A TechCrunch article reported that companies that specialize in analytics, such as Glassbox, use a technique called session replay that might violate a user’s privacy if the user hasn’t consented to monitoring. While Glassbox (formerly named Clarisite) is an example of an SDK that enables developers to record these sessions, it’s the app developers that integrate it and other similar SDKs that ultimately benefit from this recording capability and whose obligation it is to ensure user consent and privacy.
The initial TechCrunch research appears to have been performed by an anonymous researcher for the App Analyst site on the Air Canada iOS application. This NowSecure Research post aims to demystify and provide additional details around session replays on both Android and iOS.
Session replay is a technique that allows app developers to view screenshots, screen recordings, and touch events of how a user interacts with an app. This means that the developer can see where users click, what they type, where they scroll and how they navigate the app.
On the one hand, this information is valuable for developers because it can potentially save them hours of debugging in order to fix a bug. On the other hand though, depending on how this technique is implemented, it can have some serious impacts to a user’s privacy. Information such as credit card numbers, addresses, or other sensitive data could potentially be captured by the developer, sometimes without a user’s consent.
Based on the recent news articles, Apple already has started to notify app developers that they should obtain consent and inform users if they are being recorded.
How does session replay work on iOS?
There are at least three common ways to achieve session replay on iOS:
1. ReplayKit
2. WKWebView or UIWebView DOM
3. UIGraphicsBeginImageContext
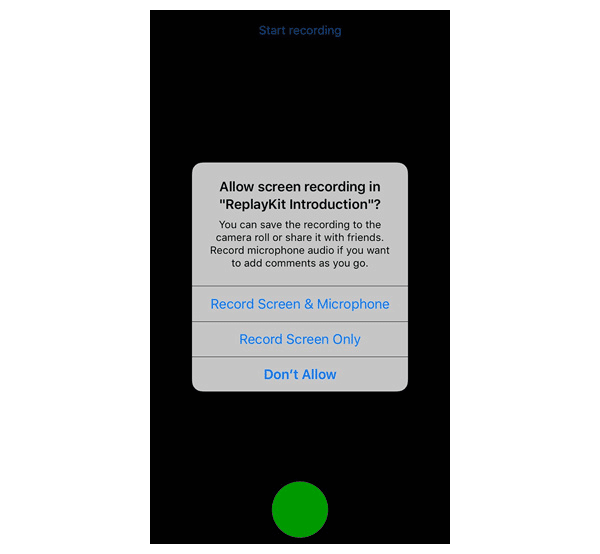
Apple introduced in iOS 9 the ReplayKit, which allows a developer to record or stream video from the screen. For this to work the user has to give consent to the developer.
When properly using ReplayKit, the following screen is presented to the user:
Another possibility is to leverage a JavaScript bridge, as is often used in hybrid apps. Hybrid apps are web apps in the native browser such as UIWebView in iOS. A session replay captures everything that happens in the WKWebView or UIWebView DOM along with its mutations while a user interacts with the app, then transforms that to a video to provide to the developer. In this case, only the DOM inside the UIWebView is being recorded.
Lastly, another technique is to take screenshots before a touch event, record where the touch event happens, and create a session replay from those actions.
One of the positives we did see while evaluating the Clarisite/Glassbox screen replay framework is that at least one of these frameworks has APIs that enable the integrator of the SDK to mask certain screens or regions of the UI. This functionality is inherently opt-in, however, and requires diligence on the part of the developer to ensure that no sensitive data ultimately ends up in a screen capture.
How can you record the native UI on iOS?
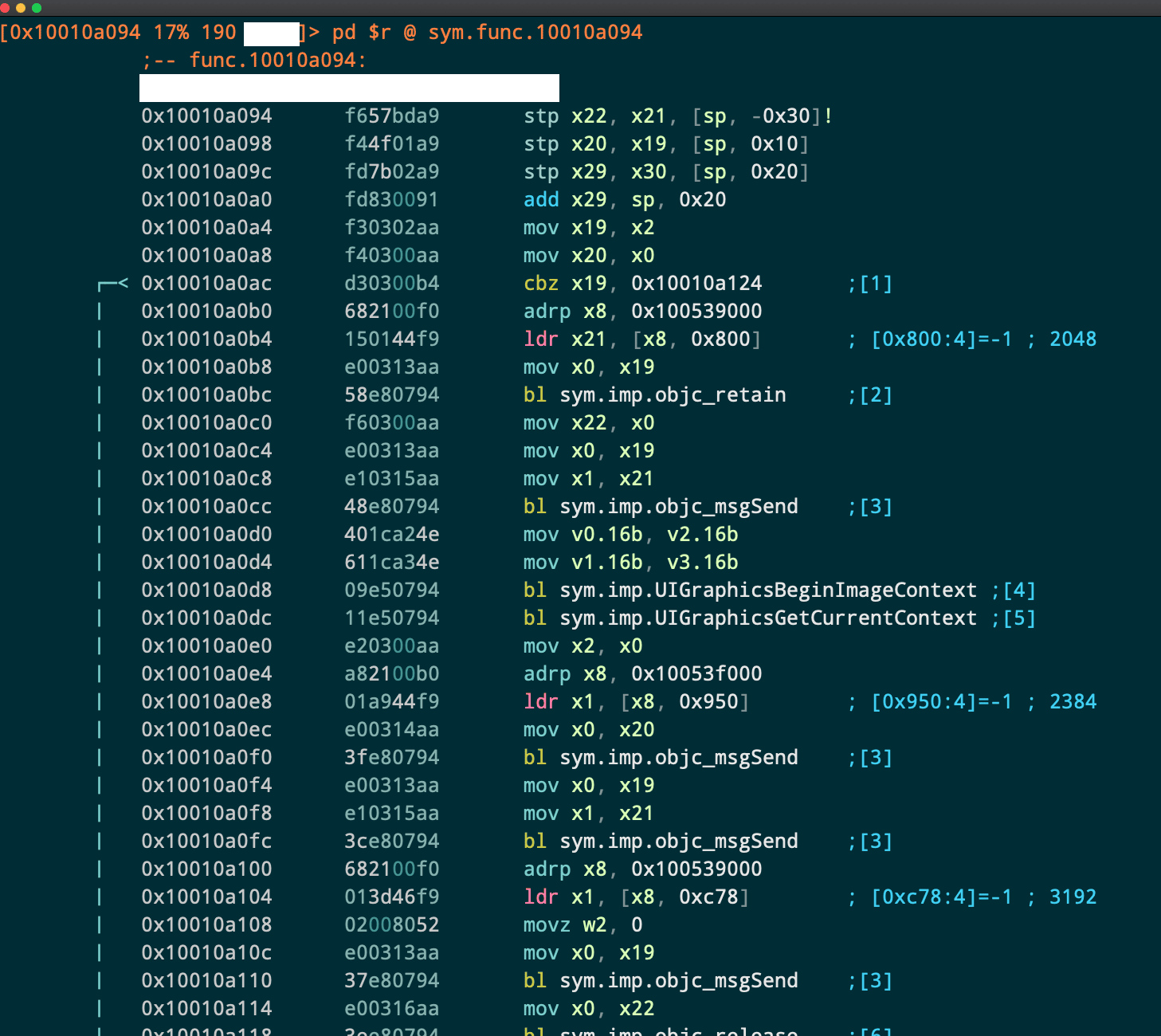
One approach is to use the UIGraphicsBeginImageContext API as mentioned in this Stack Overflow post. We all know Stack Overflow is the first place developers look for quick fix code snippets, right? In the example below we have purposely masked the name of the method that calls these APIs, but it’s from one of the popular screen recording frameworks we found.
How can you screen record on Android?
As with iOS there are also at least 3 ways to achieve session replay: MediaProjection API, WebView DOM, or via screenshot APIs.
The DOM technique that was described above can work for any web apps regardless of the underlying OS that they are running on.
Android also provides the MediaProjection API on Android, making it relatively easy to capture a user’s screen, but that still requires user’s consent as long as the phone is not rooted. The WebView approach, however, doesn’t require any special permissions to pull off. A variation of an iOS screenshot technique can also be used on Android.
How can you detect Glassbox on iOS?
There are a multitude of ways to detect Glassbox via dynamic or static analysis.
Dynamically one can monitor the network requests that are being made by the app and look for the *.glassboxcloud.com or https://glassbox.* in the url. Usually sensitive data such as click events or iOS versions are transferred there.
Detecting it statically now can happen in a couple of ways. As long as the app is not obfuscated, one can list the class names of the executable Mach-O binary and see if the ClarisiteServices, ClarisiteAgent or even the ClarisiteCordovaAgent is there. This can easily be done with a one liner in radare2: icj | jq .[].classname | grep -i Clarisite
[Note that Clarisite renamed to Glassbox but old API names remain.]
We mentioned the class ClarisiteCordovaAgent, which in a sense is a plugin for Cordova, an open-source development framework for hybrid apps on iOS and Android. This means that
somewhere this dependency should be specified, and indeed that is the case which usually resides in the www/cordova_plugins.js or sdk/cordova.js. The actual code of the plugin can be found in www/plugins/clarisite-cordova-plugin/www/detectors/detector-cordova.js. Inside there we can see that they indeed track various events such as mousedown, mouseup, touchstart, touchen, click, change, blur, focusout, submit, reset, load, unload, hashchange, ajaxComplete, popstate, focus, focusin, mouseenter and touchmove. There is also a JavaScript bridge between the native side of the app and the Cordova side where the developer can start tracking the user and report various events, whether on the native part of the app or on the web DOM.
Last but not least, one can find specific Clarisite/Glassbox Info.plist files usually either with the name ClarisiteSettings.plist or eyeviewResources.bundle/Info.plist.
How do you detect Glassbox on Android?
Detecting third-party libraries is easier on Android than on iOS. In this case, the developer has to specify a service entry in the AndroidManifest.xml file looking like this:
<service android:exported="false" android:name="com.clarisite.mobile.ClarisiteService">
<meta-data android:name="url" android:value="https://FOO.glassboxcloud.com"/>
<meta-data android:name="appid" android:value="FOO"/>
</service>Then the specific code will be under the package com/clarisite of course.
Are there other libraries out there with similar capabilities?
Yes, there are many other libraries/SDKs out there that appear to be taking advantage of both the WebView based recording and native UI recording. We won’t mention all of them here, but many are used broadly for web browsers that are easily ported to mobile WebView based applications. A list of these SDKs are just a couple of Google queries away.
What help can NowSecure provide?
The NowSecure Research team performs deep dive investigations of vulnerabilities and privacy issues to craft proprietary testing and reverse engineering innovations. The NowSecure research team includes the creators of popular open-source security tools, like Frida and Radare, who contribute continuous enhancements to our advanced automated analysis engine.
Built on these innovations, NowSecure software combines static (SAST), dynamic (DAST) and behavioral testing to analyze mobile app binaries running on real devices. Below are some sample screenshots from mobile apps where NowSecure has detected use of the Glassbox library.
AirCanada’s iOS app Network Data Flows during DAST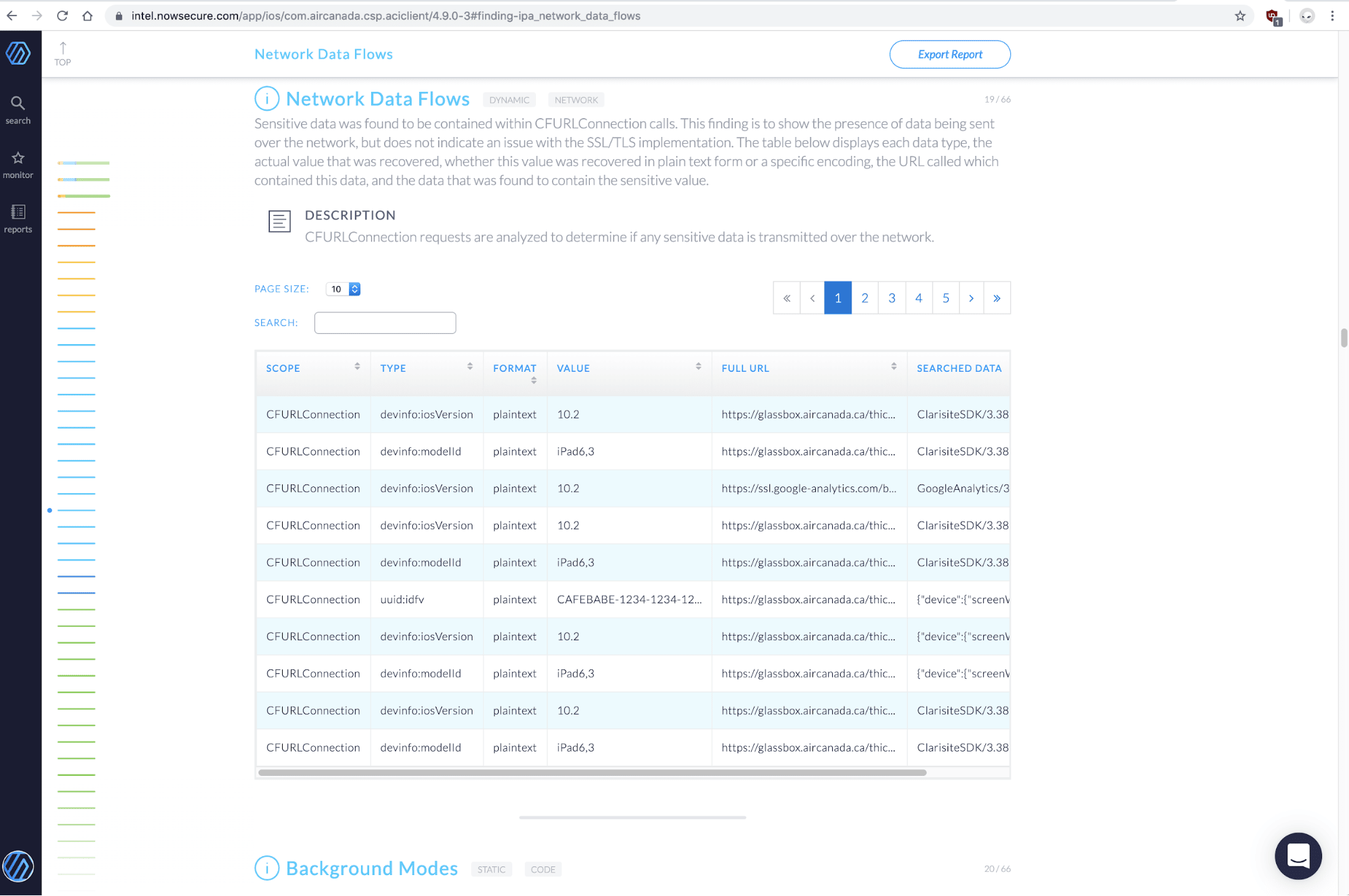
Detailed Network Data from an earlier version of AirCanada’s iOS app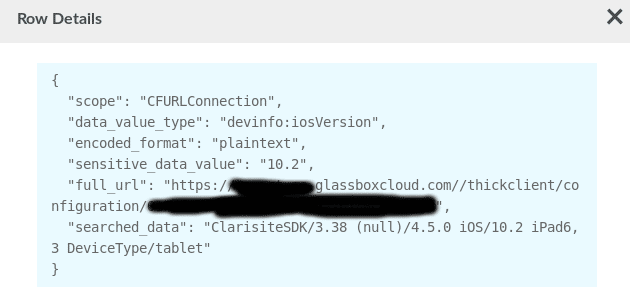
AirCanada’s iOS actual recording of events during DAST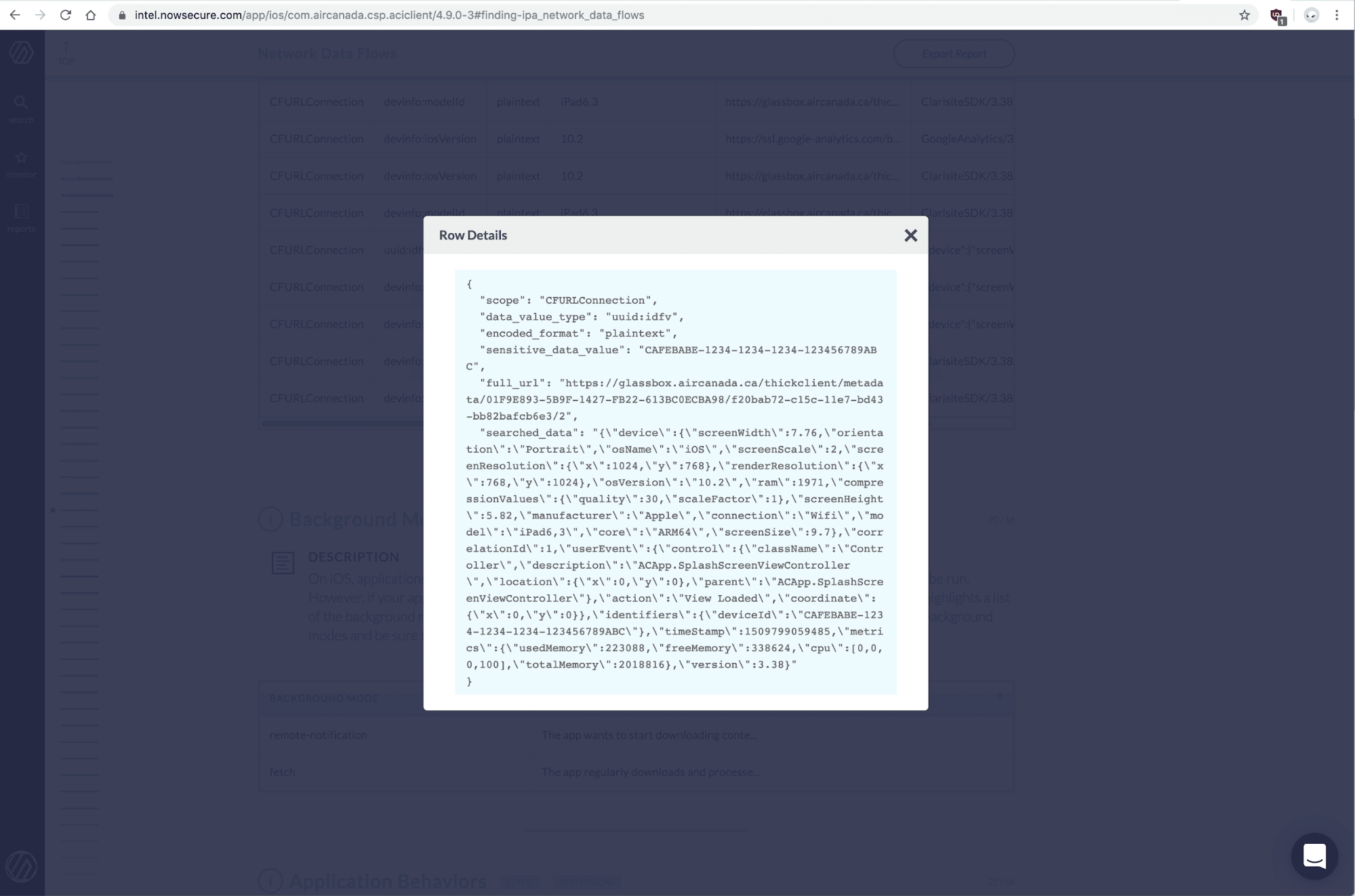
Activities & Services of AirCanada’s Android app during SAST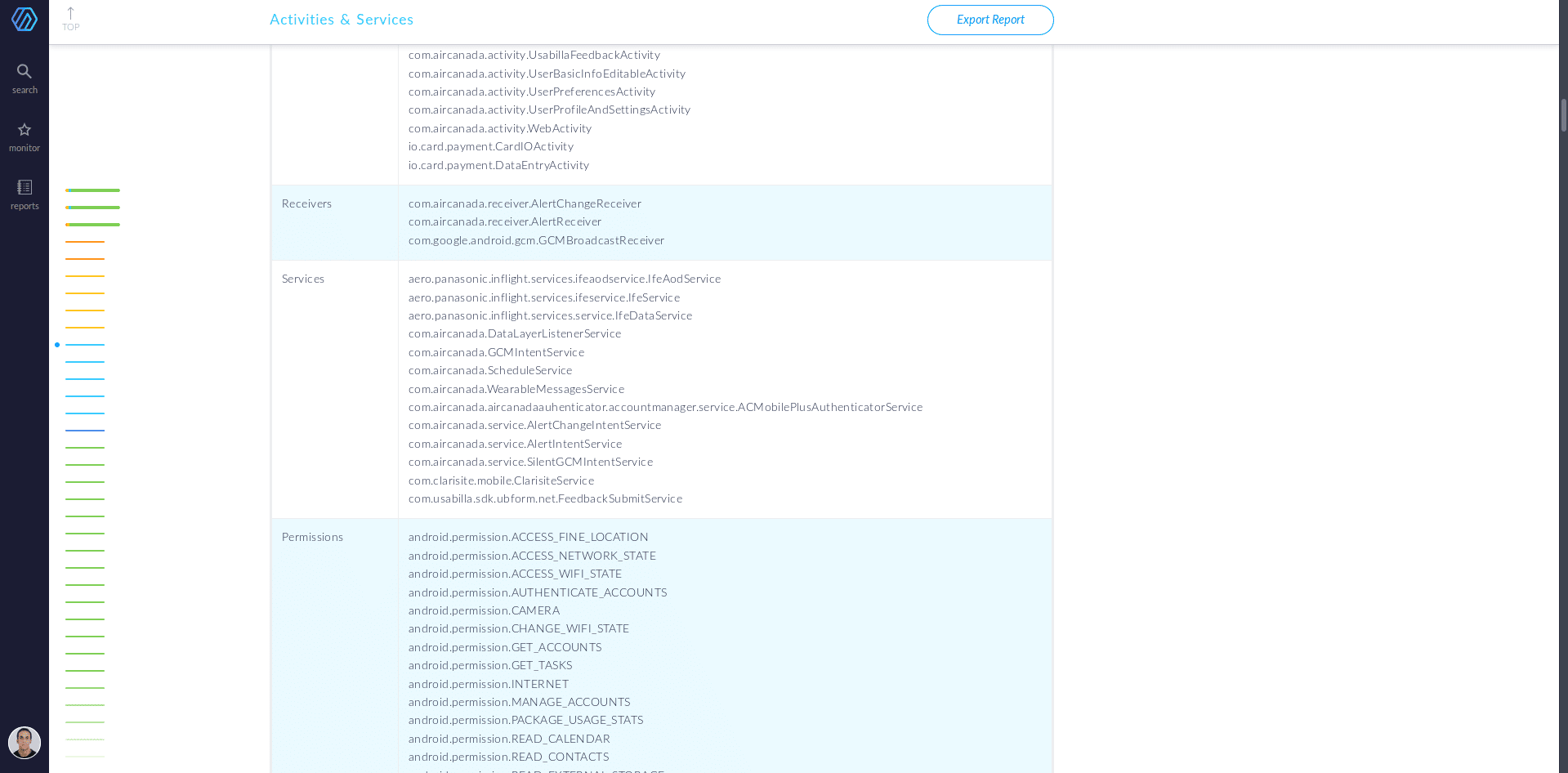
Summary
Session replay can be a very useful feature for developers to understand how customers use their apps, gain feedback to improve their apps and troubleshoot customer issues. But as discussed session replay needs to be implemented carefully and properly to safeguard user privacy.
Get a demo to see how the NowSecure solution identifies security, privacy and compliance issues to protect developers and users alike.