CVSS scores for mobile apps: Guidelines for measuring mobile risk
Posted by Keith Mokris NowSecure Marketing
At NowSecure, we believe in referencing open-source standards and industry guidelines when evaluating mobile risk. With the ever-changing mobile landscape, we believe these guidelines offer incredible benefit to security leaders when identifying and prioritizing the remediation of code defects and vulnerabilities as well as tracking metrics to show company leadership. Industry-standard guidelines create the framework for our reporting and serve as powerful guides for our team when we add new vulnerability tests and code checks.
We constantly update our Secure Mobile Development Best Practices to help developers avoid mobile app security mistakes, and recently explained the OWASP MASVS Risks. While the OWASP MASVS is a powerful list, CVSS provides another method for risk prioritization.
What is CVSS?
Developed by the Forum for Incident Response and Security Teams (FIRST), the Common Vulnerability Scoring System (CVSS) is a universal open and standardized method for rating IT vulnerabilities and determining the urgency of response. This CVSS value, which ranges from zero to 10, helps security analysts prioritize risk as they look to identify and fix vulnerabilities. As teams look for mobile app security testing solutions that can pinpoint mobile flaws and vulnerabilities, they also want a way to measure the risk associated with those flaws and vulnerabilities — CVSS does just that.
What’s included in CVSS and how does that impact a score?
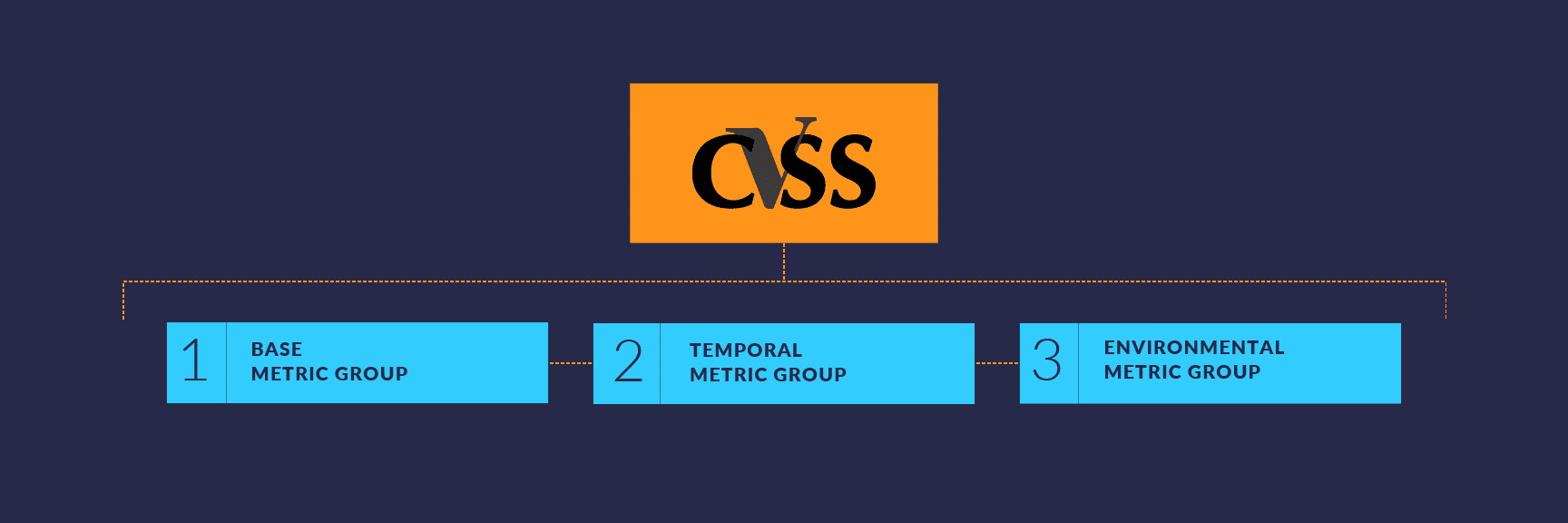
More than a dozen criteria sorted into three specific groups calculate a vulnerability’s CVSS score:
- Base metric group refers to aspects of a vulnerability that remain constant over time across all environments
- Temporal metric group reflects vulnerability characteristics that may change over time but not among user environments
- Environmental metric group takes into account the Base and Temporal metrics, but then applies those to the specific implementation (which will vary) of the vulnerable technology. Later versions of CVSS also refer to Environmental metrics as Modified Base metrics. The more severe a potential attack the higher the score for that organization.
The Base metric group
This post will focus on the Base metric group because it is the universal foundation of CVSS scoring. Values for the the group remain constant over time and across environments because they do not change based on Temporal or Environmental factors.
The Base group includes Exploitability Metrics and Impact Metrics. Exploitability Metrics quantify how a vulnerability can be exploited and the difficulty of exploiting it. Impact Metrics quantify the consequences of successfully exploiting the vulnerability.
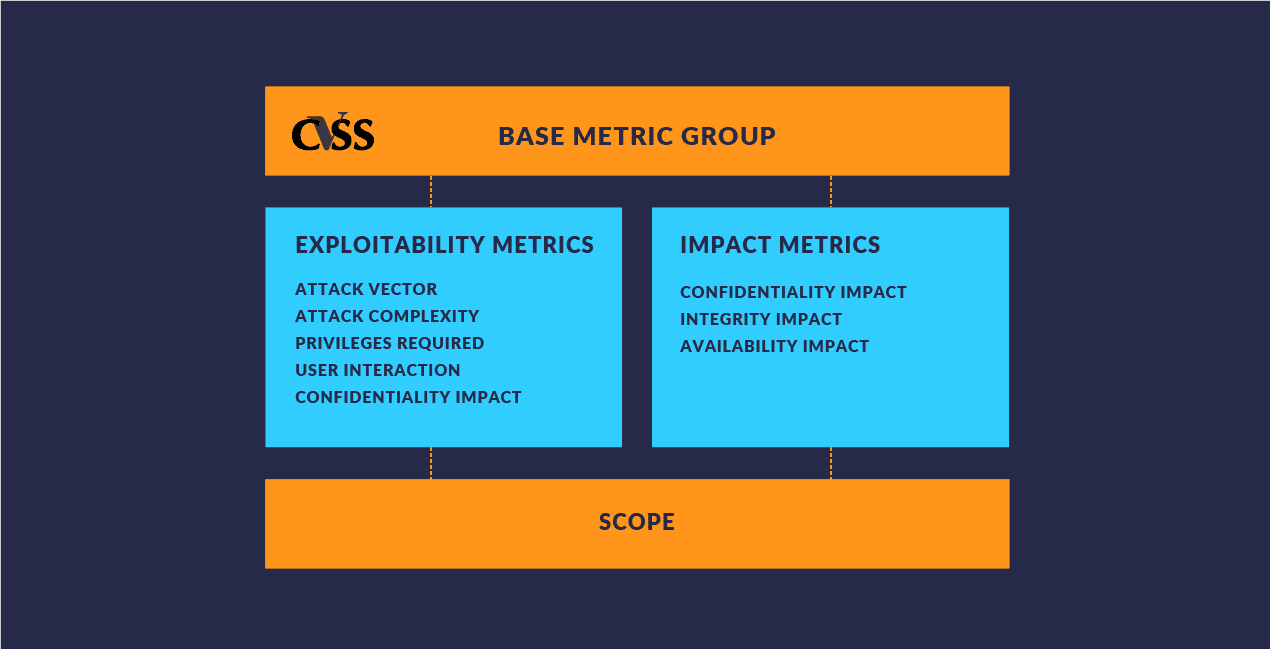
Attack Vector
Attack Vector reflects the “remoteness” of an attack. Generally, the further away an attacker is when compromising your app, device, or network, the higher your base score will be. This criterion also differentiates between local attacks and physical attacks. For example, CVSS accounts for whether an attacker needs to physically touch the vulnerable piece of technology to exploit the vulnerability, trick a user into installing malware, or have a user offload files via USB stick, and more.
Attack Complexity
Attack Complexity refers to conditions outside of the attacker’s control that might affect the exploitation of a vulnerability. Social engineering, the means of collecting information about a user or target or tricking that user into divulging information about themselves, may play an important role in the complexity of an attack.
Privileges Required
Privileges Required refers to the level of access required for a successful attack. The lower the leverage of privileges required to exploit a vulnerability, the easier it can be to carry out an exploit and therefore the higher the score.
User Interaction
This metric measures how much user interaction is required to pull off a successful exploit. For example, some exploits require a user to install a mobile app or certificate to their device. The less user interaction necessary, the higher the score.
Confidentiality Impact
Confidentiality Impact refers to how much information is lost due to a vulnerability. When an attack is executed, this metric measures how much actual information can be obtained from a specific vulnerability. For example, gaining an administrator’s password, which would result in greater access to confidential information, would yield a higher score.
Integrity Impact
FIRST defines integrity as the “trustworthiness and veracity of information,” so this aspect of the score quantifies an attacker’s ability to alter that data.
Availability Impact
Availability refers to system resources or other components impacted by a successful attack. If exploiting a vulnerability can lead to an IT asset or service being made unavailable, it would receive a higher score in this area.
Scope
Scope refers for the possibility of a vulnerability impacting greater resources throughout a compromised organization. Generally, vulnerabilities that have the ability to escalate privileges receive higher scores because they potentially increase the scope of a compromise.
How we use CVSS at NowSecure
In all of our reports, we reference CVSS scores whenever a vulnerability or defect is identified. These scores allow us to quickly and independently prioritize and rate findings across products and services. For example, a security analyst on our services team will use these guidelines performing penetration tests on an app and score results just like our products would. This allows users to easily compare findings from multiple sources, prioritize which risks they want to fix first, and quantitatively report back to company leadership about reducing risk.

CVSS scores are used to sort results into three key risk levels: Low, Medium, and High. Security teams can then fix the High Risk flaws first to maximize their initial remediation work. Then, they can focus on fixing the Medium and Low Risk flaws.
In our free Evaluation Guide for Mobile App Security Testing, we highlight the ways enterprises can benefit from using industry-standard guidelines like CVSS in reporting, and also in measuring return-on-investment for mobile security solutions.





