Adventures in Remote Code Execution and Zip File Vulns — from Samsung and Vungle to ZipperDown
Posted by Brian Reed NowSecure Marketing
In order to optimize mobile app file size and user installation experience, many mobile app developers turn to downloading zip files with embedded content and functionality. As with all things mobile, there are both secure and insecure ways of downloading and using zipped content. Back in 2014, NowSecure identified and properly disclosed zip file download and remote code execution (RCE) vulnerabilities on Android for Samsung and Vungle. Now Pangu has posted about iOS zipfile download issues identified as ZipperDown.
What’s the issue?
Downloading a zip file from a server then unzipping on the mobile device, if done insecurely, can allow an attacker to swap files in transit and deliver a malicious payload. Depending what the mobile app does and what permissions it has, this can be a high impact or low impact risk. This category of issues has been around since the dawn of mobile app development.
In the ZipperDown scenario, the attacker and mobile app needs to be on the same wifi network or an attacker must be able to influence upstream network resources, i.e., a man-in-the-middle (MITM) attack. The ZipperDown vulnerability focuses on mobile apps specifically using ZipArchive where all of the following conditions must exist: the data transmission, the zip package and the local scripts are NOT encrypted. Under these narrow conditions, the attacker can inject a new payload that could enable remote code execution leading to malicious activity.
From the ZipperDown post, Pangu says they have only identified the potential to have the Zip RCE issue and have not verified actual vulnerabilities in all the apps they list. Rather they have scanned a number of apps with static string matching to see if they do use downloadable zip files. While there are some major apps named, most of the identified apps are games and content apps, many are old and no longer downloadable.
History of Mobile Zip download & RCE vulns
Back in 2014, the NowSecure Research team identified zipfile download vulnerabilities that enabled remote code execution (RCE) on Android and responsibly disclosed with app developers and device manufacturers, then released public disclosure in 2015.
NowSecure identified and then in June 2015 disclosed “Research Remote Code Execution as System User on Samsung Phones” with POC posted here and video here.
- Summary: A remote attacker capable of controlling a user’s network traffic could manipulate the keyboard update mechanism on Samsung phones and execute code as a privileged (system) user on the target’s phone. These vulns were resolved and closed.
- The vulnerability has been assigned the following CVEUs by CERT: CVE-2015-4640 and CVE-2015-4641.
NowSecure Identified and then again in June 2015 disclosed “A Pattern for Remote Code Execution using Arbitrary File Writes and MultiDex Applications” with video posted here.
- Summary: This issue shows vulnerabilities that allow attackers to execute code remotely on a Android user’s device through applications which contain both an arbitrary file write and multiple dex files using Vungle ad library. These vulns were resolved and closed.
NowSecure has numerous checks in our automated test engine to identify potential critical vulnerabilities. NowSecure includes checks for zipfile in transit, secure communications, and writable executable files in NowSecure Workstation for security analyst deep testing, NowSecure AUTO for rapid testing in Dev pipeline and NowSecure Platform for 3rd party apps. The NowSecure Services team pen testing program can identify these issues as well.
Sample NowSecure findings are shown below. First a test that passed, then a test that failed with the vuln finding and finally an example of a very vulnerable app.
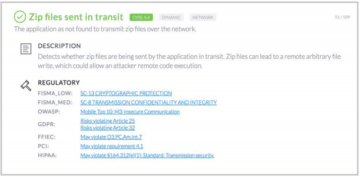
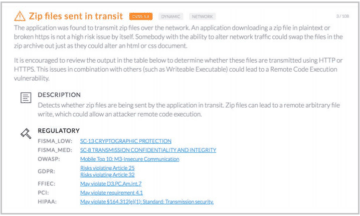
For a deeper example, below is NowSecure Platform test results of a 3rd party app that has a verified exploitable vulnerability due to wide variety of security gaps detected by our automated testing that includes multiple bad findings: writable executable, Zip files in transit, world writable files, world readable files, dynamic code loading and unencrypted data in transit and no code obfuscation.
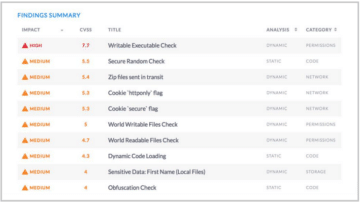
Developer and AppSec Recommendations
Frankly this zip file download problem can be a fairly typical dev error and is not limited to just Zip files but any archival container. Directory traversal vulnerabilities in Zip formats have been explored in the security research community for many years.
Suggestions for dev and security teams:
- Always use secure communications via TLS.
- Avoid downloading executable code over the network. With proper mobile app architecture, downloading of executable code should not be necessary. If you need to update your app, pushing a new version of your mobile app will provide a much safer approach.
- If your app must download content that will be executed, once again be certain to use secure communications via TLS. In addition, on android don’t temporarily store the data on the SD Card. Always store the content in the protected app data directory.
- If you download archive formats (e.g. zip archives), always ensure you safely extract the archive contents to avoid issues such as zip traversal attacks.
- Continuously test your mobile apps for security and privacy issues.
Best Practices Reminder
This recent identification of mobile apps with Zip download vulnerabilities reminds us once again that all dev organizations need to ensure secure development training and best practices are followed. NowSecure offers a free secure mobile app development best practices guide that you can leverage across your organization.
In addition, all organizations should have in place a program for continuous mobile app security testing for 1st party internally developed apps and continuous monitoring of security risks in 3rd party public apps. If you are concerned about the mobile apps you use, we recommend you sign up for a free NowSecure mobile app scan.





