Vastly outnumbered by developers, mobile application security analysts often face challenges in creating a security-first culture. Many have found success by launching security champion programs to amplify and scale security throughout their organizations. Identifying security advocates within the development team promotes security by design practices and reduces vulnerabilities.
Mature appsec programs have a 1:50 ratio between full-time appsec staff and developers, according to the Application Security Champions Report from Coalfire. At HCL Software, 3,500 developers organized in teams build the company’s 150 apps with support from around a dozen dedicated application security professionals. “Governing security of these applications is a huge undertaking,” says Bryan Batty, global director of product security for HCL Software. “You need help throughout the business.”
Last year, Batty launched a security champion initiative to forge stronger security practices and governance throughout HCL Software. A security champion program delivers many benefits:
- Improve product security
- Form key partnerships
- Foster collaboration
- Compensate for lack of budget and headcount
- Develop best practices
- Provide a communications channel
Speaking at the annual NowSecure Connect user conference earlier this year, Batty shared best practices for standing up and maturing a mobile application security champions program. What follows is advice from him and fellow appsec veterans about establishing or growing a security advocacy initiative in your organization.
Establish the Foundation
Batty based the HCL Software program on the OWASP Software Assurance Maturity Model (SAMM). He estimated it takes roughly six months to a year to get a security champions program off the ground. However, he noted there’s no finish line and recommended striving for continuous improvement. Batty referred to the Coalfire report mentioned above which outlines five levels of appsec champions program maturity — Level 1: Emerging to Level 5: Optimizing. He suggested defining the specific criteria for each level depending on your organization’s needs. “For example, Level 3 has what goals to get there and achieve it?,” Batty asked.

Building the foundation entails obtaining CISO sponsorship and executive buy-in. At this stage, security leaders will also need to identify potential advocates and tap them to join the initiative. Batty recommended looking for people in the dev groups who have an interest or skill for application security. “Make sure your champions understand how to give an elevator pitch on the risk presented by a given vulnerability or policy violation,” advises Aaron Rein, cybersecurity lead for AT&T.
Preparing for launch also requires generating excitement and establishing clear expectations for appsec allies. Be upfront about what you want them to contribute and how they will participate as well as the time commitment participation entails.
Izar Tarandach, a principal security architect for Squarespace, emphasized the importance of defining the role of participants. “If you have people who know the product and are knowledgeable enough about security then by all means bring them into the appsec team,” he said. “Don’t put them in the untenable position of having a foot on each team and not being able to fully execute on either.” Instead, he advised taking a more limited approach of tapping people who the security team knows others can rely on to get information and data, but who are not expected to act as security advisors or subject-matter experts.
Batty also advised to establish the cadence of meetings and create an informal communication channel for team discussions, such as Slack or Microsoft Teams. At HCL Software, security champions meet once a month early in the morning to straddle the various time zones of participants based on the East Coast, West Coast and in India.
“We are not in business for security, we are in business for business.” – Bryan Batty, Global Director of Product Security, HCL Software
Reward Good Behavior
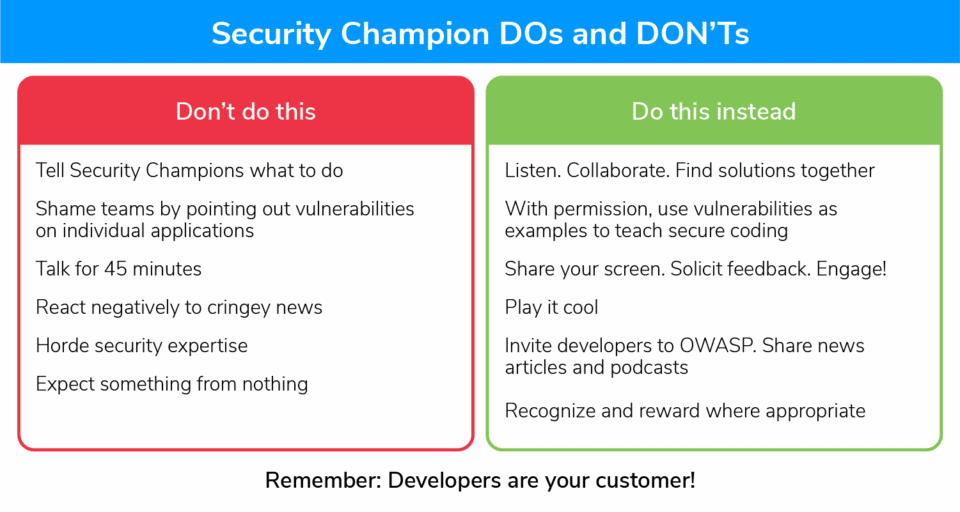
Once you launch a security champions program, the next step is engagement. Batty emphasized the need to collaborate with developers and find new ways of interacting with them. That might mean sharing a recent news article or your favorite security podcast to prompt a discussion or inviting security champions to join you at a local OWASP event. Solicit feedback and collaborate to find solutions.
Greg Nickisch of Advantus Federal suggested opening an in-house bug bounty program for devs. “Even if they start gaming the system by planting known problems only for them to ‘fix’ those same problems, it’s still a win for the enterprise moving forward with general DevSec awareness,” he pointed out.
David Lush, a mobile security lead at Scotiabank, shared the need to recognize strong development leaders and their teams and cooperate to share efforts. Don’t underestimate the power of recognition and rewards to incentivize participation.
Moving forward, Batty will include a budget for the security champions program for rewards such as gift cards, sending top contributors to a security conference, or other form of mobile appsec training. However, many forms of appreciation are free. Gather up some corporate swag and stickers to share with participants, give them security books or point them to free secure coding training. And as Batty noted, “It costs nothing but time to send an email to each security champion’s manager recognizing their achievements.”
Tanya Janca, founder and CEO of We Hack Purple Academy, emphasized the importance of recognition and rewards to a security champion program in a DevSecCon talk. “We want them to know that they are doing a good job and we don’t want them to feel like they are doing two jobs and they only get one paycheck,” she said.
“Giving them your time and attention is a reward,” Janca said. She suggested recognizing people in front of their peers at an all-staff meeting, placing a star next to their name in Slack, making a certificate, putting a note in their performance review, and sending an email and telling the developers’ bosses every time they do something that makes a difference.
Measure Success
Once the security champion program has been running for a few months, do what you can to gauge success. Batty examines both indirect and direct effectiveness.
Quantifiable metrics that indicate whether the security champions program contribute to reducing risk include improvements in mean time to remediate (MTTR), weighted risk trend (WRT) and adherence to SLAs. Metrics you can prove are a direct result of the security champions program include incident response time, instances of a specific bug class, number of times a security champion has been the source of a security issue and OWASP SAMM scoring trend.
At HCL Software, program accomplishments include OWASP SAMM assessments, threat modeling and development of application security incident response playbooks for zero-day vulnerabilities such as Log4Shell and Spring4Shell.
Above all, security champion programs can aid considerably in bridging the dev/security gap and advocating for mobile application security throughout the organization. “Always remember, developers are your customer,” said Batty. “We are not in business for security, we are in business for business.”
NowSecure Academy offers free training to upskill developers and other stakeholders about mobile application security as well as paid certificate programs for mobile application security analysts and developers. Check out the range of courses available today.





