Samsung Account and GALAXY Apps Technical Breakdown – CVE-2015-0863 and CVE-2015-0864
Posted by Jake Van Dyke NowSecure Marketing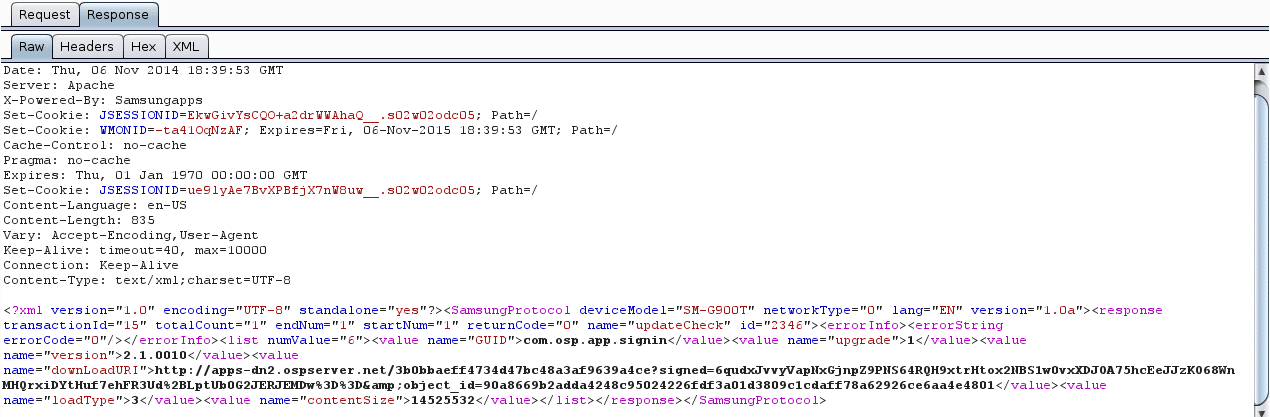
Last year, NowSecure mobile security researchers Ryan Welton and Jake Van Dyke discovered two major vulnerabilities affecting nearly 80% of Samsung Android devices, including flagship Galaxy S5 phones. We provide a high-level summary of the issue in our article Corrupdate: Samsung patches flaw discovered by NowSecure.

Nicknamed Corrupdate due to the attack vectors described below, the vulnerabilities were discovered in Samsung Account and Samsung GALAXY Apps, and put users at risk of data loss or system attack. When exploited, an adjacent network attacker could replace an app update with their own malicious apk.
In this blog post we walk you through the exploit, describe the security impact, and provide recommendations on how to protect yourself.
NowSecure reported these issues to Samsung to help them create a patch and ensure users would be protected. Patched versions have been created and deployed by Samsung, and some users have received updates, while others must take steps on-device to update these apps. Users can find out if they are vulnerable following instructions below, or by installing the free NowSecure Mobile for Android app.
The vulnerabilities have been assigned CVE-2015-0863 for GALAXY Apps (com.sec.android.app.samsungapps) and CVE-2015-0864 for Samsung Account (com.osp.app.signin).


System Application Vulnerabilities
System applications can contain vulnerabilities that affect the privacy and security of a userUs device. These apps are frequently installed by the device manufacturer or the cellular carrier. Users cannot uninstall these applications (even if they choose not to use them), leaving potentially vulnerable apps on their device. Like any application, system apps require a routine update process, which in this case we found vulnerable to attack.
Samsung Account and GALAXY Apps (also called Samsung Apps and Samsung Updates on some versions) are susceptible to Man-in-the-Middle attacks, putting users at risk of having their data accessed and manipulated by attackers. The vulnerability discussed here allows an active network attacker to replace an update to an application with the attackerUs own app. The malicious app can then request permissions it would like and manipulate the device to its full potential.
The Damage
In all of our tests, the Samsung Account app did not install any app without the userUs permission. The user is prompted when this app retrieves any update, and the user must confirm for the updated app to be installed – whether genuine or malicious.
The GALAXY Apps market, on the other hand, DOES install applications without user consent, and in our testing the store tried to automatically install some other Samsung apps (Samsung IAP, Samsung Billing). On an insecure network, this exposes the user to having a malicious application installed without their knowledge or intervention. Due to the installation without approval, the GALAXY Store vulnerability rates as a higher risk.
One limiting factor on the attack is that, once installed, the malicious application can only execute after the user has run the app at least one time. However, once the malicious app does start, it can do anything that any other app can do, including data theft and attempts at privilege escalation. For example, it can send your contacts off to a foreign country, track your location, display ads, open a reverse shell back to the attacker, mine bitcoins, etc. An attacker could name their app to mimic a popular user app, in order to trick the target into executing their malicious app.
In our testing we were able to exploit both Samsung Account and GALAXY Apps and install an app containing a root exploit as a proof of concept.
User Recommendations
CHECK IF YOU ARE VULNERABLE
Because these are system apps, they cannot be uninstalled by the regular user nor updated through Google Play. Samsung has published updates to both apps and users can check the versions on their device in the Application manager under Settings. Access the Application manager by navigating to Settings > More > Application Manager, Settings > General > Application manager or Settings > Application manager, depending on device model and Android version. Under ALL, locate Samsung Account and GALAXY Apps (which may also be called Samsung Apps or Samsung Updates). When the app is selected, the App info screen shows the Version number.
The patched versions of these apps are as follows, meaning any versions LOWER than these are vulnerable.
- Samsung Account: version 1.6.0069 or later (1.0 series), Version 2.1.0069 or later (2.0 series)
- GALAXY Apps (aka Samsung Apps or Samsung Updates): version 14120405.03.012 or higher
Rather than checking versions manually, users can install NowSecure Mobile to be alerted if their device is vulnerable.
UPDATE THE APPS In order to update these apps the following user actions may be required according to Samsung.
NOTE: Due to the nature of the vulnerability, the updates should be performed as soon as possible, but only on a trusted secure network such as home wi-fi.
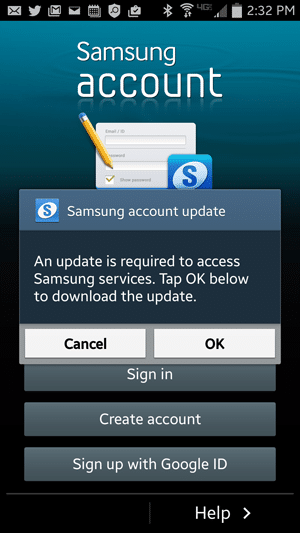
- Samsung Account: Open any Samsung Apps which require Samsung Account login. You will be prompted to download the latest version of Samsung Account, as shown below.
- Galaxy Apps issue: Open Samsung Apps, go to “settings”. You will be prompted to download the latest version as shown below. This action will change name of the Samsung Apps to Galaxy Apps. Though they are different name, they use same version scheme.
 TURN OFF THE APPS For users who have not received udpates or want to block these apps from running, it is possible to disable the apps. Although they cannot be uninstalled, the Application manager offers the option to RTurn offS the affected apps, which will prevent exploit of this vulnerability. See above for where to access Application manager.
TURN OFF THE APPS For users who have not received udpates or want to block these apps from running, it is possible to disable the apps. Although they cannot be uninstalled, the Application manager offers the option to RTurn offS the affected apps, which will prevent exploit of this vulnerability. See above for where to access Application manager.
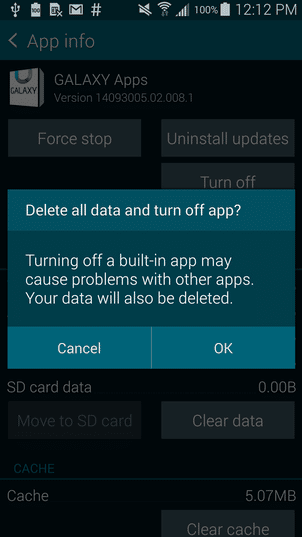
If you click Turn Off the system will prompt you to confirm RDelete all data and turn off appS as shown in the screenshot below. You can accept the following warning by clicking OK.
When disabled these apps will not attempt to retrieve updates insecurely. However, it is important to note that with GALAXY Apps disabled other Samsung apps may not be updated, which could prevent updates that fix other issues.
Exploit Walkthrough
These two apps pre-installed on Samsung Phones were tricked by a network attacker into installing a new malicious app. The new app can masquerade as a popular app, and if the user runs the malicious version, it can do anything any other app can do.
Periodically, Samsung Accounts will send off requests and see if it needs to update.
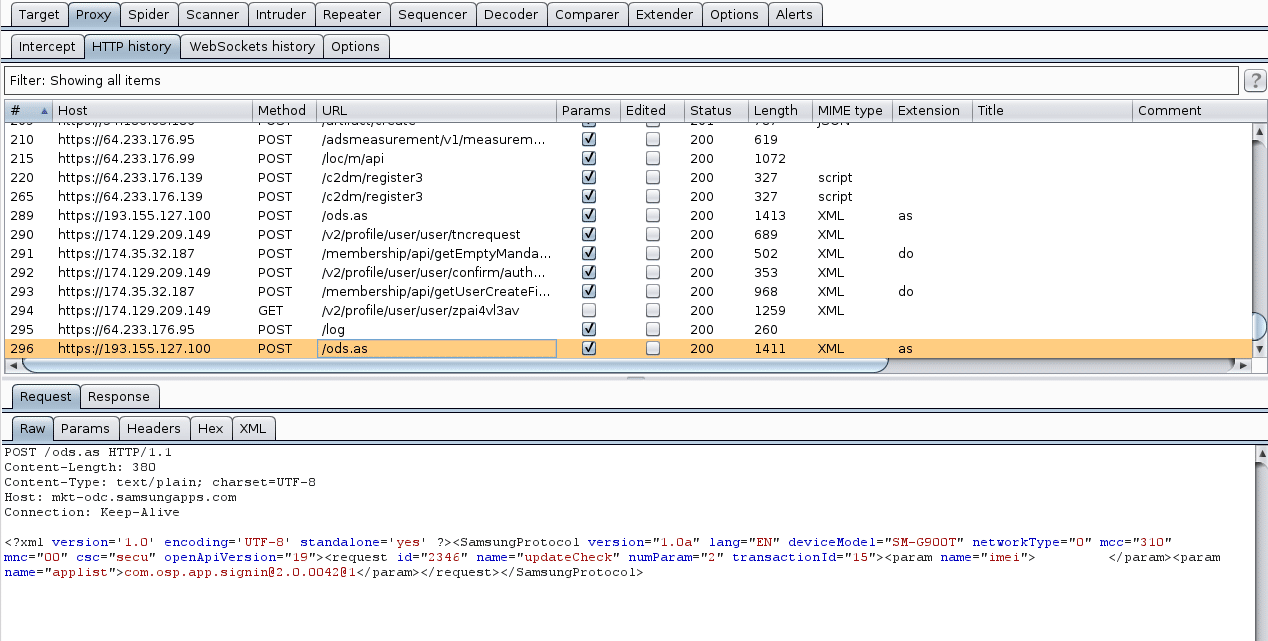
If there is an update, the server will respond with something like this. The http://apps-dn2.opserver.net/ url seen in this screenshot is the source of the update.

On the phone, the user is prompted in the notification tray that there is an update available.
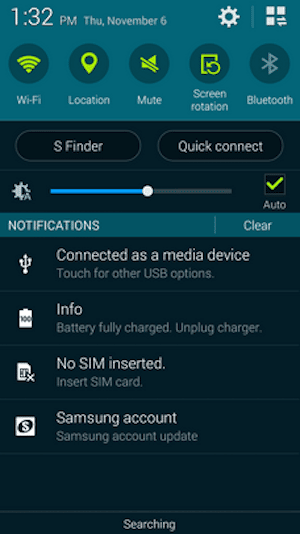
Once the user clicks this notification and accepts the update, the app will attempt to download the URL it received.
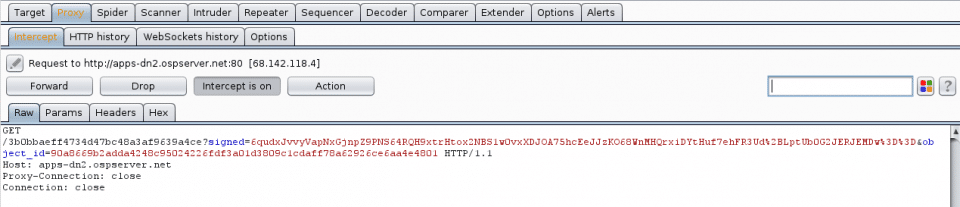
And it will receive back the plaintext apk (zip file).
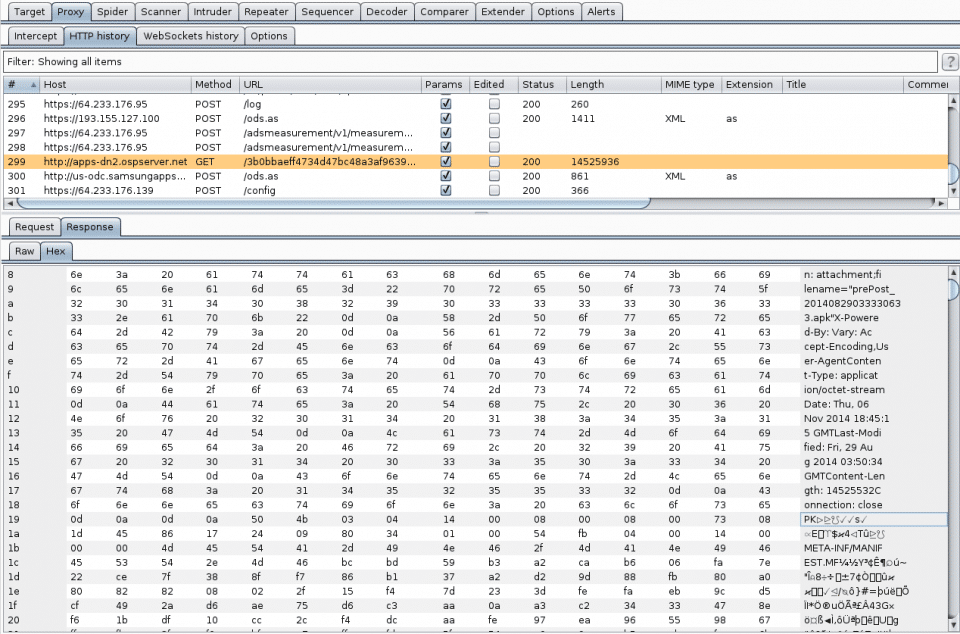
The GALAXY Apps store works in a similar fashion. It downloads APKs in plaintext via http://apps-dn2.opserver.net/. We did come across some constraints with the file size (on some devices) for replacement apps that would limit an attacker. But the window is fairly flexible and we were able to trick both the Samsung Account and GALAXY Store apps into installing a version of towelroot to root the device as a proof of concept.
Detection and Disclosure
Below are the versions of the apps where the issue was discovered and tested, using the Galaxy S3 (Sprint), Galaxy S5 (T-Mobile), and Galaxy Note2 (International). Samsung has since confirmed the vulnerability exists on numerous versions of the apps across many devices.
GALAXY Apps (aka Samsung Apps or Samsung Updates) package: name=’com.sec.android.app.samsungapps’ versionCode=’4210080′ versionName=’14040104.21.008.0′ sdkVersion:’7′ targetSdkVersion:’16’ application-label:’Samsung Apps’
Samsung Account package: name=’com.osp.app.signin’ versionCode=’200042′ versionName=’2.0.0042′ application-label:’Samsung account’ application-label-ca:’Samsung account’
Disclosure Timeline 2014-07-31 Notified vendor of Samsung Accounts vulnerability 2014-08-21 Second notification to vendor requesting response 2014-08-25 Response from vendor requesting more information 2014-08-26 Additional details provided by NowSecure 2014-08-27 Vendor requested extension of disclosure 2014-08-29 Vendor confirmed vulnerability 2014-09-03 Vendor requested extension for patch development & distribution 2014-12-04 Vendor began patch distibution 2015-01-26 NowSecure disclosure





