What is the Dirty COW vulnerability and how does it impact mobile security?
Posted by Sergi Àlvarez i Capilla NowSecure Marketing
This week, details about the Dirty COW vulnerability (CVE-2016-5195) were made public. The vulnerability interested me because of the potential grand scale of its impact (and specifically its impact on Android). I analyzed the vulnerability and exploit to find out more about it and also ended up writing a plug-in for Radare2 that uses the exploit.
Dirty COW was introduced in Linux version 2.6.22 around 2007 and is reportedly being exploited in the wild. A CVE Identifier (CVE ID) number was filed for at the end of May 2016, a patch for the Linux kernel was released on October 13, and Linus Torvalds made a commit to the master branch on October 18.
You can read more about the vulnerability on the official Dirty COW website. A working exploit has been published on the Dirty COW GitHub repository.
A lot of technology uses Linux, and not just desktops and servers. Other devices that use Linux include routers, embedded devices, and mobile phones running the Android, FirefoxOS, and Sailfish operating systems.
What does Dirty COW mean for mobile security?
The bug allows an attacker to modify the copy-on-write (abbreviated COW – from where the vulnerability gets its name) cache provided by the kernel in order to change what the system and apps see when reading the affected files.
The attacker is able to modify the contents in memory of any file readable (and mmapable) by the user. This means that “non-COW-ed” filesystems like /sys or /proc are not affected. On some systems, executables are not affected. But for the vast majority of systems, this exploit can be used to modify any file, even if the partition is mounted as read-only.
As long as the modifications only affect the cache in memory, they will not persist after a reboot.
However, these capabilities are enough to gain root privileges and pwn the system completely.
Am I affected?
If you have any device running a Linux kernel higher than 2.6.22, there’s a good chance that you are vulnerable. The same goes for all versions of Android whether they come from Samsung, Google, Cyanogen, MIUI, or other vendors because they have not yet issued security updates.
In order to exploit this vulnerability, the attacker needs to run code in the affected device, which in Android’s case can be done via the Android Debug Bridge (ADB) over USB or by installing an app that makes use of the exploit.
How do I protect myself?
While updates aren’t currently available for any impacted device, by following good security practices you can reduce your risk of exposure. As long as Dirty COW is a local vulnerability, and running native code on Android requires no special permissions, the first recommendation is to avoid installing software from unknown sources. Also, beware when connecting your mobile device to a computer using USB because (only hypothetically at this point) desktop malware could use ADB to exploit the vulnerability in a phone and achieve root privileges.
Playing with the Dirty COW
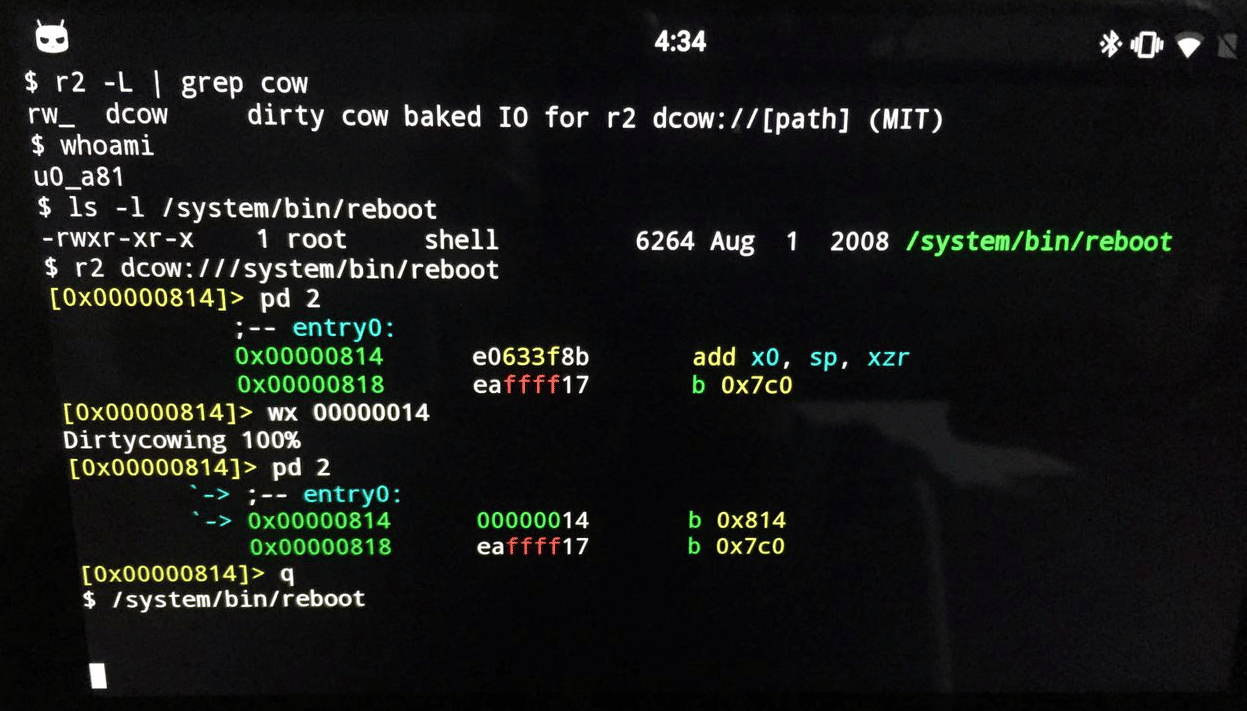
Having a public exploit was enough to motivate me into writing an IO plugin for Radare2.
A Radare2 IO plug-in that takes advantage of the Dirty COW vulnerability allowing a user to modify files owned by other users is now available at https://github.com/nowsecure/dirtycow. Within the same repository you’ll find a program called “cowpy” that allows a user to copy the contents of files into other files.
Here’s a screenshot of the PoC: