Health care and mobile man-in-the-middle risks: Guidance for HIPAA-covered entities
Posted by Brian Lawrence NowSecure Marketing
Last week the U.S. Department of Health and Human Services (HHS) warned of security products that inspect HTTPS traffic potentially exposing Protected Health Information (PHI) via man-in-the-middle (MITM) attacks. The warning focuses on HTTPS interception products that decrypt, inspect, and re-encrypt web traffic. There’s also, however, a mobile MITM vector that HIPAA-covered entities need to be wary of. The paper cited in the alert explains that a number of these security products also intercept mobile traffic. As more healthcare organizations take advantage of mobile devices and apps to deliver better services, I wanted to highlight the mobile MITM vector for health care organizations and offer some tips for developers as they set out to develop HIPAA-compliant mobile health apps.
Man-in-the-middle attacks on the health care industry
The HHS warning came as a result of a recently published paper examining the use of HTTPS interception tools. The paper found that 62 percent of connections through such HTTPS inspection products — or “middleboxes” — had their security downgraded, and an alarming 58 percent inherited “severe vulnerabilities.” HHS enforces the Privacy and Security Rules of the Health Information Portability and Accountability Act (HIPAA). When the agency warns HIPAA-covered entities of software vulnerabilities and potential cyber attacks, those organizations ought to take note.
The warning focuses on the dangers of HTTPS interception products designed to inspect network traffic for malware. The mechanics of the products’ functionality might actually make network connections less secure, and vulnerable to MITM attacks. MITM attacks take many forms and are difficult to detect because there’s usually no trace left to indicate that information has been exposed.
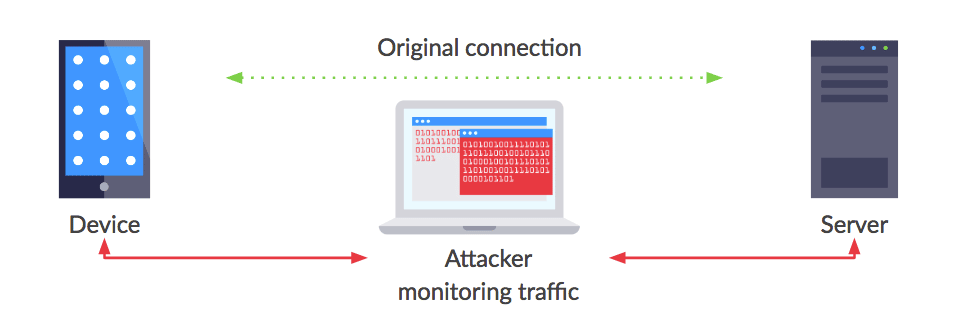
MITM attacks consist of a third party intercepting the communications between two parties – say, a mobile health app and a database full of PHI. A malicious individual may execute an MITM attack to eavesdrop on or manipulate those communications to cause harm or bypass other security measures on either side of the connection.
These attacks can be particularly devastating for health care entities who need to comply with HIPAA. Yes, there’s the potential for PHI exposure. But in addition, such a breach is difficult to detect, and so the entity may only become aware of the breach after it’s too late — after pilfered data is published on the internet.
MITM attacks, mobile health apps, and HIPAA-covered entities
Mobile apps often are the front-end for much deeper enterprise architecture, making the MITM potential impact even greater. A compromised connection between a mobile app and an enterprise’s network infrastructure can affect not only the compromised user, but the entire IT organization that supports the app. Recently Quest Diagnostics found this out the hard way when a vulnerability in their mobile app exposed over 34,000 patient records. Attackers leveraged the mobile app to expose an entire database.
In addition to large-scale data compromise, a successful MITM attack could allow an adversary to read and modify the data sent between the parties, potentially affecting every user connected to the app. For example, the data flowing to doctors, hospitals, and medical devices could be altered in transit. And worst of all, the MITM attack could occur without either party’s consent or knowledge, meaning the breach might not be discovered until it was too late.
How to protect mobile health apps against MITM attacks
In order to help protect PHI from a MITM attack, the HHS alert lists two items relevant to developers of mobile apps.
- Mobile app developers need to implement secure transmission of sensitive data and ensure they use an up-to-date version of transport layer security (TLS). They should use TLS 1.1 or better and not use deprecated protocols such as TLS 1.0 or SSL, which have known vulnerabilities.
- Mobile app developers need to implement certificate pinning. Most mobile health apps use certificate validation to secure communications, but a good second layer of protection is certificate pinning.
Certificate-pinning is a method by which the specific certificate for a back-end server is hard-coded into an app. This results in the app only connecting with a server that presents the hard-coded certificate, preventing the app from connecting with an impersonator. This provides a second layer of defense against a MITM attack, resulting in a significant decrease in the possibility of a breach of PHI.
With the HHS warning about the expansion of vectors for MITM attacks, it’s imperative that mobile health app developers take every step possible to ensure that PHI stays protected.
For more information about the dangers of mobile MITM attacks and how to protect against them, join NowSecure for a webinar on June 13 entitled – “Cutting out the middleman: Mobile man-in-the-middle attacks and prevention.”





