Cloudflare ‘Cloudbleed’ bug impact on mobile apps: Data sample of potentially affected apps
Posted by David Weinstein
Today, Google’s Project Zero team published details of a bug that causes Cloudflare reverse proxies to dump uninitialized memory. People are beginning to call the bug “Cloudbleed.” This is a big deal, and the Cloudflare Cloudbleed bug affects mobile apps.
What is the Cloudflare Cloudbleed bug?
According to a Cloudflare incident report, the bug affected “e-mail obfuscation, Server-side Excludes and Automatic HTTPS Rewrites,” which means it impacted a wide spectrum of customers and services. Some 2 million websites on the Cloudflare network may be affected. Some of the leaked data includes HTTP headers related to basic authorization, OAuth tokens, usernames, and passwords!
How does the Cloudbleed bug affect mobile apps?
Mobile applications are potentially impacted because in many cases they are designed to make use of the same backends as web browsers for content delivery and HTTPS (SSL/TLS) termination. Users on Hacker News have confirmed the presence of HTTP header data for apps such as Discord, FitBit, and Uber by searching through search engine caches with targeted search terms.
“The bug was serious because the leaked memory could contain private information and because it had been cached by search engines,” which is chilling. This issue is possibly worse than the Heartbleed bug because this time the leaked data has been cached throughout the Internet (or “sprayed into caches all across the Internet,” as one Hacker News commenter put it) by various search engines including DuckDuckGo, Baidu, and Google throughout the lifetime of the bug. Search engines constantly crawl the web and Cloudflare customer data leaks would be part of the data the engines cache.
What should I do about the Cloudbleed bug?
Due to the cached data, cleaning up the mess may, unfortunately, take quite a while. If I were responsible for a service that has ever used Cloudflare, I would scour the web right now to proactively search for leaked authentication tokens and user credentials before the rest of the Internet makes use of them. Once I identified that leaked information, I’d be sure to terminate related sessions and require password changes for affected accounts.
Data sample including potentially affected mobile apps
Interestingly, as part of our mobile app security testing and the NowSecure Intelligence engine that powers our mobile app reputation service, we collect dynamic analysis data for hundreds of thousands of popular apps from the Google Play and Apple App Store. I ran a quick query to see what iOS apps use Cloudflare services and may have been impacted by this bug. So far, researchers have identified leaked data associated with the FitBit Android, Uber, and Discord apps. Below is a screenshot with detailed information from our engine.
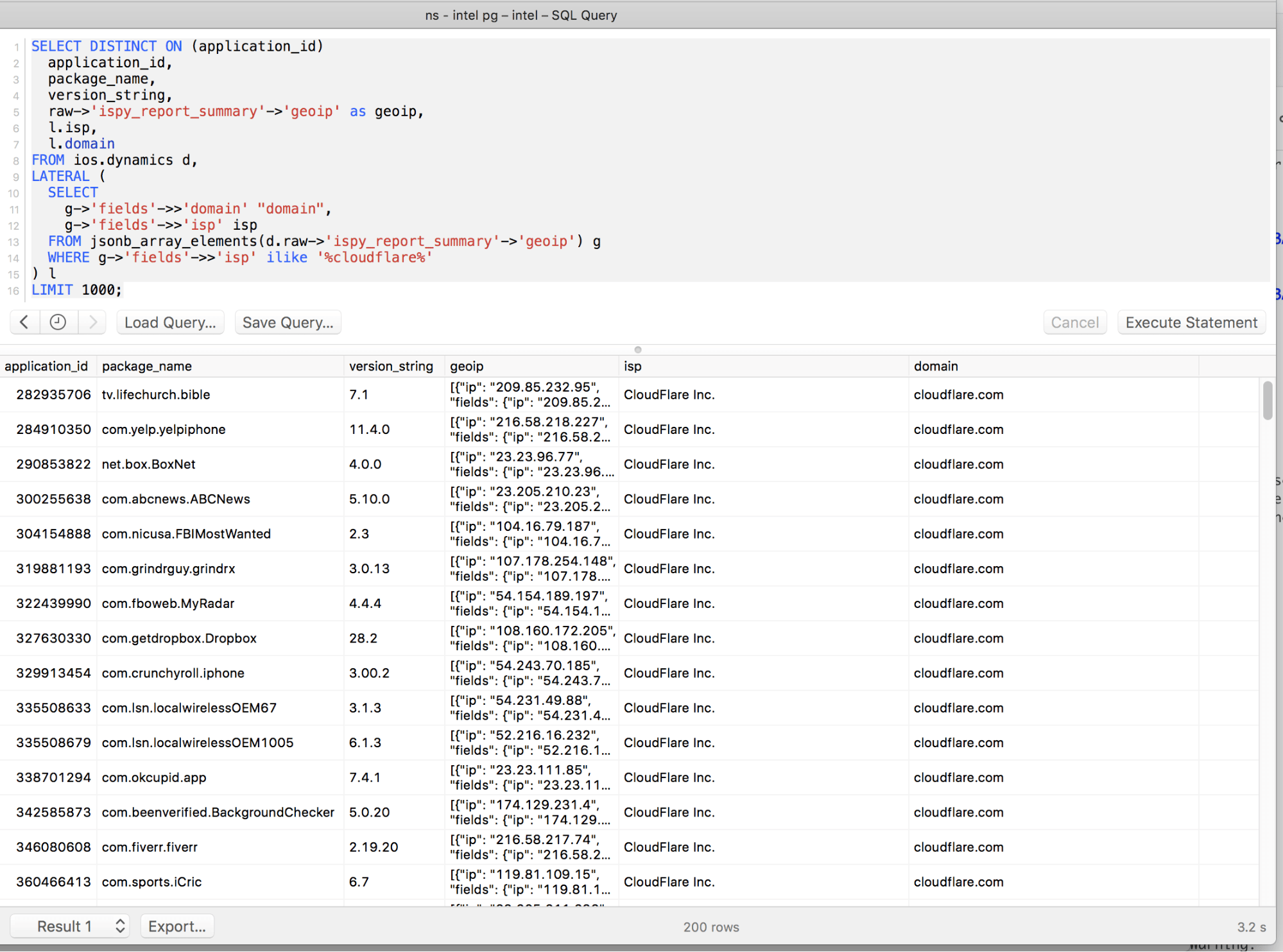
List of potentially affected iOS apps
Below is a list of 200 iOS apps that I’ve identified as using Cloudflare services from a sampling of approximately 3,500 of the most popular apps on the app store (about five percent of the popular free apps we sampled), and we recommend users take precautions, proactively resetting passwords or otherwise monitoring account activity closely as cleanup is underway.




