This is a cross-post from Sebastiàn Guerrero’s original post on Jetdirect vulnerabilities, translated to English.
A few weeks ago, I had the opportunity to test various printer models in order to better understand how they function. The tests revealed some interesting bugs worth sharing.
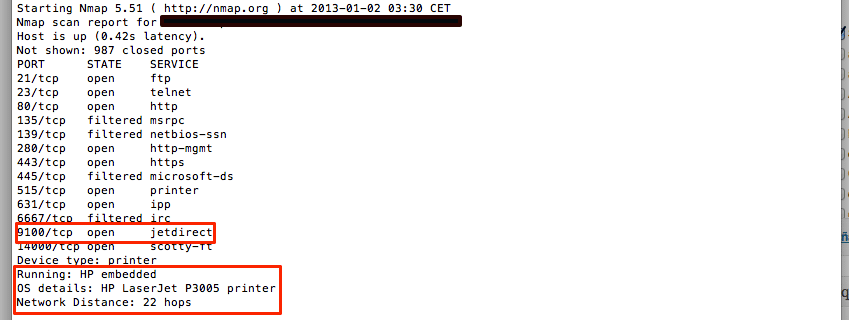
Today, most printers on the market make use of JetDirect technology. Designed by HP, it allows these devices to easily attach directly to a local area network, allowing the printer to be visible and accessible to other devices and/or users connected to the same network segment. When we want to print file, we only have to send it to the print queue and seconds later collect our hard copy printout.
But how does the process really work?
The JetDirect protocol is used to first establishes communication with the printers waiting to receive the data stream.
Along with the content to be printed, in the format required by a file extension, JetDirect adds additional information that is parsed and interpreted by the printer.
For our purposes, it is sufficient to know the following terms:
- UEL (Universal Exit Language ) – Command used at the beginning and end of each data stream sent to the printer. The syntax is represented as %-12345X , where ESCape can be represented by 0x1B.
- PJL (Printer Job Language ) – Used to tell the printer what action to take. It serves as additional support for the PCL.
- PCL (Printer Control Language ) – Basically a language used to format pages. Although it may seem harmless, it can be used to exploit vulnerabilities in most parsers and interpreters.
As always, for a more detailed and accurate information, please read the specifications provided by each language:
- PJL / PCL Printer Language Technical Reference – Part I
- PJL / PCL Printer Language Technical Reference – Part II
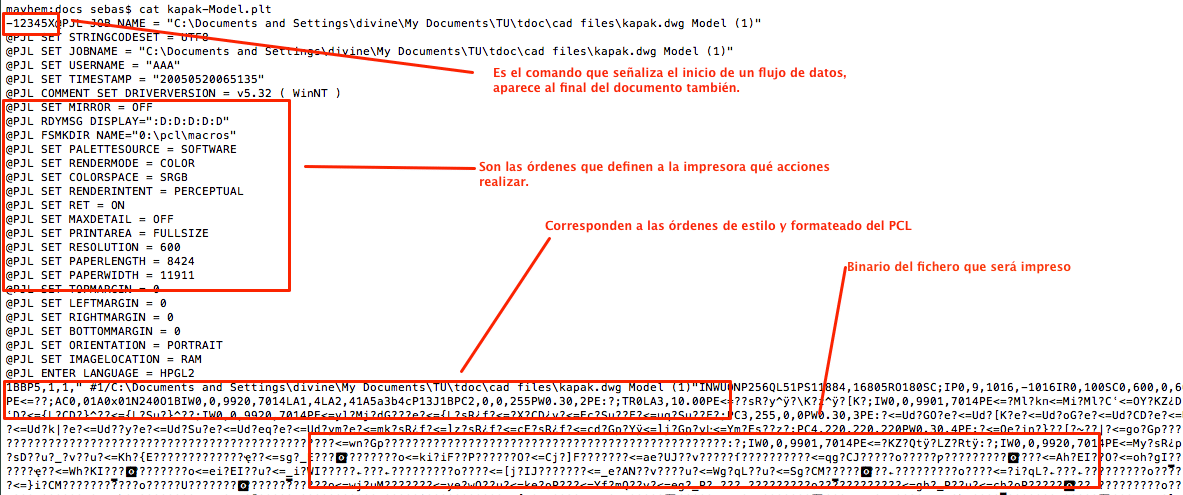
Here’s what a typical print job might look like:
As you may have guessed, by infusing tags parsed and used by interpreters of PCL / PJL, an attacker could trigger persistent denial of service affecting a large percentage of models and manufacturers.
Why attack a printer?
When considering threats to their computer infrastructure, most companies donÍt really consider the risks that printers may pose. Especially as many feel they are safeguarded by fingerprint access, PINs, passwords, smartcards and so on. But consider that all the heavily encrypted documents a company have on their computers are automatically unprotected once sent to the print queue and are reflected and stored in the history. What if attackers had control or direct access to that record and could use the internal memory to re-print previous jobs?
When we consider the the long list of manufacturers whose printers may have security vulnerabilities _ Canon, Fujitsu, HP, Konica Minolta, Lexmark, Xerox, Sharp, Kyocera Mita, Kodak, Brother, Samsung, Toshiba, Ricoh, Lanier, Gestetner, Infotek, OCE, OKI _ and look at the number of units theyÍve sold in recent years, the magnitude of the issue because strikingly clear.
Disclaimer: I am not responsible for the application of this information, and for that matter, I do not name any brands or models specifically. The results returned by the failures may vary by manufacturer or model, as well as the firmware version installed.
Vulnerability I _ Bypassing authentication processes
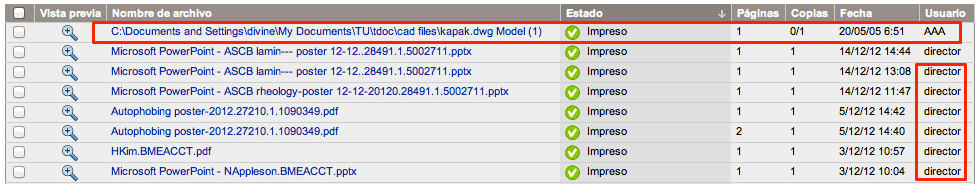
Many new printer models incorporate authentication mechanisms to control which users have access to them. A company can view the number of copies made by each user, what documents have been printed, and so on. Every time an employee wants to print a job they have to unlock the device, or enter their domain credentials.
But this whole process can be skipped by making a direct connection to the port or sending content to print:
The result:
If we analyze the document sent to print, we see two rather curious labels:
1 @ PJL SET JOBNAME = "C: Documents and Settings Divine My Documents TU TDOC cad files kapak.dwg Model (1)" 2 @ PJL SET USERNAME = "AAA"
Vulnerability II – Assigning work to system users
Taking advantage of the vulnerability above, an attacker can modify their values to assign labels to the Director occasional printed job.
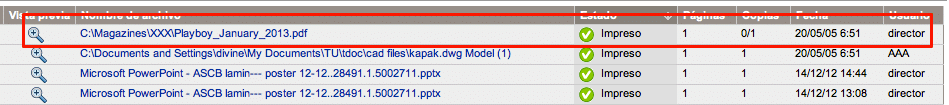
Thus, in addition to printing restrictions skipping, an attacker can assign the copies to any other user, thereby increasing the counter.
Vulnerability III – Generating denial of service
As demonstrated above, the printed files sent includes information that determines its style, formatting and actions that the printer has to notice. These values are parsed and interpreted by the printer, so that if we introduce a value not expected or desired, it may cause the printer to cease to be functional.
In our case, letÍs focus on labels PCL, and use the following formatting portion:
As a reference we can use: PCL Printer Commands besides this file macros
1 ^[&l7H^[&l-1M^[*o5W^M^C^@^G^[*o-2M^[*o5W^M^B^@^@^A^[*o5W^K^A^@^@^@^[*o5W^N^C^@^@^E^[*o5W^N^U^@^@^@^[&l110A^[&u600D^[*o5W^N^E^@^S`^[*o5W^N^F^@^[g^[*r4724S^[*g12W^F^_^@^A^BX^BX
Here’s what we can we conclude from this: * **g # W** – ” Configure Raster Data Command ” followed by a number of configuration bytes ( # – in this case, 5 ), set parameters such as color depth, vertical and horizontal resolution, etc. * **o # W** – ” Configure Driver Command “, also, is followed by a specified number of bytes of settings ( # – in this case 12 ), is used to execute instructions specific printer, which can be found in the Configuration Sheet specifications for each printer. * **& L7H** – Determines the source of the paper, in this case set to automatic. * **& L-1M** – Media Type Bond * **& L110A** – Corresponds to the macro PCL_JENV_CHOU3 that defines the height of the paper. * **& U600D** – Indicates the number of units per inch PCL. At this point, if you modify any of these parameters by inserting an unexpected character, depending on how it is implemented by the parser and interpreter for the specific printer model, you may cause denial of service, knocking printers offline and forcing them to be reset manually: 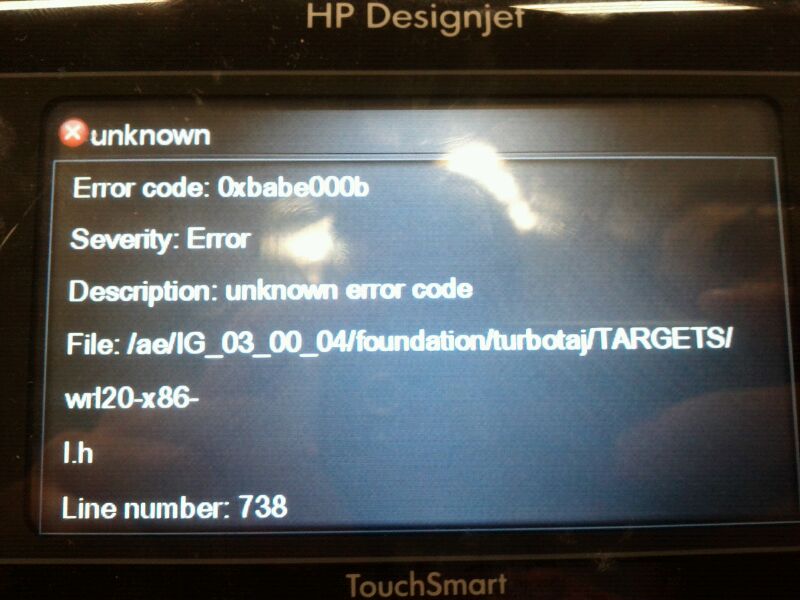 #### Vulnerability IV – What is your name? One of the peculiarities presented by these new models is the inclusion of a screen “TouchSmart” whereby you can interact directly with a few settings on the printer, or in other cases obtain and display configuration information. Among available information to change is the name the FTP service which uploads scanned jobs for those multifunction printers:
#### Vulnerability IV – What is your name? One of the peculiarities presented by these new models is the inclusion of a screen “TouchSmart” whereby you can interact directly with a few settings on the printer, or in other cases obtain and display configuration information. Among available information to change is the name the FTP service which uploads scanned jobs for those multifunction printers: 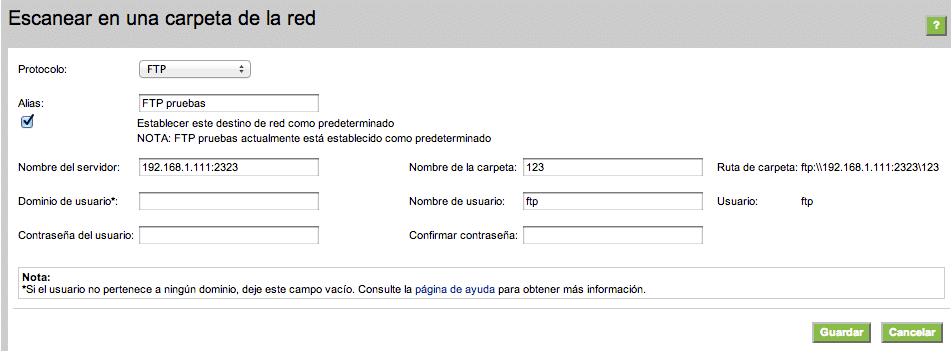 While the number of characters entered is limited and controlled by JS, once an attacker has intercepted the request, they could enter something like:
While the number of characters entered is limited and controlled by JS, once an attacker has intercepted the request, they could enter something like:
1 perl-e ‘print “A” x1000’
2 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
In this case, the printer was bricked and had to undergo a USB hard reset by re-installing the firmware.
The examples above represent just a few of the printer vulnerabilities that can be exploited for denial of service attacks-of perhaps greater worry to companies might be data theft that could easily occur on printer devices that store sensitive information. As such, its imperative that companies don’t fail to take into account their printing devices when considering their overall risk profile.