Building blocks for secure mobile development: Testing for the OWASP MASVS Top 10
Posted by Keith Mokris NowSecure Marketing
Security leaders are tasked with quickly and consistently managing mobile risk within and beyond their organization’s walls, a task that will only get more difficult as mobile app usage and development continues to rise.
The Apple App Store, which currently has an estimated 2 million mobile apps, is expected to more than double to over 5 million active apps by the year 2020. The QA managers, security teams, and mobile developers that NowSecure works with use the OWASP MASVS as a de facto security standard to help them develop more secure code, fix flaws earlier in the development lifecycle, and reduce the vulnerability of an app before they’re deployed. To help customers assess their mobile apps against the OWASP MASVS, our mobile app security testing solutions map findings to the list.
Building blocks for mobile security success
Leaders in the security space should be familiar with the Open Web Application Security Project (OWASP). The purpose of this post is to familiarize developers, QA professionals, and security analysts with the OWASP MASVS, as well as provide additional guidance from the NowSecure Secure Mobile Development Best Practices about how to avoid or remediate the top ten risks. The OWASP MASVS offers a key building block that we want security teams to check off their list when using our mobile app security testing solutions.
The list is ever-evolving to meet the rapid speed of mobile innovation. The community has plans to update its guidelines for mobile in 2016. While the mobile threat landscape extends well beyond the categories here, we recognize their value in securing mobile app data, connecting to outside servers, handling sessions properly, and more.
The OWASP Mobile Top 10
Below, you’ll find a breakdown of each category on the list with corresponding links to our Secure Mobile Development Best Practices.
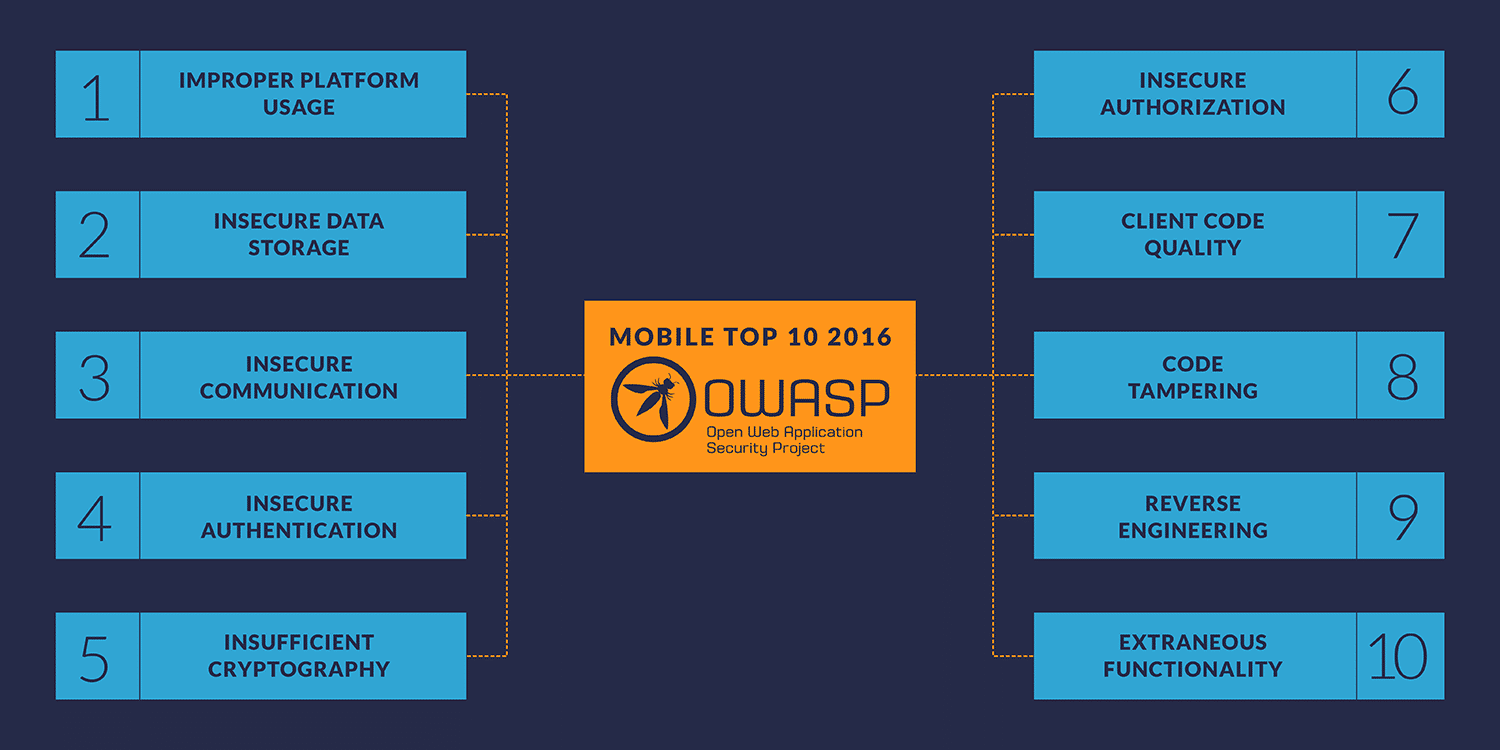
M1 – Improper Platform Usage
This category focuses on misuse of a mobile operating system feature or lack of platform security controls for the Android or iOS operating systems. Issues may include incorrect use of the keychain on iOS or Android intents.
Best practice: iOS: Use the Keychain Carefully
M2 – Insecure Data Storage
According to the 2016 NowSecure Mobile Security Report, 25 percent of mobile apps have a least one high risk security or privacy flaw. These vulnerabilities leak personal information that can be used for illicit purposes.
Best practices: Avoid Query String in Sensitive Data | Implement Secure Data Storage | Securely Store Data in RAM
M3 – Insecure Communication
Insecure communication involves failing to protect data in transit, an example of which is sending communications in cleartext.
Best practices: Fully Validate SSL / TLS | Implement Secure Network Transmission of Sensitive Data
M4 – Insecure Authentication
Mobile apps need to securely identify a user, especially when users are calling and sending sensitive data such as financial information. This category includes session management issues, privacy issues related to authentication, and issues where user identification tokens are compromised.
Best practices: Hide Account Numbers and Use Tokens | Implement Enhance / Two-Factor Authentication
M5 – Insufficient Cryptography
Two types of flaws in this category can lead to an adversary gaining access to sensitive information from a mobile app due to insufficient data protection. Vulnerabilities can impact the process behind encryption and decryption and / or the algorithm behind encryption and decryption may be weak in nature.
Best practices: Implement Secure Data Storage | Understand Secure Deletion of Data
M6 – Insecure Authorization
Insecure Authorization, which differs from M4, refers to the failure of a server to properly enforce identity and permissions as stated by the mobile app. While M4 refers to authenticating the user within the app, M6 covers authorizing communication between the app and back end servers. For example, this could occur when a server blindly allows the mobile app to make requests.
Best practices: Implement Proper Web Server Configuration | Properly Configure Server-Side SSL
M7 – Client Code Quality
This category includes risk stemming from vulnerabilities like buffer overflows, format string vulnerabilities, and various other code-level mistakes where the vulnerability allows code to be executed on the mobile device. According to OWASP, bad code can allow attackers to exploit the organization logic and potentially bypass security controls enforced on the device.
Best practices: Avoid Simple Logic | Test Third-Party Libraries | Validate Input from Client
M8 – Code Tampering
Attackers can tamper with or install a backdoor on an app, re-sign it and publish the malicious version to third-party app marketplaces. Such attacks typically target popular apps and financial apps. Developers should employ anti-tamper and tamper-detection techniques to detect and prevent illegitimate applications from executing.
Best practice: Implement Anti-Tampering Techniques
M9 – Reverse Engineering
If an attacker can easily reverse engineer an app, it means they can analyze an app’s source code, libraries, algorithms, and more. With deeper knowledge of an app’s functionality and how it works, an attacker can more easily identify flaws they can exploit.
Best practice: Increase Code Complexity and Use Obfuscation
M10 – Extraneous Functionality
Developers frequently include hidden backdoors or security controls that are useful during the development phase that they do not plan to release to production. When that functionality is accidentally released into the wild, attackers can take advantage of that functionality to compromise an app.
Best practice: Carefully Manage Debug Logs
Going beyond the OWASP MASVS Risks
NowSecure Security Researcher Jake Van Dyke recently shared the following insight in his webinar 5 Things You Must Know to Crush Mobile Security Bugs. He said:
“Lists like the OWASP MASVS or NowSecure’s Secure Mobile Development Best Practices are good checklists. At the same time, many dangers exist outside of these lists that security professionals need to be aware of. Remember, the FBI Most Wanted List contains a lot of bad guys, but others are still out there that law enforcement is looking for as well.”
While the OWASP MASVS doesn’t capture every flaw you need to be fully secure, it’s a powerful, minimum-baseline checklist that can be used as a source document for building a mobile app security program.





