How to Use Frida & Radare to Crack a Mobile IoT App
Posted by NowSecure Mobile Security Advocate Tim Neighbors
Mobile AppSec security pros or Internet of Things (IoT) enthusiasts up for a challenge should follow along as esteemed NowSecure mobile security researchers demonstrate how they used leading open-source tools to reverse engineer and manipulate an IoT lighting control mobile app to discover security and privacy issues. In this recorded Black Hat 2021 conference session, Radare2 and r2frida Author Sergi Àlvarez (Pancake) and Frida Author Ole André Vadla Ravnås (oleavr) use their tools to put on the NowSecure version of a light show — that is, cracking a mobile app to flash Bluetooth Low Energy (LE) lights when the device microphone was in use.
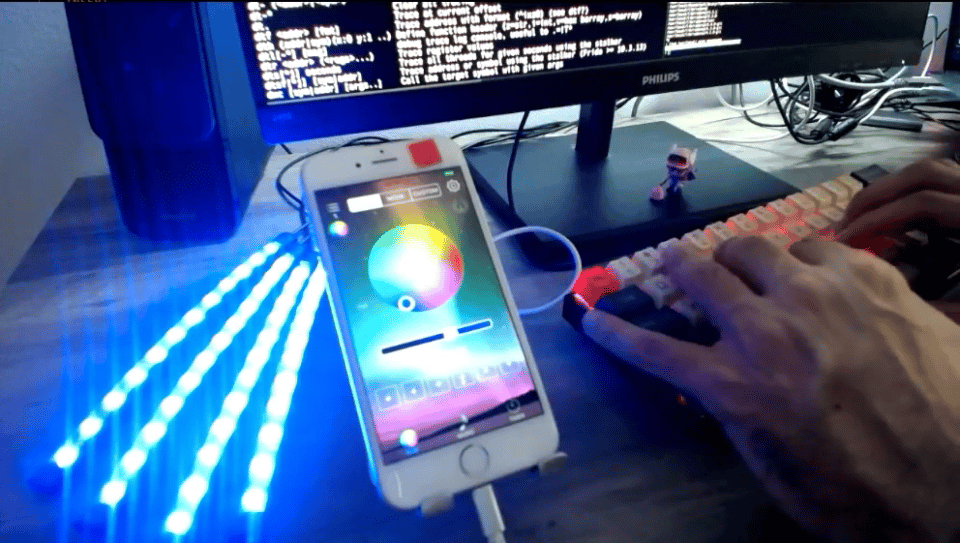
To play along, you’ll need the following components:
- LED BLE iOS app
- Inexpensive RGB LED device (ours cost $10)
- r2, Frida and r2frida OSS tooling
Once again, access the Black Hat session recording to see Ole and Pancake inspect the IoT app.
Mobile Risk Tracker
New NowSecure MobileRiskTracker™ – A Game Changer with Live Industry AppSec Scores
When we downloaded the LED BLE app from the App Store, the last update was in 2018. Watch the replay of “Cracking Fun with Frida & Radare: Mobile App & IoT Edition” to learn how to use the tooling to instrument the app and build our toy. We were able to flash the lights when using the device microphone.
Our ability to access the microphone demonstrated a common privacy concern, nor was there any way to block the mobile app’s access to the photo gallery or background code calls. This example underscores the need for developers to apply secure coding techniques and for organizations to tap automated mobile application security and privacy testing for all mobile apps prior to release.
NowSecure partners with the ioXt Alliance to ensure the security of IoT-connected mobile apps. The NowSecure ioXt Compliance Testing Solution empowers organizations to rapidly certify their IoT-connected mobile apps for the ioXt Mobile Application Protection Profile. For more insight into securing IoT mobile apps, consult NowSecure Researcher Abdel Eid’s blog post about standardizing automated security testing for Bluetooth LE.





