There is no denying that mobile applications have become ubiquitous. For many companies, building an app is a foregone conclusion. We have applications for social, for fitness, for productivity, for organization and even for things as sensitive as our finances. We are all increasingly turning over more of our personal information and data to applications and companies we may know very little about. On the web, we can be sure that application data is transferred securely when we see the bright green lock icon symbolizing that a site has implemented an SSL certificate. What about for mobile? How do you know that an application is adhering to security standards when passing data to its back end Application Programming Interface (API). For those building the apps, do you have a handle on what the best practices are for mobile API security? This series will discuss the aspects of planning, implementing and deploying secure APIs to power mobile applications. To start with, let’s explore the API planning process.
Mobile app authorization
The first step in securing your application’s API is deciding on an authorization protocol. The choice of authorization protocol is critical because it is the entry-point to all of the sensitive data your users may provide you. When considering your choice, think about the answer to these three questions:
- Identity – Who is it that will be querying the API?
- Authentication – How do you verify who they are?
- Authorization – Are they allowed to access what they are trying to access?
If you simply need to track API hits, you can use a simple API key. If you need to verify identity, you can use HTTP Basic authentication with a username and password. If you’re looking for a higher level of security and controls on identity, authentication and authorization then you’ll want to look into OAuth as a possible solution for your application. In the below diagram detailing the OAuth flow, the user will, through an app (the Consumer), try to authenticate against a Service Provider (e.g., Facebook when you “Connect with Facebook”).
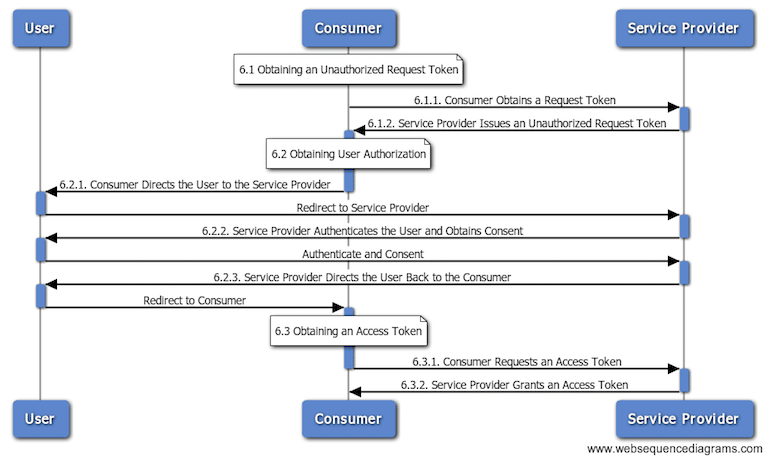
Diagram via https://joecodeswell.wordpress.com/2011/06/08/oauth-uml-sequence-diagrams/
[Editor’s note – Some developers need help implementing OAuth correctly. See the NowSecure blog post, How bad OAuth 2.0 implementation sabotages mobile app security for more.]
Securing data in transit
Once you’ve selected your authorization scheme, the next concern is in transferring the data safely between the application and the server. For this purpose you’ll need to use HTTPS with TLS. Both protocols use an ‘asymmetric’ public key infrastructure (PKI) system. This type of system relies on a public and private key for encryption. Once encrypted with the public key, information can only be decrypted by the private key. In order to establish a secure connection, the server must have an SSL Certificate which binds the domain with an organizational identity and location. You can get certificates from paid sources like DigiCert, Comodo, Symantec, Network Solutions and many others. However, there are some new certification authorities that provide reputable SSL Certificates for free! If you’re interested, have a look at Let’s Encrypt.
Access tokens
So you’ve got your authentication scheme set up, you’re passing data securely over the wire, and you’re ready for the next step. Now you’ll want to setup a way to represent a claim to be transferred between parties. To do this, your best bet is to use a JSON Web Token (JWT). JSON (Javascript Object Notation) Web Tokens are simply JSON objects which are signed using JSON Web Signature (JWS) and/or encrypted using JSON Web Encryption (JWE). The purpose of this is to be able to transfer verifiable claims such as “I am logged in as an administrator.” The claims can be verified by the server or thrown out if they are false.
API security tools
Now that you have an understanding of the basic decisions you’ll need to make when creating a secure API, you’ll need to know about some incredible companies providing all-in-one security tools that handle much of the aforementioned challenges for you. The market leading API security and management solutions are:
- Mashery
- 3Scale
- Apigee
- Restlet
- Layer 7
With these basics, you’re prepared to begin mapping out an API for your mobile or web application. In our next installment, we’ll talk about the best practices for developers to adhere in order to maintain application security to while coding.