Escalating software supply-chain attacks pose a serious threat to the public sector and organizationes. Adversaries exploit vulnerabilities in third-party code to compromise a supplier to the vast digital ecosystem downstream. The ripple effect causes widespread disruption, financial loss and reputational damage and even endangers national security.
Consider the enormous impact the SolarWinds software supply chain attack had on the private sector and U.S. federal, state and local governments then think of the thousands of web and mobile applications that are under attack. Notable mobile apps that suffered data breaches in 2021 include Apple iMessage, Klarna, ParkMobile, Samsung SecureFolder and Slack.
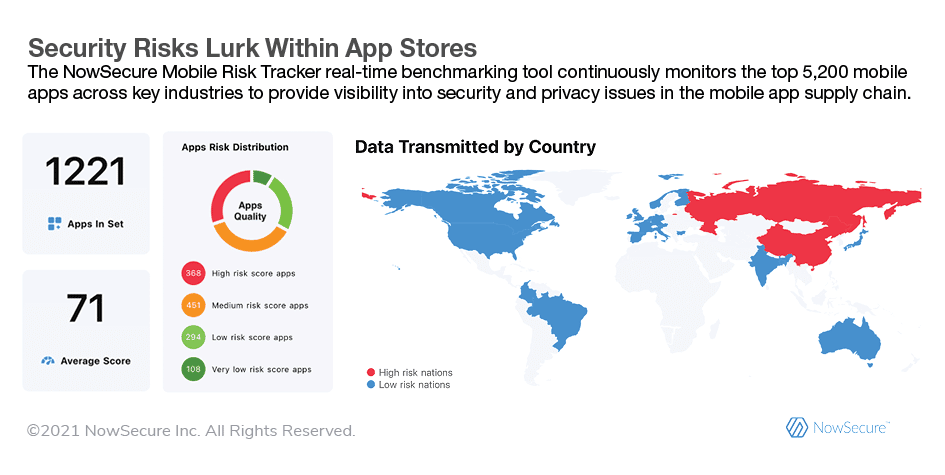
As developers increasingly rely on code libraries and open-source components to quickly build mobile apps and enterprises deploy more third-party apps, the complexity of the software supply chain grows. The Apple App Store™ and Google Play™ house some 6 million apps and don’t include countless other custom mobile apps companies develop in house or obtain from vendors and consultants. That makes for a massive threat landscape in which a single weak link can lead to an attacker infiltrating systems around the globe.
Breaches Unleash Extensive Damage
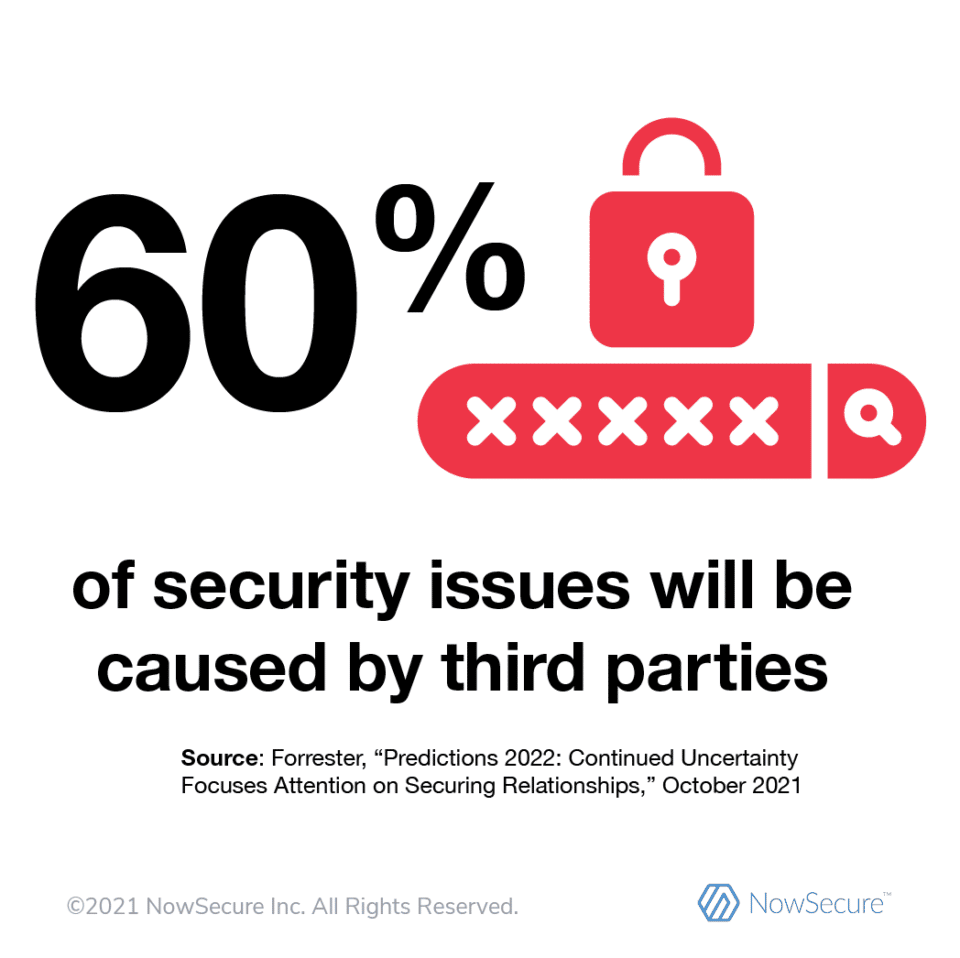
Skyrocketing reports of software supply-chain security incidents demonstrate the struggle to manage software supply-chain risk. The European Union Agency for Cybersecurity (ENISA) estimated a 4x increase in supply-chain attacks in 2021. Sonatype research revealed a 650% increase in next-generation cyberattacks against open-source tools over a one-year period. And Forrester forecasts that 60% of cybersecurity incidents in 2022 will result from issues with third parties.
Software supply-chain attacks have far-reaching impacts and organizations face considerable challenges and expense to remediate them. A CloudBees survey revealed 64% of C-suite executives said it would take more than four days to mitigate a software supply-chain security incident. But some may not even know when their organizationes are attacked. And a BlueVoyant report found more than one-third of leaders have no way of knowing if or when a cybersecurity issue with a third party arises.

U.S. Government Strengthens Cyberdefenses
Alarmed by growing risk to the software supply chain, the U.S. government has acted to fight the threat. In 2021, the White House issued an Executive Order mandating cybersecurity requirements for federal agencies, systems integrators, vendors and contractors. “The United States faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy,” the EO states. “The federal government must take action to rapidly improve the security and integrity of the software supply chain, with a priority on addressing critical software.”
Organizations must rapidly improve the security and integrity of the software supply chain. – White House Executive Order
In addition, the Cybersecurity and Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST) recently offered guidance to the private sector about mitigating software supply-chain risk. And as part of the cybersecurity EO directive, NIST has defined critical software and is updating a set of best practices for secure software delivery and software labeling.
Announcing the World’s First Dynamic Software Bill of Materials (SBOM) for Mobile Apps
Early Access Program Enables Organizations to Access Dynamically Generated SBOMs for Any Mobile App Binary
Safeguard the Mobile App Supply Chain
Security and DevSecOps leaders should adopt cyber supply chain risk management strategies to safeguard their mobile applications from attack. Here are a few initial steps to take.
- Create and maintain a Software Bill of Materials (SBOM) to uncover risks hiding in open-source and third-party components that your development team uses to build mobile apps.
- Ask your software vendors to provide SBOMs and confirmation that their mobile apps are safe to use.
- Gain visibility into your existing mobile app portfolio by conducting an inventory and vetting for security, privacy and compliance issues.
- Perform continuous monitoring to stay on top of new vulnerabilities or dependency changes that introduce security, privacy or compliance risks.
About NowSecure
NowSecure offers a comprehensive suite of automated mobile app security and privacy testing solutions, mobile penetration testing and training services to reduce risk. Trusted by many of the world’s most demanding organizations, NowSecure protects millions of app users across banking, insurance, high tech, retail, healthcare, government, IoT and others. As the recognized expert in mobile app security, NowSecure was recently named a mobile security testing leader by IDC, a DevSecOps transformational leader by Gartner, a Deloitte Technology Fast 500 winner and a TAG Distinguished Vendor.





