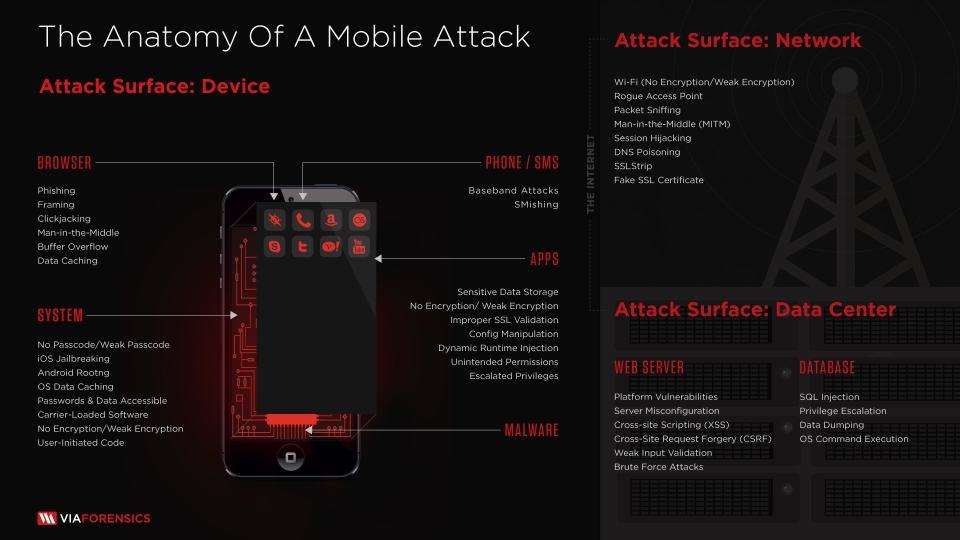
As illustrated below, a mobile attack can involve the device layer, the network layer, the data center, or a combination of these. Inherent platform vulnerabilities and social engineering continue to pose major opportunities for cyber thieves and thus significant challenges for those looking protect user data.
There are three points in the mobile technology chain where malicious parties may exploit vulnerabilities to launch malicious attacks:
- The device
- The network
- The data center