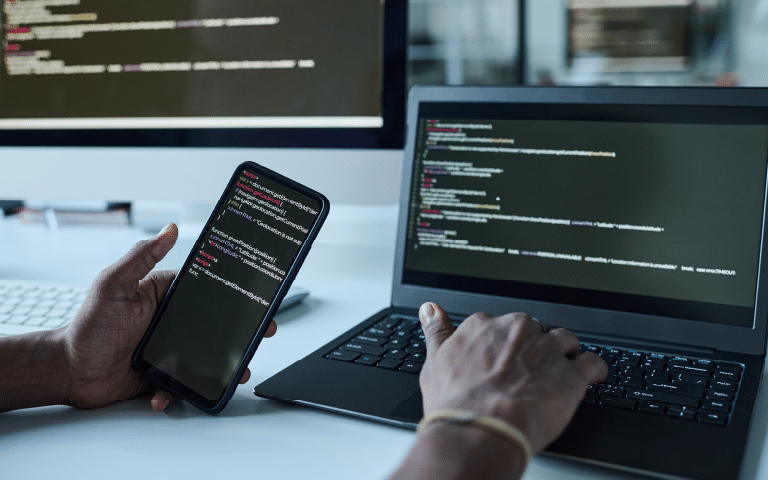
NOWSECURE NOW AVAILABLE IN THE MICROSOFT AZURE MARKETPLACE
Microsoft Azure customers gain access to NowSecure Mobile App Security and Privacy Testing for scalability, reliability, and agility of Azure to drive mobile appdev and shape business strategies.

NOWSECURE NOW AVAILABLE IN THE MICROSOFT AZURE MARKETPLACE
NOWSECURE NOW AVAILABLE IN THE MICROSOFT AZURE MARKETPLACE
Show More