Mobile security standards from the Open Web Application Security Project (OWASP) help align mobile application security analysts and mobile app developers’ expectations about what needs to be remediated prior to release. Standards drive consistency, repeatability and speed.
NowSecure has long embraced the value of mobile security standards built by industry experts and validated by the open-source community. The company supports the work of OWASP in many ways and recently announced full support for OWASP Mobile Application Security Verification Standard (MASVS) V2. Organizations can tap a mix of automated mobile application security testing, Mobile Pen Testing as a Service (PTaaS) and in-depth mobile app security training to meet OWASP MASVS requirements.
Perhaps nobody knows OWASP MASVS better than one of our own, NowSecure Mobile Security Research Engineer Carlos Holguera. The co-leader of the OWASP Mobile Application Security (MAS) Project joined NowSecure in 2021 and works full time to advance the organization’s important work. Holguera recently spoke with us about the exciting developments the OWASP community can expect to see in 2023.
Q: What is the OWASP Mobile Application Security Project?
A: The OWASP MAS project sets the industry standard for mobile app security around the globe. It establishes a common language and a foundation for mobile application security requirements. It aligns security and development teams to speed secure mobile app development. It specifies how to thoroughly test mobile apps against the security standard based on risk level. And it serves as an excellent learning resource for beginners and professionals on everything about mobile security.
Q: Who are key contributors?
A: The OWASP MAS resources are crafted and are curated by a team of numerous experts and community contributors working voluntarily. The core team includes me and Sven Schleier who lead the project plus a co-author, Jeroen Beckers.
Community contributors open issues, work on PR and communicate with us via Slack or other channels. Industry contributors such as Android and the App Defense Alliance (ADA) provide continuous, high-value feedback on all OWASP MAS initiatives such as the MASVS refactoring. And MAS advocates — NowSecure is the only one to date — are industry adopters of the OWASP MASVS and MASTG who have invested a significant amount of resources to push the project forward by providing consistent high-impact contributions and continuously spreading the word.
Q: How did you become an OWASP mobile project leader?
A: OWASP was organizing a Security Summit 2017 and one of the tracks was focused on mobile security, so I decided to attend. I was so amazed by the team, the topics we discussed and the things we implemented that I started contributing to the project. In 2018 I led my first session “Diving into Mobile Crypto using BDI with Frida” and became a co-author, and in 2019 I led a major restructuring of several areas of the MASTG so that the Android and iOS chapters mirror each other as much as possible, making it easier for readers to find the content they want to find.
After work, continuous commitment, and more work, such as proposing and leading major structural changes, I decided to apply for project leadership. I was sure that I wanted to continue to push the project and invest a lot of time to make everything better. I was very happy when I got the approval from OWASP, and I’m sure it was one of the best decisions I’ve made in my career.
Q: What are the renamed OWASP project elements?
A: Our project was previously called the OWASP Mobile Security Testing Guide (MSTG) project. Unfortunately, this was a source of confusion because we happened to have a resource with the same name, the OWASP MSTG. Not only that, but the name didn’t reflect the full scope and reach of our project. Since we already had the MASVS, have you ever wondered why the MSTG is called MSTG and not MASTG? Both documents are about mobile application security, and we wanted to make that clear.
In August 2022 we renamed the project to OWASP Mobile App Security (MAS). We also created a new logo and branding including new covers and names for our main resources. All of this was done to reflect all the consistency, structure, and transparency we’re bringing with our MASVS and MASTG refactoring efforts to bring them up to version 2.0.
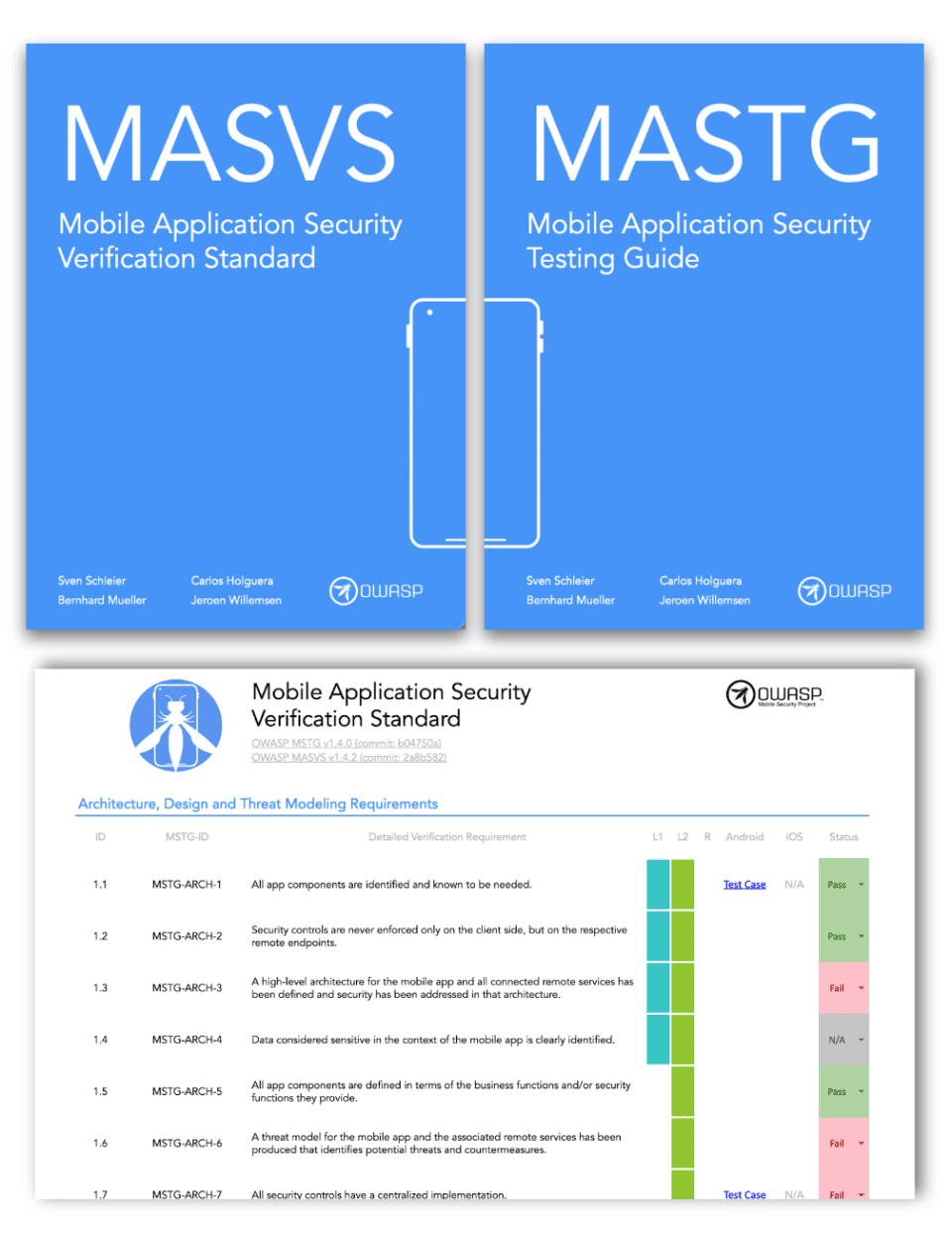
The core resources are:
- OWASP Mobile Application Security Verification Standard (MASVS) is the industry standard for mobile application security. It can be used by mobile software architects and developers who want to build secure mobile applications, as well as by security testers to ensure completeness and consistency of test results.
- OWASP Mobile App Security Testing Guide (MASTG) is a comprehensive guide to mobile application security testing and reverse engineering. It describes technical procedures for verifying the controls listed in the OWASP MASVS.
- OWASP MAS Checklist, which combines the MASVS and MASTG to aid security assessments/pen tests and compliance.
- OWASP MAS Crackmes, a collection of mobile reverse engineering challenges. These challenges are used as examples throughout the OWASP MASTG. Of course, you can solve them just for fun.
Q: Why did OWASP embark on refactoring MASVS?
A: Based on our experiences, the following issues often popped up:
- MASVS-ARCH (Architecture, Design and Threat Modeling) contains several controls that cannot be validated from an external perspective. As a result, it is difficult to explain why we can’t cover the entire MASVS for an external assessment.
- There is a clear overlap with the ASVS, which is much more thorough for various backend vulnerabilities.
- Some controls are very broad and require very broad test cases with multiple parts.
- Some controls overlap (e.g. ‘up-to-date security libraries’ and ‘all third-party components are up-to-date’).

Q: How did you approach the process and what did the work entail?
A: We’ve done a lot of brainstorming, independent thinking, collaboration, and community outreach to get feedback. We set up a few goals:
- Keep abstraction: The MASVS keeps being OS agnostic and high-level. We leave the details to the MASTG.
- Simplify: Have fewer controls by removing overlaps and redundancies.
- Bring clarity: Use standard terminology whenever possible to leave no room for ambiguity in language and formulation. This includes terminology from standards such as NIST-SP 800-175B and NIST OSCAL as well as well-known and used sources such as CWEs, Android and Apple Developer Docs.
- Narrow scope: Rely more on other standards including OWASP ASVS, OWASP SAMM and NIST.SP.800-218 SSDF v1.1.
We started releasing one GitHub Discussion per MASVS category including a spreadsheet with a detailed view of the changes. You can see why each control was removed/moved/reworded, read about the focus of the new controls, see the list of proposed new MASTG tests, and see how the control relates to other standards and resources.
Here’s what we did so far the second iteration:
- Processed all feedback from each of the beta proposal comments from the community.
- Tried to find overlaps and redundancies (again), e.g. MASVS-NETWORK-1 (beta) vs. MASVS-NETWORK-2 (beta).
- Tried to start all controls with ‘The app…’.
- Tried to formulate all controls with a ‘positive’ formulation.
- Tried negating each control to see if it still covered the same.
- Went through all test cases and double-checked coverage.
- Asked what/how we are protecting in each control.
In addition to being extremely insightful, this exercise has allowed us to provide you with an even cleaner version of the MASVS, which is designed to remain a timeless baseline for mobile application security, leaving the heavy lifting to the MASTG, which will become more dynamic and allow for more specific and flexible testing.
We created new spreadsheets where you can inspect all the changes and see the mappings from v2 to v1.4.2 and vice versa.
Q: What are the major changes in MASVS v2.0?
A: There are many:
- We removed the MASVS-ARCH category because it is covered by NIST.SP.800-218 SSDF v1.1 and OWASP SAMM.
- We decoupled MASVS-AUTH from OWASP ASVS. Users must use the OWASP ASVS on the server side. MASVS is for the client side, i.e. the mobile application.
- We’ve fixed the scope of many MASVS categories, especially MASVS-STORAGE and MASVS-PLATFORM, which had some overlap.
- We also aligned MASVS-CODE with NIST.SP.800-218 SSDF v1.1 and removed controls that can be addressed through a secure SDLC.
- We’ve simplified the language and wording of the controls throughout, especially in the Cryptography, Network and Resilience categories. This greatly reduces unnecessary verbosity.
- We’ve removed the verification levels from the MASVS and will rework them and then apply them to the MASTG test cases.
Q: How do those changes improve mobile application security for users?
A: One of the things we’re most proud of is the friendliness of our standard. Its simplicity makes it very accessible, so we tried to make it even friendlier to reach an even wider audience. The new MASVS controls are fewer in number related to v1 and use simpler language and familiar concepts. Any reader, even a beginner or coming from another field (e.g. web application security), will understand what ‘encrypted communication’ or ‘stored encrypted’ means. This way, we ensure that the higher level of the mobile attack surface is well understood.
With the new MASVS and the upcoming MASTG refactor, we’re bringing a new dimension to MAS testing; now you can test for compliance to our standard, but also customize it to your needs using profiles.
We’re also proud of the synergy between MASVS and MSTG. It’s unique in the industry and we’re going to make it even stronger. Until now, we have offered you the checklist as a link between the two. Soon you’ll get more, you’ll be able to interact with the standard in ways you never thought possible before.
The core deliverable will be a machine-readable file, similar to the one we currently use to generate the checklists, but enhanced so that you can use it to feed your own tooling, reporting and documentation tools. This allows you to verify MASVS compliance at newer and deeper levels.
All of these mechanisms, processes, and automation make us more agile and allow us to focus on what’s important: continuing to research and deliver the industry standard for mobile applications.

Q: What’s next for the MAS project?
A: We will publish the final version of the MASVS v2.0 after collecting and reviewing all comments from the Release Candidate. Hopefully this will happen in time for our upcoming presentation at OWASP AppSec Dublin.
Next, we’ll publish our first proposal for MAS Profiles definitions. The MAS profiles will replace the current MASVS levels, but don’t worry, our beloved L1, L2, and R aren’t going away completely. They’ll be back in a new, better form. They will apply to specific MASTG tests instead of MASVS controls. This will provide a fine-grained view of how an application maps to the overall MAS.
We’ll kick off the MASTG refactor to v2.0. We’re in the process of defining the sections for the atomic tests. This is very important so that everyone knows what to do when writing new tests. For each test, we’ll be answering essential questions:
- Why is the issue at hand bad and why are we testing for it?
- How do we test for the issue?
- How do we fix the issue?
We will publish the first proposal for MASTG atomic tests. We’ve published a preliminary list of tests (including only titles). Some of them are in the MASTG already and some are completely new. This first proposal will include the list of consolidated titles and a first proposal for profiles (e.g. L1, L2) for each MASTG atomic test.
Q: Why did you join NowSecure?
A: I get this question quite often. I say, ‘Have you seen the team?’ It may sound utopian, but imagine if you could assemble all the top talent in the mobile security industry, including the creators of the essential mobile security tools. Well, stop imagining, because here they are. So it was a no-brainer for me.
Other pluses are the company’s culture, values, and the fact that it already had a dedicated research team. Also, NowSecure is a big supporter of open-source projects such as Frida and Radare, and of course the OWASP MASVS and MASTG which I get to work on fulltime in my work with the company.
Another important point is that NowSecure is in line with my own passion for mobile app security. I fell in love with the OWASP mobile project and wanted to do something to save the world from unsafe mobile applications. As it happens, that’s also a NowSecure goal. So it was a natural next step for me.
Q: When you’re not immersed in mobile application security, what do you like to do in your free time?
A: Coffee and Japanese. I love going to coffee shops, whether it’s in my city or when I visit other places. I have my own espresso machine at home, and I’ve learned a lot about coffee and latte art over the years. As with mobile security and hacking, you have to be patient, persistent, and willing to accept failure.

When I have some free time and energy left over, I continue to learn Japanese. I’m in love with the language and I know it may take many years to understand and speak in an acceptable way, but I guess that’s part of why I like it, it’s an endless challenge. And I love its calligraphy, eating Japanese food and visiting the country.
Where to Learn More
Explore OWASP mobile security standards in depth by enrolling in free training from NowSecure Academy. The on-demand training includes several courses about OWASP, including OWASP mobile vs web standards, OWASP MAS updates and the MASVS and MASTG updates.
In addition, join us from 2 – 3 p.m. ET on Feb. 21 for a special upcoming NowSecure Tech Talk where you’ll get the chance to meet Holguera and hear him speak about the OWASP MASVS v2 updates. Register now.





