OnePlus Device Root Exploit: Backdoor in EngineerMode App for Diagnostics Mode
Posted by NowSecure Marketing
A number of mobile devices manufactured under the OnePlus brand by China’s BBK Electronics are vulnerable to compromise via a factory-installed app called EngineerMode that acts as a backdoor providing root access to affected devices. At this time, the exploit is most useful to an attacker with physical access to a OnePlus device or an owner looking to root their own device. OnePlus devices are more prevalent in markets outside the U.S. such as China and India but are gaining popularity in the U.S. A security researcher posting on Twitter under the pseudonym “Elliot Alderson” (a reference to the “Mr. Robot” TV show protagonist) discovered the problematic app on Monday. Within the hour, the NowSecure Mobile Threat Research Team set to work helping validate the root exploit.
In fulfilling the NowSecure mission, we educate customers about the latest mobile security threats and help them maximize the security of the mobile apps they use and develop. Here we explain this new OnePlus root exploit and what financial services organizations, government agencies, and other enterprises need to do to protect themselves. To start, if you or anyone within your organization uses a OnePlus mobile device (especially enterprises with offices in Asia), beware of the EngineerMode app so that you can take appropriate action to mitigate the risk.
Why is the EngineerMode app dangerous?
OnePlus develops its own customized version of the Android operating system, called OxygenOS, for their branded devices. In this case it appears OnePlus mistakenly left a diagnostic app, EngineerMode, developed by Qualcomm for pre-deployment device testing in the production build of the OxygenOS operating system. What seems especially careless is OnePlus leaving behind a system-signed .apk and a native library with a SHA256 hash of the password that was easily reversed. On Twitter, Qualcomm VP of Product Security Engineering Alex Gantman stated that the EngineerMode app was not authored by Qualcomm but that others had built on top of a past testing app.
With the password, the EngineerMode app enables a debugging mode that is generally only needed for development of the device and grants full root privileges on the device via a simple ADB command or potentially by installing an APK from the Play Store. In general, devices that include such a dangerous diagnostic app still on the firmware should not be released to the public because it puts users at risk. On Twitter, OnePlus co-founder Carl Pei thanked the original Twitter poster and said the company would investigate.
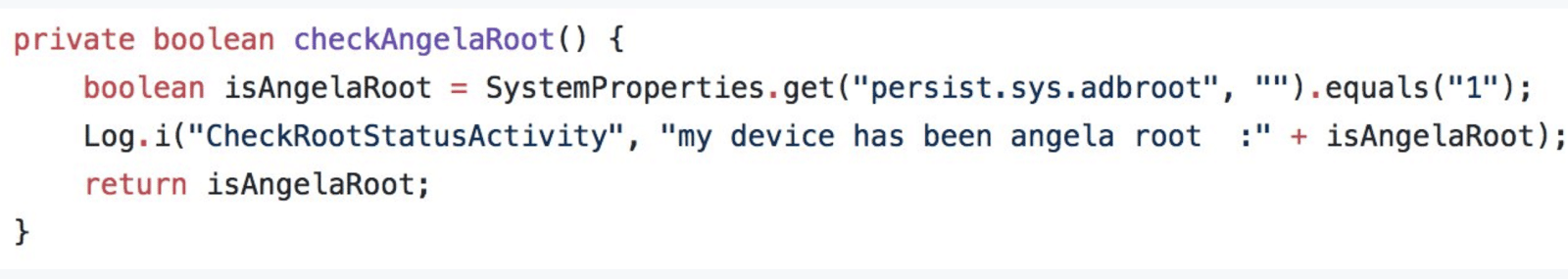
Entering the password, which turned out to be “angela” (possibly another “Mr. Robot” reference to character Angela Moss), just once grants permanent root access to the Android Debug Bridge (ADB) process via the EngineerMode app — essentially creating a backdoor to root privileges on affected OnePlus mobile devices.
Here’s the ADB command that enables this “backdoor”:
adb shell am start -n com.android.engineeringmode/.qualcomm.DiagEnabled --es "code" "angela"
Again, using this shell command triggers the diagnostic mode (or backdoor) and grants future ADB sessions root access, even after the device is rebooted.
Is my OnePlus Device affected by this backdoor?
The NowSecure Team verified that at least the following OnePlus devices are affected by this root exploit:
- OnePlus 3 (OxygenOS 4.5.1, build number ONEPLUS A3003_16_171012)
- OnePlus 5 (OxygenOS 4.5.14, build number ONEPLUSA5000_23_171031)
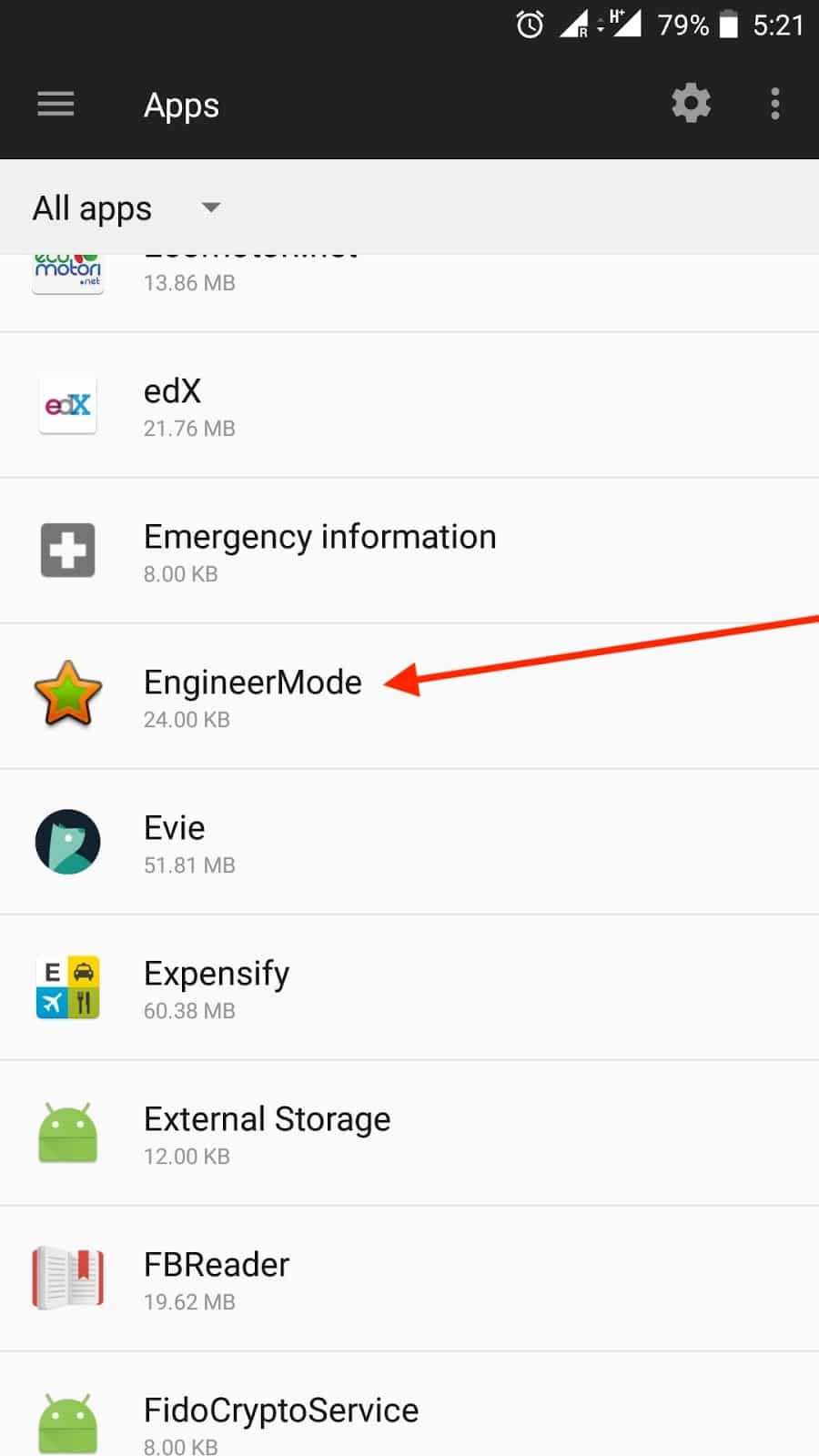
To determine whether your device is affected, look for any .apk with the name “EngineerMode” by going into the device settings, navigating to “Apps,” then “Menu,” then “Show System Apps” and searching for the EngineerMode app as shown below:
How Did NowSecure Get Involved?
“Alderson” stumbled upon a factory-installed app called EngineerMode on a OnePlus device and suspected that the app used for diagnostic purposes was a backdoor.
<Thread> Hey @OnePlus! I don’t think this EngineerMode APK must be in an user build…🤦♂️
This app is a system app made by @Qualcomm and customised by @OnePlus. It’s used by the operator in the factory to test the devices. pic.twitter.com/lCV5euYiO6— Elliot Alderson (@fs0c131y) November 13, 2017
The discoverer speculated that the EngineerMode app might provide root access to the OnePlus device given the right password. “Alderson” put out a call for skilled reverse engineers to help him identify the password needed to enable the diagnostic mode through the app and grant root privileges to the ADB process. The NowSecure Research Team, together in the Washington DC area this week for a team summit, happily obliged.
Combining their wits with the open-source reverse-engineering framework Radare — created and maintained by a member of the NowSecure Mobile Threat Research Team, sponsored by NowSecure, and built-into the NowSecure Platform™ — the team quickly identified the password and verified the backdoor.

The NowSecure team included (from left to right in the photo above) CTO David Weinstein and researchers Francesco Tamagni, Ole André Vadla Ravnås, and Ioannis Gasparis.
How did NowSecure find the password?
To start, the team disassembled the EngineerMode .apk binary using Radare and collaborated to reverse-engineer the native code extreme programming style. Attackers take the same approach in profiling and targeting Android and iOS apps, and a crucial aspect of the NowSecure mobile app security testing methodology is to approach an app from the attacker’s point-of-view.
The Radare screenshot below shows the results of the binary disassembly:
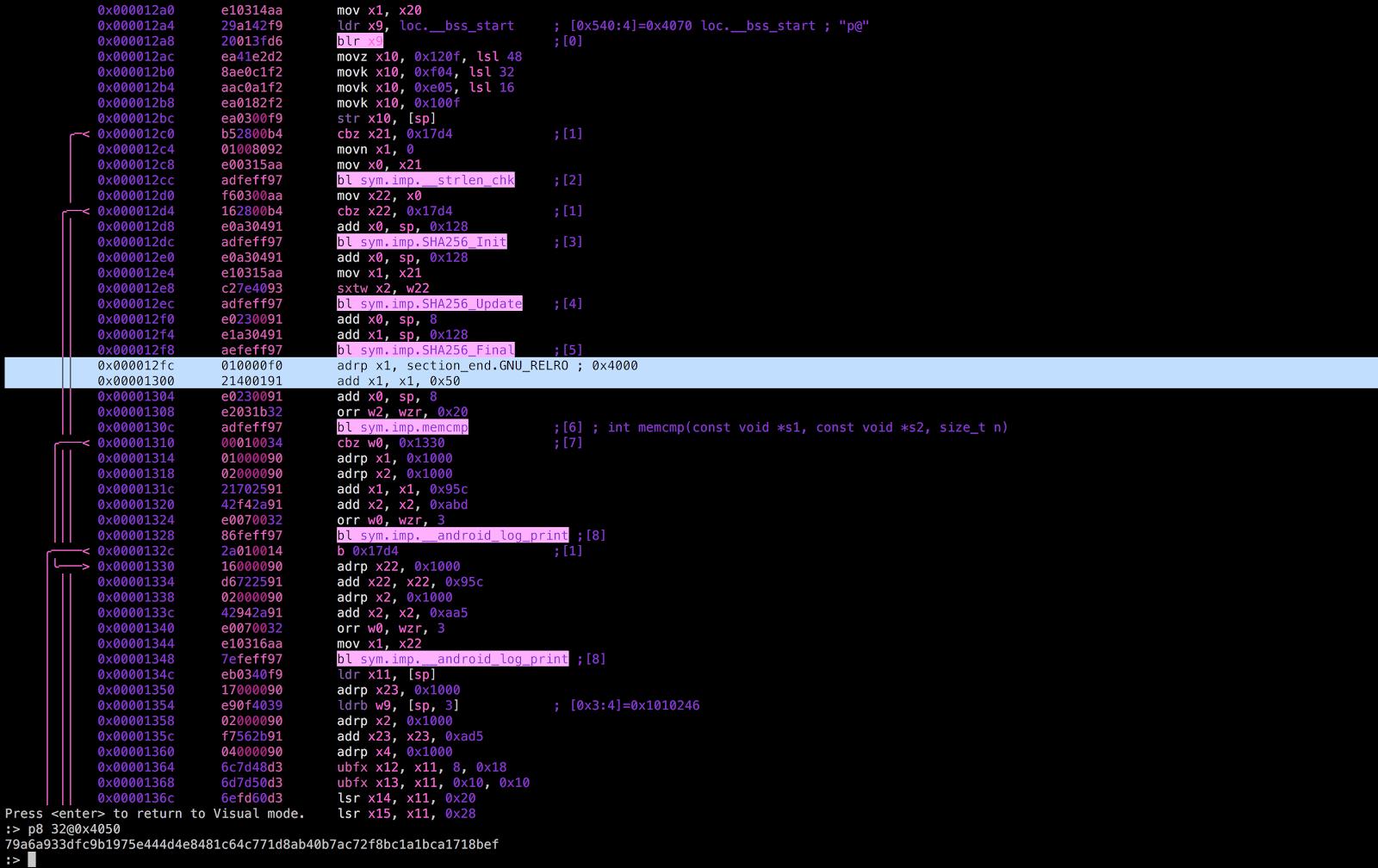
The team discovered the comparison (`memcmp`) they sought nearby the code that performed the SHA256 hash of the user-supplied password in the code section for the symbol `JNI_OnLoad`. Discovering the valid password hash in the binary (79a6a933dfc9b1975e444d4e8481c64c771d8ab40b7ac72f8bc1a1bca1718bef), they found the hash to be trivially reversible to the string “angela” with a mere copy-and-paste into Google search.
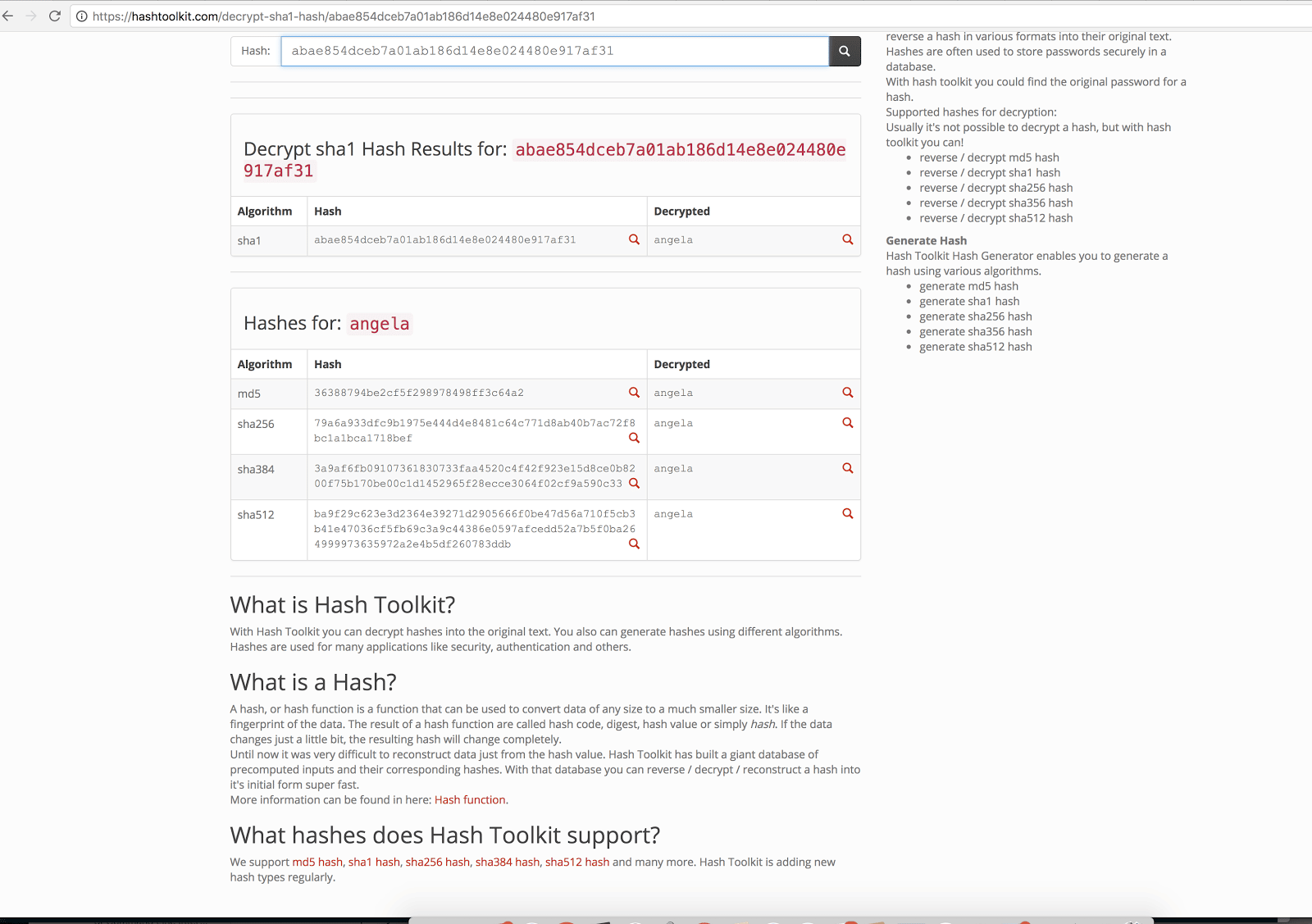
With that, the NowSecure Team found and decrypted the password used to enable diagnostic mode on the device, verified the backdoor and notified the original twitter poster who confirmed:
Awesome! Thanks to @insitusec and the @NowSecureMobile team, we have the password! It’s now possible to root an @Oneplus device with a simple intent pic.twitter.com/gN0awYijBv
— Elliot Alderson (@fs0c131y) November 13, 2017
It turns out (later discovered by “Alderson”) that a password hint existed in the EngineerMode .apk all along as shown below:
NowSecure and the NowSecure Platform can help ensure that the mobile apps you develop do not include potentially high-risk mistakes such as this one (or identify similar mistakes in 3rd-party Apple® App Store® and the Google Play™ store apps used by your employees). To find out more about the OnePlus EngineerMode backdoor or NowSecure products and services, e-mail us at [email protected] or fill out our contact form.




