A cyberattack last week held hundreds-of-thousands of computers hostage in 150 countries and forced the U.K. National Health Service (NHS) to redirect patients or delay medical care. Some call the attack a “wake-up call,” and it certainly is. But it’s also an indictment of our current cybersecurity tools and procedures.
Everyone, not just cybersecurity experts, should understand the WannaCry malware attack in order to help prevent such attacks in the future. Below I explain in plain language what happened, how organizations could have prevented this attack and urgent action needed to secure our future.
What happened and why?
In a typical ransomware attack, culprits send e-mails that include a seemingly harmless attachment or website link. Clicking the link or attachment will activate software code that abuses a weakness in other software installed on the targeted computer. At that point, the ransomware is installed and goes to work concealing folders and files on the computer using encryption. The victim is told to pay a ransom if they want to access those files ever again.
In this most recent case, the attackers broke into computers through a weakness in older versions of Microsoft Windows which allowed them to install software that locked up valuable files on the system. Worth noting is that Microsoft had fixed the issue in March but not every organization installed the update, leaving themselves — and the people they serve –vulnerable to attack.
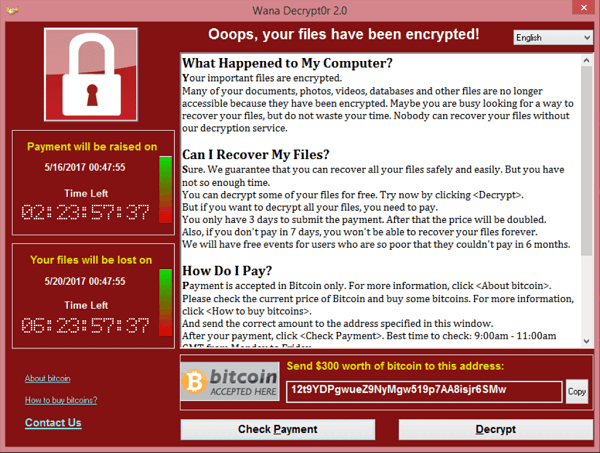
Motivated by profit, the perpetrators forced victims to pay a ransom in order to regain access to the files on the infected computers. The software displayed a screen with instructions on how to pay approximately $300 to unlock the files, a fee that increases as time passes. So far, it’s been reported that the attackers have collected approximately $80,000 in payments. That’s not exactly peanuts, but it hardly seems worth the danger of denying or delaying medical care or other critical services to people that need them.
So what can you do about it?
For large organizations, installing updates across their entire network can be arduous. But, the update process is less painful and risky than the ramifications of an attack that denies service to patients and customers.
Here are some actions you can take:
- Teach employees how to recognize phishing e-mails
- Install updates as soon as they’re available
- Stay on top of the latest threats by following security alerts such as those from the United States Computer Emergency Readiness Team
What does the future hold?
Wireless medical devices that monitor patient health or Internet-connected implantable and wearable devices may also contain security flaws vulnerable to attack. Thankfully, no deaths have been reported thus far as a result of this most recent ransomware attack. However, the attack serves as an example of the insecurities lingering in health care and other critical industries and demonstrates that there is money to be made exploiting those shortcomings. When attackers can blackmail a health care organization because they hold life-sustaining technologies hostage — how can that organization refuse to pay?
The entire world is going mobile and while both individuals and organizationes benefit from this trend, mobile technologies create opportunities for criminals. Employees use a wide variety of mobile devices, operating systems and apps, which makes it even more difficult for employers to ensure everyone’s devices and apps are up-to-date and secure against criminals’ latest attack techniques. At NowSecure we test the security of mobile apps and their interactions with mobile devices and networks. And while mobile app development and usage skyrockets, we’re not seeing sufficient investment in making sure those apps are secure.
As we look to our ubiquitous mobile future, we must acknowledge the mobile security gap and recognize that continued underinvestment puts not only organizations, but all of us, at risk.