Who’s listening? Mobile app privacy lessons from the Bose Connect lawsuit
Posted by NowSecure Marketing
Manufacturers of wireless devices that connect to phones and tablets via companion apps should take note of a recent lawsuit related to mobile app privacy. The suit alleges that Bose, a manufacturer of audio equipment, has violated the Wiretap Act and other state laws by collecting data about the audio files users listen to through headphones that pair with the Bose Connect mobile app. This and other recent litigation makes an example of enterprises that probably should have spent more time discussing security during product development and design.
Mobile app privacy and collecting user data
The Wiretap Act (18 U.S.C. §§ 2510-2522) prohibits the interception and disclosure of “wire, oral, or electronic communication” using any “electronic, mechanical, or other device” except where the act allows for it (e.g., when a communications provider needs to do so to render services). The class action complaint alleges that the Bose Connect app records the contents of electronic communications sent to and from the app, a user’s mobile app, and a user’s Bose headphones.
The plaintiff claims that data collected about a user’s audio selections — music, Podcasts, etc. — can identify that user’s age, political beliefs, religious affiliation, medical conditions, and more. The complaint wants an injunction to stop Bose from collecting, transmitting, and disclosing (to a third party data-mining company) users’ audio selections and seeks damages related to the invasion of users’ privacy and the purchase of associated Bose products.
Those of you familiar with the fact that security flaws afflict a great many mobile apps out there might ask what makes the case of Bose Connect different from any other leaky app. The reason is, it suggests that consumers are feeling more empowered to take action against enterprises they deem negligent in protecting mobile data. The allegations against Bose are just one more example in recent months of consumers, and lawyers, holding accountable companies that potentially violate personal privacy via mobile devices, mobile apps, and paired technology.
We mentioned another suit related to a wireless device and mobile app pairing allegedly violating consumers’ privacy in one of our #MobSec5 mobile security news digests last month. The We-Connect mobile app that connected with We-Vibe massage devices sent user data including date and time of use along with e-mail addresses registered with the app account to company servers without users’ consent.
I don’t think Standard Innovation Corporation, the manufacturer of We-Vibe devices, collected this data with malicious intent — nor do I think Bose did. But in the end, it didn’t matter for Standard Innovation. The settlement will cost the company $3.75 million dollars.
Prioritize mobile app privacy and security in product development
I’m not shaking my fist and grumbling that product and development teams should stop innovating. I’m just reminding them not to let shiny new products and features distract from privacy and security considerations. I’m suggesting that security representatives receive an invitation to even early-stage development discussions. Developers, product managers, and the enterprise as a whole all need to think about user privacy and security throughout the product lifecycle — from inception to launch through end-of-life.
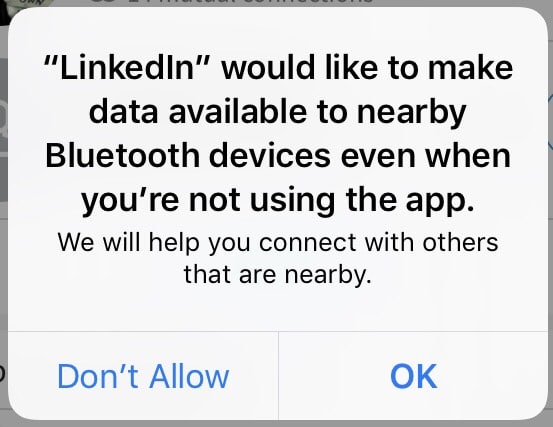
Just this morning someone commented on another potential example of starry-eyed enthusiasm over a new app feature outshining security concerns. In the image below, you see a screenshot of a permissions request from the LinkedIn app for iOS. The LinkedIn team is probably really excited about providing additional ways for users to connect with each other. But what data will the app make available as a result of this feature, and does the feature open up an avenue for adversaries to connect with victim’s devices? Just because you can do something doesn’t always mean you should do it.
In the cases of both Bose and We-Vibe, it’s possible a security delegate would have expressed concern about the collection and transmission of user data. Had security entered the conversation earlier, I think a debate could have ensued about whether the data collection is necessary and what relevant laws, regulations, and security best practices it might violate.
Mobile app privacy mistakes can cultivate a target for attackers
You might not consider $5 million, at a minimum what the Bose lawsuit says the case is worth, or $3.75 million, the We-Vibe settlement, significant legal penalties. But, I suspect we’ll see more and more of these class action suits as consumers become more aware of just how much personal data their mobile devices and the apps they use collect about them.
And even if legitimate companies are not outright selling consumers’ personal data, I start to think about the recently revealed Yahoo breaches and whether companies are simply creating juicy caches of data for attackers to pilfer. I’m not denying the value of “big data” for improving the customer experience and machine learning, for example. It’s just important for enterprises to make sure they’re protecting that data and that the value they gain outweighs the value miscreants might see in getting their hands on it.
What I hope you’ll take away from this post and these incidents is inspiration to conduct security assessments of mobile apps you market or develop — especially if the app pairs with some sort of connected device. You could save yourself significant time and money avoiding legal fees and damage to your reputation. You may not even be aware of the user data your app stores or transmits.
NowSecure believes strongly that the best time to start thinking about security is at the beginning of a mobile app, or any, development project. This is why we sponsor groups such as Security By Design and publish free resources like our Secure Mobile Development Best Practices, Mobile App Security Program Management Handbook, and Evaluation Guide for Mobile App Security Testing.




