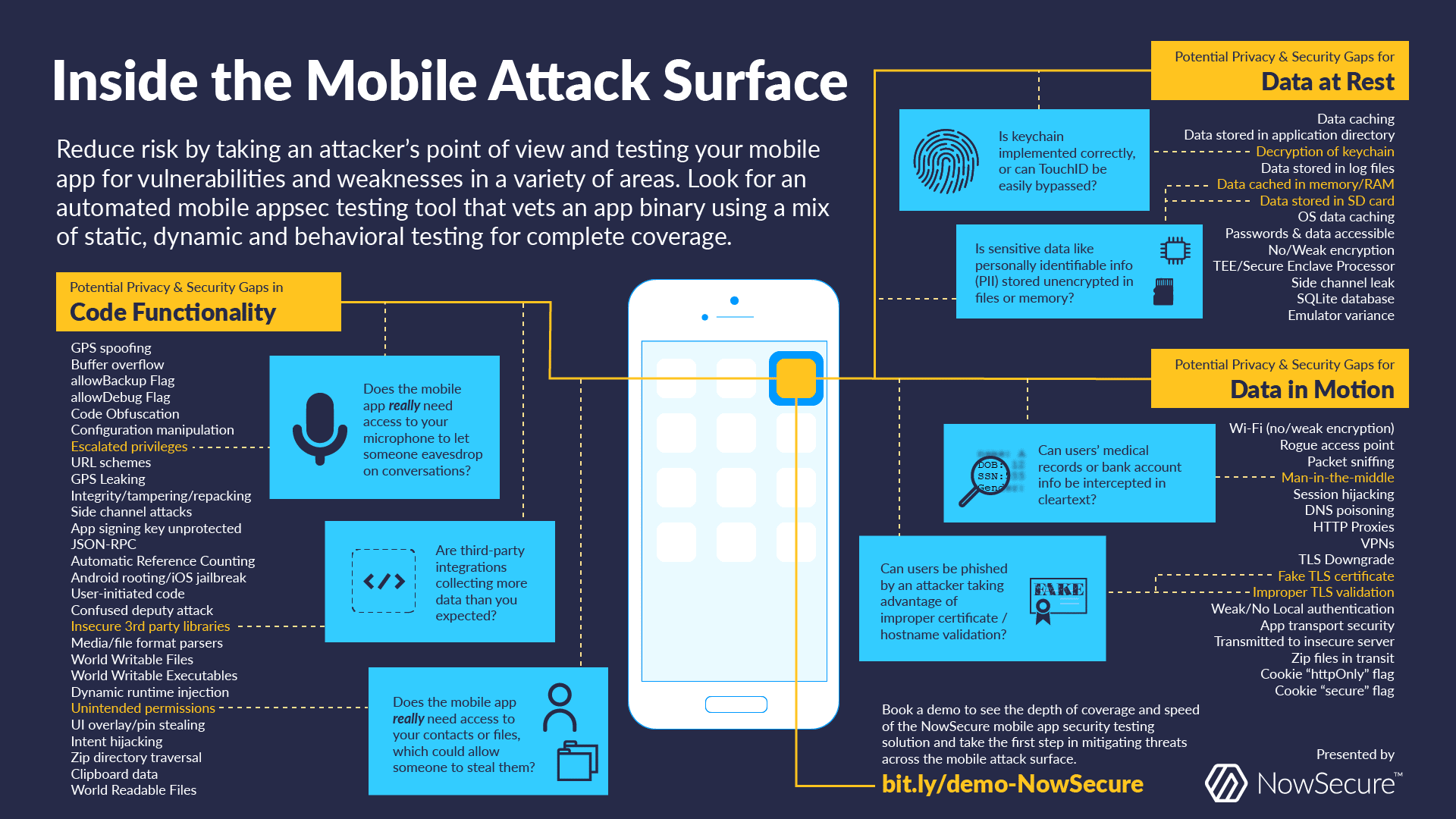
Application security managers are keenly aware of an abundance of mobile threats that can result in data loss, identity theft, and damage to brand reputation. One of the most effective ways to mitigate risk is to thoroughly assess the mobile apps that you build and deploy for security vulnerabilities and privacy flaws.
Mobile app vulnerabilities can be found in major areas: data at rest, code functionality, data in motion, APIs and back-ends. Consult the infographic below to drill deeper into mobile attack vectors and see all the areas of coverage your mobile appsec testing solution should focus on.
Related Content