How Google aims to reduce mobile OS fragmentation with Android API levels
Posted by Tony Ramirez Ashleigh Lee
The problem of mobile platform fragmentation has worsened over the years, especially among Android devices. Google is now taking action to reduce Android fragmentation by requiring developers to adopt recent target API levels for all new apps beginning in August.
A snapshot of data taken in May 2018 from the Android Developer Distribution Dashboard reveals these Android operating system adoption rates:
- Less than six percent of Android users are on the latest version—Android 8 Oreo, released in August 2017.
- About 31 percent of users are on Android 7 Nougat, released nearly two years ago in August 2016.
- Just over one-quarter of users are on Android 6 Marshmallow, released in October 2015.
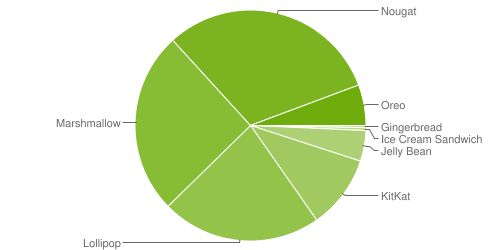
Source: Android Developer Distribution Dashboard
This means nearly 40 percent of Android users are stuck on an OS release that is more than three years old. Without timely mobile OS updates, enterprise users and their employers find themselves exposed to the latest mobile application security threats. To help reduce Android version fragmentation, Google will soon begin enforcing current Android API levels for all new and updated apps uploaded to the Google Play store.
We want to proactively reduce fragmentation in the app ecosystem and ensure apps are secure and performant while providing developers with a long window and plenty of notice in order to plan ahead.”
Google is taking a two-pronged approach to reduce Android fragmentation. Announced in May 2017, the Project Treble initiative aims to simplify the process that device manufacturers undergo to get their phones and tablets running the newest version of Android. Unfortunately, most old Android devices do not support Treble. So Google launched another plan to reduce Android fragmentation by requiring developers to incorporate current API levels in their new releases and updates. Google will begin enforcing its new target API level policy in August.
What’s an Android API level?
Simply put, an API level is another way of referencing a version of the Android OS release and its Software Development Kit (SDK). For example, Android 8.1 is referred to as API level 27, Android 8.0 is API level 26, Android 7.1 is API level 25, and so forth.
Technically, the Android API level is the framework apps use to interact with the Android system. Every version of Android is an additive framework so apps are generally forward compatible, but not necessarily backward compatible. Developers can specify a target API level and a minimum API level in the manifest of an app to designate which version of the OS an app is designed to run on and which is the oldest version it can run on.
What’s changing?
Historically, if there were new features in more recent Android API levels that helped users but created significant work for developers, developers could simply target lower API levels to avoid accommodating those features, such as a la carte permissions or less background processing. However, the new policy will adversely affect app availability if the app updates don’t meet the target API level requirement.
Future Android versions will also restrict apps that don’t target a recent API level and adversely impact performance or security.”
- As of August, new apps will be required to target API level 26 (Android 8.0 Oreo) or higher. (FUN FACT: this API level will have the network security configuration feature baked in. Is it mandatory to use it? No, but we do recommend it as a layer of security to your app.)
- Beginning in November, existing apps that are updated on Google Play will be required to target API level 26 or higher.
- And beginning in 2019 and onward, the required target API level will increase.
Within one year following each Android dessert release, new apps and app updates will need to target the corresponding API level or higher.”
Developers can continue to code for older versions of Android and designate the minimum API level in the manifest. Old apps that don’t get updated on Google Play will be grandfathered in. (FUN FACT: There are still debuggable apps living in Google Play.)
It’s worth noting that minimum Android API levels do not have to be designated in the manifest. However, if left unspecified, the minimum Android API level will default to the target Android API level. This means if your app targets Android API level 26 (Oreo) and has no minimum Android API level specified, devices running on Android API level 25 (Nougat) or older will not be able to install it, fundamentally limiting the reachable audience.
While restricting the use of apps on older Android API levels may seem like a security benefit, bad code is bad code no matter what device it runs on. Developers will now be required to target a recent Android API level to prevent availability issues while coding to ensure their mobile apps don’t expose users to security, compliance, or privacy risks.
As developers continue to evolve their mobile apps to abide by Google’s new policy, security teams can keep up with release cycles by quickly testing apps pre-release for any vulnerabilities. Integrating automated, purpose-built mobile application security testing into their pipeline helps companies quickly pinpoint and fix vulnerabilities before releasing their apps to Google Play. Learn more about tools for automating mobile application security testing here.





