Growing up in Greece during a time when my country’s technology was immature, I spent countless hours assembling jigsaw puzzles or playing with my Playmobils. But today, many parents introduce mobile devices and apps to kids at a young age. I won’t argue if mobile technology helps or hinders your kids’ health and well being, but parents should be aware that children’s mobile apps have been under fire for violating privacy laws.
In the United States, the Children’s Online Privacy Protection Act (COPPA) protects children’s online privacy. Given the recent scrutiny about data privacy, NowSecure sought to evaluate popular mobile apps designed for use by young children aged six and under and their parents. Upon testing 50 Android children’s apps for security and privacy risks, we found some questionable behavior that potentially compromises young children’s personal information.
Testing Methodology
We randomly downloaded 50 free Android apps for young children from the Google Play™ store. App categories include baby monitors, games and storytelling apps. While we won’t name the specific app brands to protect the privacy of developers, the apps combined had more than 80 million installations and greater than 1.5 million average downloads.
To quickly zero in on the privacy and security issues of those kid’s apps, we used our NowSecure proprietary mobile app security testing tools. In less than eight minutes, we observed some disturbing findings. For the most accurate picture of mobile app security, privacy and compliance risk, use a combination of static application security testing (SAST), dynamic application security testing (DAST) and behavioral testing, an analysis technique NowSecure pioneered in the mobile security industry.
Privacy Results
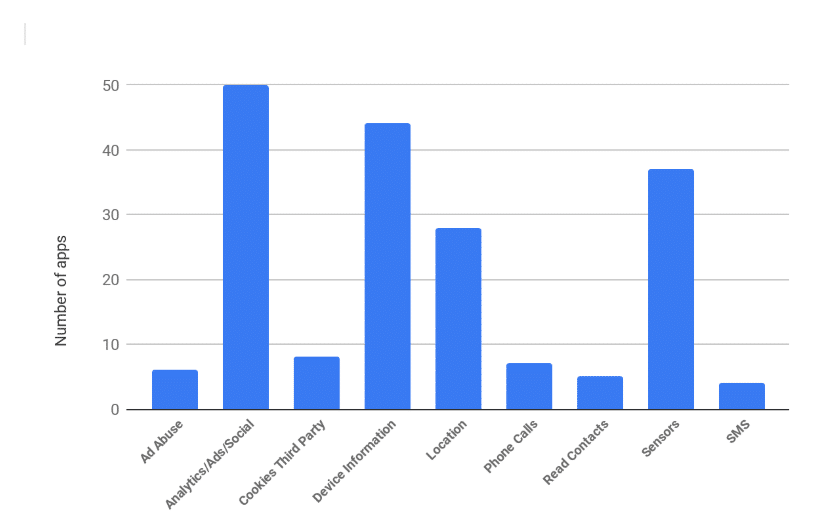
The chart below shows that 44 of the children’s apps access device-related information, as well as device sensors (37) and device location (28). The latter occurs either directly (8) or indirectly (28) via Wi-Fi or Telephony Manager APIs. This can be attributed to the fact that all of the apps contain either some sort of an ad library, crash analytics, analytics, and/or social network library.
Moreover, 12% of the apps enable advertising collection, which is generally used to track user demographics. Because a number of the apps are baby monitors that need to access a camera and microphone to operate, we won’t focus on findings about that functionality. On the other hand, 8% of apps send or read SMS, 10% can read the phone contacts and 14% can place a phone call. What’s more, eight apps allow third-party cookies to be set.
Security Issues
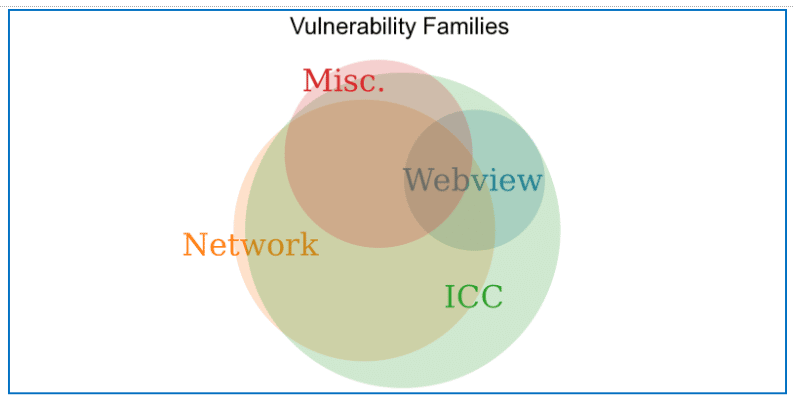
We categorize the security issues into four families of vulnerabilities. The Venn diagram below shows how the apps share these types of security issues. Nearly every children’s app we evaluated that has a security issue in webview or network also has an issue with the Android Inter-Component Communication (ICC) system.
Webview Issues
Through the NowSecure tool, we can see that roughly 75% of the apps have some form of webviews with Javascript enabled. This by itself is not bad, but it opens the door to various security issues. First, there is a single app that accepts file scheme cookies. This is something that is generally considered insecure and is disabled by default. Moreover, three apps contain a vulnerable version of jQuery. And six apps contain a default webview client that doesn’t restrict access to any web page, enabling it to be pointed to a malicious website that entails diverse attacks.
Network Issues
The NowSecure tool can display results related to misuse of network APIs and communications in general. At least 28% of the kid’s apps we tested use some form of network-based HTTP communication. We can see that three apps use a vulnerable version of OkHttp, while half of the apps potentially have a misconfigured SSL implementation (e.g., lacks hostname/server verification) exposing them to potential man-in-the-middle attacks.
Our analysis also shows a number of apps use a Firebase database. Surprisingly, one of the apps we tested didn’t have any rules for securing a Firebase database, which enables anyone with the link to access and read it. And out of all 50 apps, only one performs some form of proper certificate pinning for fully secure network communications.
ICC Issues
Android Inter-Component Communication can sometimes be tricky and quite complex. Our testing with NowSecure tools found that there are 31 apps with at least one exported component that is not protected with any permissions, and 11 apps with unprotected providers. A full 90% of the apps register an unprotected broadcast receiver, while 6% still use sticky broadcasts, which is deprecated from API Level 21. Plus, a single app has persisted dynamic permission.That means the developer grants permission to an app or component but forgets to revoke it, enabling the recipient of granted access to obtain long-term access to potentially sensitive data.
Miscellaneous Issues
Among miscellaneous issues, we observed that one app tries to run a su command. Moreover, we see that an app always initializes a random generator with a static value, while at the same time we see that 14 of the children’s apps can create world readable/writable files. Last but not least, one app sets the setRandomizedEncryptionRequired to false. That means that a given plaintext will always produce the same ciphertext, potentially compromising security.
Key Takeaways
Our findings indicate that parents are right to be concerned about mobile apps that collect kid’s personal information and potentially leak that information. Developers of Android apps for young children should properly test their apps for security and privacy risk prior to release to ensure they maintain compliance with regulations such as COPPA.
The NowSecure solution automatically tests mobile app binaries for Android and iOS using a hybrid approach of dynamic, static and behavioral analysis. If you’re a developer of mobile apps for children, book a demo to see how to reduce risk with automated mobile app sec testing. And if you’re curious about the security, privacy and compliance stance of the mobile apps your organization uses, score a free mobile app risk assessment for one app today.