2020 has been a difficult year for many. While none of us could have foreseen all the events that occurred, high-profile mobile app security breaches and data loss were no surprise to NowSecure experts who predicted an intensified focus on privacy in 2020.
Globally, time spent on mobile continues to rise and accounts for 79% of total digital minutes, according to the Comscore 2020 Global State of Mobile report. And in Q2 2020, time spent in mobile apps soared by 40% year over year in part due to the pandemic, App Annie reported. In addition, the pandemic has dramatically accelerated mobile digital transformation. Mobile apps have driven a surge of traffic in key segments such as retail, banking and finance and mobile telehealth.
Mobile Risk Tracker
New NowSecure MobileRiskTracker™ – A Game Changer with Live Industry AppSec Scores
2020 Cyberattacks Target Multiple Industries
This year, few if any industries were immune to mobile application security threats that put customer data at risk and jeopardized revenue and brand reputation. Exploits and attempted attacks on mobile banking apps became so prevalent that the FBI in June warned consumers to be careful about downloading apps.
Our automated mobile application security testing findings and the manual mobile app penetration testing we perform for clients indicate that mobile app security vulnerabilities, privacy issues and compliance gaps are all too common. NowSecure security and privacy benchmark assessments show that 85% of public app store apps have cybersecurity issues and 70% leak private data.
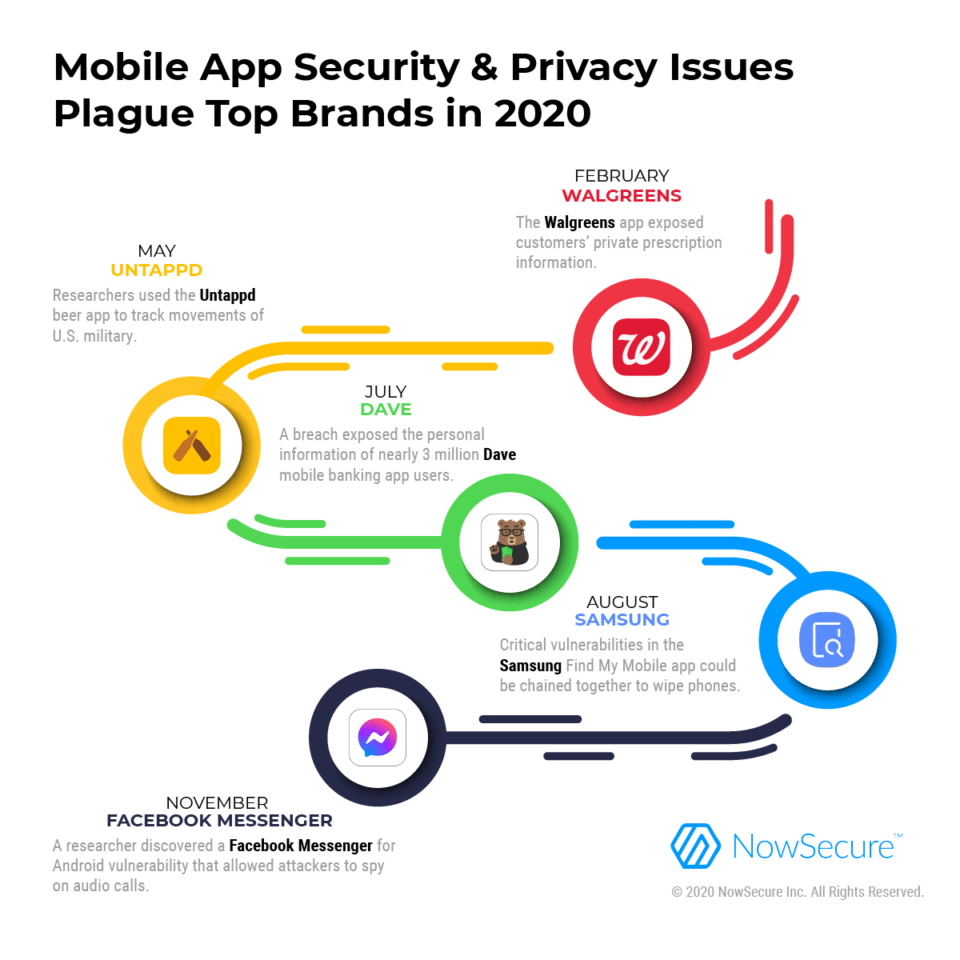
What follows are five noteworthy mobile app security and privacy issues in 2020 stemming from a vulnerability, breach or data leak:
- Walgreens: The pharmacy giant reported in February that an internal security error in its flagship mobile app’s messaging feature exposed customer names, shipping addresses, names of drugs they had been prescribed, prescription numbers, and store number fulfilling the order. The data exposure occurred between January 9, 2020 and January 15, 2020. Walgreens fixed the bug that week, promised to carry out additional testing in the future, filed a breach report with the California Department of Justice and notified customers.
- Untappd: Researchers in May revealed they were able to follow the movements of U.S. military and intelligence personnel through the social networking app Untappd. The app allows beer fans to check in at various locations, post photos of beer and rate the beverages which unintentionally could put them at risk and pose a security threat. For example, researchers used location tracking and other public data from the app to discover sensitive data such as the location of covert training facilities, homes and identities of officials’ family members. Untappd responded by educating users about how to set their profiles to private and encouraged smart data usage.
- Dave: In July, the mobile-only banking app Dave disclosed that a third-party breach exposed the personal information of nearly 3 million users that landed on the darkweb. An attacker who accessed the analytics platform of Dave’s former service provider Waydev to steal personal information such as names, emails, birth dates, physical addresses and phone numbers. In response, Dave launched a manual security code review to identify and fix flaws in its code base, prompted customers to reset their passwords and offered customers identity theft resolution services through 2021.
- Samsung: Researchers from Char49 revealed at DEFCON in August that four critical vulnerabilities in the Samsung Find My Mobile app would have enabled an attacker to chain them together in a man-in-the-middle (MiTM) attack to factory reset Galaxy S7, S8 and S9 phones, resulting in complete data loss. In addition, the vulnerabilities enabled attackers to track users’ real-time locations, monitor phone calls and messages, and lock users out of their phones. Samsung learned of the security flaws in February 2019 and fixed them later that year, but the issues weren’t made public until August 2020.
- Facebook: In October, a Google Project Zero security Researcher Natalie Silvanovich discovered a Facebook Messenger for Android vulnerability that could have allowed a sophisticated attacker to listen to calls without permission. Facebook fixed the bug in November and awarded a $60,000 bug bounty to reflect its maximum potential impact. Also in October, a vulnerability in the download feature of the Facebook Android app could have allowed remote code execution. The company mitigated the path traversal flaw and awarded a $10,000 bug bounty.
How to Reduce Mobile Application Security Risk
Incidents like the ones above can easily happen when developers don’t adopt secure coding practices and organizations fail to conduct comprehensive mobile application security testing to uncover security vulnerabilities and gaps. See the NowSecure ebook, Building Privacy by Design Into Your Mobile App Portfolio, for useful advice about how developers can better protect sensitive information. In addition, get a demo of NowSecure Platform to see how the automated mobile application security testing tool delivers fast, accurate and efficient results that enable development and security teams to fix bugs and remediate vulns before releasing apps.