system.
The Support Behind Radare
Radare was created by NowSecure Researcher Sergi “Pancake” Alvarez and is supported by a large global community of tool makers and security researchers. r2Con is the Radare community annual congress with hundreds of attendees. NowSecure researchers support the Radare community and its ongoing mission. Learn more about Pancake and the history of Radare here and follow Pancake and the RadareOrg on Twitter, watch YouTube and join the Radare community on Telegram or Discord. Access the Radare2 Github Repo or learn more fromthe Official Radare book. In 2017, Frida and Radare were integrated as R2Frida to get the best of both, learn more here.

Radare Powers Testing for Mobile Apps
Radare can be used to reverse iOS and Android mobile app binaries (no source code needed) to understand functionality, visualize data structures, patch programs to uncover new features or fix vulnerabilities, and more. With Radare2, you can assemble and disassemble a large list of CPUs, analyze and emulate code with ESIL, navigate ascii-art control flow graphs, patch binaries, modify code or data, and search for patterns, magic headers, and function signatures.

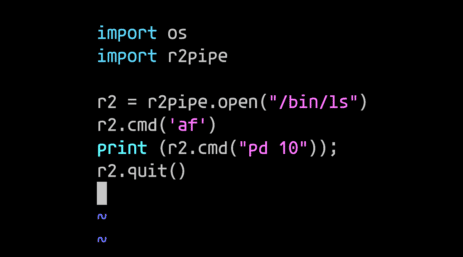
Using Radare
Radare is incredibly flexible and can be used in many ways from command line or shell scripts by calling the individual tools. Users can also take advantage of the integrated package manager to easily install external plugins from different sources including the r2dec decompiler the frida integration, and more. One of the simplest and most effective ways to script radare2 is by utilizing r2pipe. R2pipe is a simple protocol that allows communication with r2 via commands, which enables the scripting of radare2 for virtually every language. Radare can also be used through Radius2, the best theorem solver tool available for mobile apps, and R2ghidra which integrates the native decompiler of Ghidra as a plugin, so it can be used without Java and in batch mode.
Radre Powers NowSecure Solutions
Radare and r2Frida are leveraged across the NowSecure Solution portfolio as part of our blackbox testing capabilities. Radare is used in NowSecure Platform for continuous security testing, NowSecure Workstation for pen tester toolkit, and NowSecure Pen Testing Services, available on demand or through Pen Testing as a Service (PTaaS), for deep expert mobile app analysis.
See Radare In Action with NowSecure
Learn About Automated or Manual Testing